Security
Insidious Ransomware Gang Exploits Employee Monitoring Software in Cyber Attacks

The Abuse of Employee Monitoring Software for Ransomware Deployment
Recent incidents have revealed a concerning trend where threat actors, specifically a member of the Crazy ransomware gang, are exploiting legitimate employee monitoring software and remote support tools to infiltrate corporate networks, evade detection, and prepare for ransomware attacks.
Researchers at Huntress have uncovered multiple breaches where attackers utilized Net Monitor for Employees Professional and SimpleHelp for remote access, camouflaging their activities within normal administrative tasks.
During one intrusion, the attackers strategically deployed Net Monitor for Employees Professional via the Windows Installer utility, msiexec.exe, enabling them to install the monitoring agent directly from the developer’s site on compromised systems.
Once operational, the monitoring tool granted the attackers full interactive access to the victim’s desktop, including file transfers and command execution capabilities.
To ensure persistent access, the attackers employed PowerShell commands to download and install the SimpleHelp remote access client, disguising it with filenames resembling legitimate software like Visual Studio vshost.exe.
The SimpleHelp binary was sometimes hidden under filenames simulating association with OneDrive, such as C:\ProgramData\OneDriveSvc\OneDriveSvc.exe, allowing the attackers to maintain remote access even if the monitoring tool was removed.
Through these tools, the attackers could remotely execute commands, transfer files, and monitor system activity in real-time. They even attempted to disable Windows Defender by halting and erasing associated services.
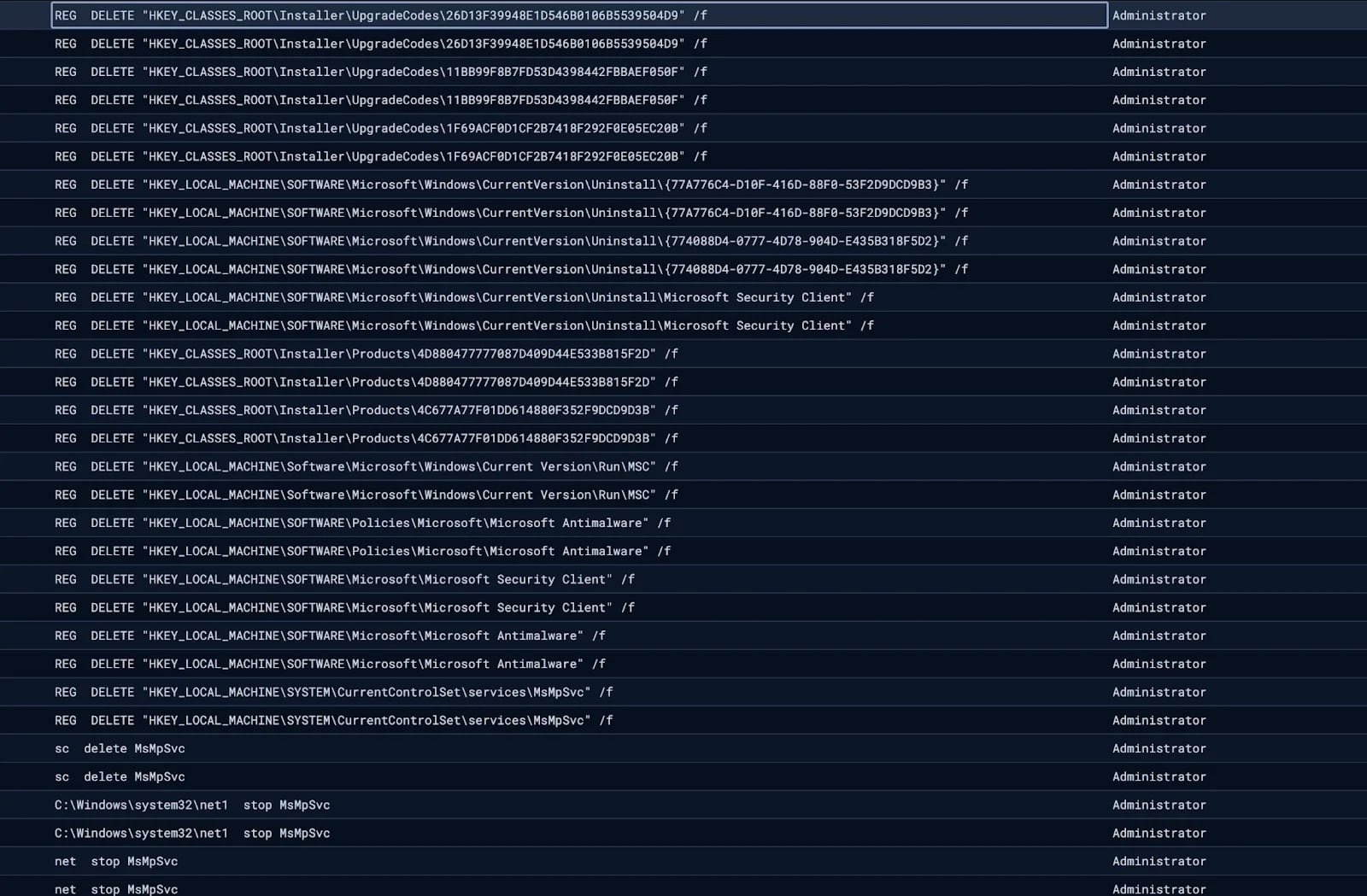
Source: Huntress
In a particular incident, the attackers configured monitoring rules within SimpleHelp to alert them of any activity related to cryptocurrency wallets or remote management tools, indicating preparation for ransomware deployment and potential cryptocurrency theft.
Huntress explains that the attackers monitored keywords associated with cryptocurrency services and remote access tools to detect any suspicious activities on the compromised systems.
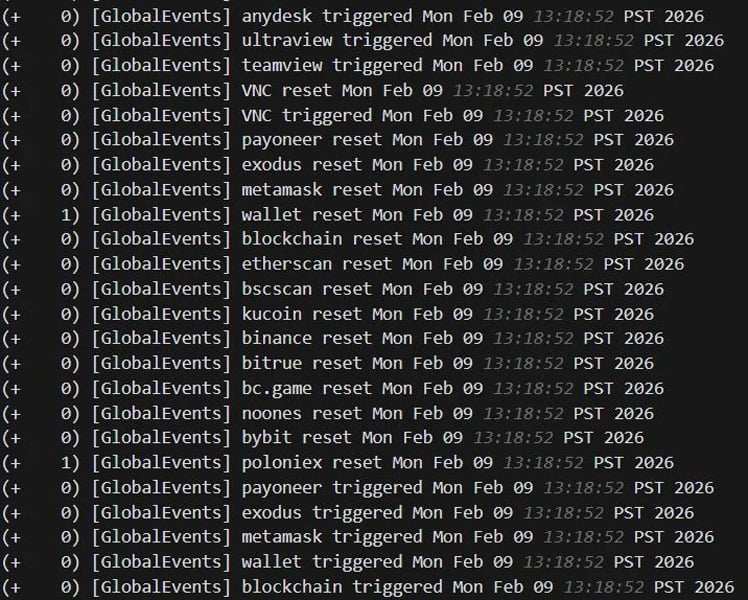
Source: Huntress
By leveraging multiple remote access tools, the attackers ensured continuous access even if one tool was compromised or removed. Although only one incident resulted in Crazy ransomware deployment, Huntress believes the same threat actor is responsible for both intrusions.
Legitimate remote management and monitoring tools are increasingly utilized in ransomware attacks due to their ability to blend in with normal network traffic. Organizations are advised to monitor unauthorized installations of such tools and enforce multi-factor authentication for all remote access services to prevent similar breaches.

Modern IT infrastructure moves faster than manual workflows can handle.
Discover how automated response can reduce delays and enhance reliability in the new Tines guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































