Security
Rampant Cyberattack: Hacker Successfully Breaches 600 Fortinet Firewalls in Just 5 Weeks

Article updated at the bottom with additional technical details about this campaign.
Amazon is warning that a Russian-speaking hacker used multiple generative AI services as part of a campaign that breached more than 600 FortiGate firewalls across 55 countries in five weeks.
A new report by CJ Moses, CISO of Amazon Integrated Security, says that the hacking campaign occurred between January 11 and February 18, 2026, and did not rely on any exploits to breach Fortinet firewalls.

Instead, the threat actor targeted exposed management interfaces and weak credentials that lacked MFA protection, then used AI to help automate access to other devices on the breached network.
Moses says the compromised firewalls were observed across South Asia, Latin America, the Caribbean, West Africa, Northern Europe, and Southeast Asia, among other regions.
An AI-powered hacking campaign
Amazon says it learned about the campaign after finding a server hosting malicious tools used to target Fortinet FortiGate firewalls.
As part of the campaign, the threat actor targeted FortiGate management interfaces exposed to the internet by scanning for services running on ports 443, 8443, 10443, and 4443. The targeting was reportedly opportunistic rather than against any specific industries.
Rather than exploiting zero-days, as we commonly see targeting FortiGate devices, the actor used brute-force attacks with common passwords to gain access to devices.
Once breached, the threat actor extracted the device’s configuration settings, which include:
- SSL-VPN user credentials with recoverable passwords
- Administrative credentials
- Firewall policies and internal network architecture
- IPsec VPN configurations
- Network topology and routing information
These configuration files were then parsed and decrypted using what appears to be AI-assisted Python and Go tools.
“Following VPN access to victim networks, the threat actor deploys a custom reconnaissance tool, with different versions written in both Go and Python,” explained Amazon.
“Analysis of the source code reveals clear indicators of AI-assisted development: redundant comments that merely restate function names, simplistic architecture with disproportionate investment in formatting over functionality, naive JSON parsing via string matching rather than proper deserialization, and compatibility shims for language built-ins with empty documentation stubs.”
“While functional for the threat actor’s specific use case, the tooling lacks robustness and fails under edge cases—characteristics typical of AI-generated code used without significant refinement.”
These tools were used to automate reconnaissance on the breached networks by analyzing routing tables, classifying networks by size, running port scans using the open-source gogo scanner, identifying SMB hosts and domain controllers, and using Nuclei to look for HTTP services.
The researchers say that while the tools were functional, they commonly failed in more hardened environments.
Operational documentation written in Russian detailed how to use Meterpreter and mimikatz to conduct DCSync attacks against Windows domain controllers and extract NTLM password hashes from the Active Directory database.
The campaign also specifically targeted Veeam Backup & Replication servers using custom PowerShell scripts, compiled credential-extraction tools, and attempted to exploit Veeam vulnerabilities.
On one of the servers found by Amazon (212[.]11.64.250), the threat actor hosted a PowerShell script named “DecryptVeeamPasswords.ps1” that was used to target the backup application.
As Amazon explains, threat actors often target backup infrastructure before deploying ransomware to prevent the restoration of encrypted files from backups.
The threat actors’ “operational notes” also contained multiple references to trying to exploit various vulnerabilities, including CVE-2019-7192 (QNAP RCE), CVE-2023-27532 (Veeam information disclosure), and CVE-2024-40711 (Veeam RCE).
The report says that the attacker repeatedly failed when attempting to breach patched or locked-down systems, but instead of continuing to try to gain access, they moved on to easier targets.
While Amazon believes the threat actor has a low-to-medium skill set, that skill set was greatly amplified through the use of AI.
The researchers say the threat actor utilized at least two large language model providers throughout the campaign to:
- Generate step-by-step attack methodologies
- Develop custom scripts in multiple programming languages
- Create reconnaissance frameworks
- Plan lateral movement strategies
- Draft operational documentation
In one instance, the actor reportedly submitted a full internal victim network topology, including IP addresses, hostnames, credentials, and known services, to an AI service and asked for help spreading further into the network.
Amazon says the campaign demonstrates how commercial AI services are lowering the barrier to entry for threat actors, enabling them to carry out attacks that would normally be outside their skill set.
The company recommends that FortiGate admins not expose management interfaces to the internet, ensure MFA is enabled, ensure VPN passwords are not the same as those for Active Directory accounts, and harden backup infrastructure.
Google recently reported that threat actors are abusing Gemini AI across all stages of cyberattacks, mirroring what Amazon observed in this campaign.
Custom AI toolset powers breaches
Separate research published yesterday on the Cyber and Ramen security blog provides additional technical details about how AI and large language models were incorporated directly into the intrusion campaign.
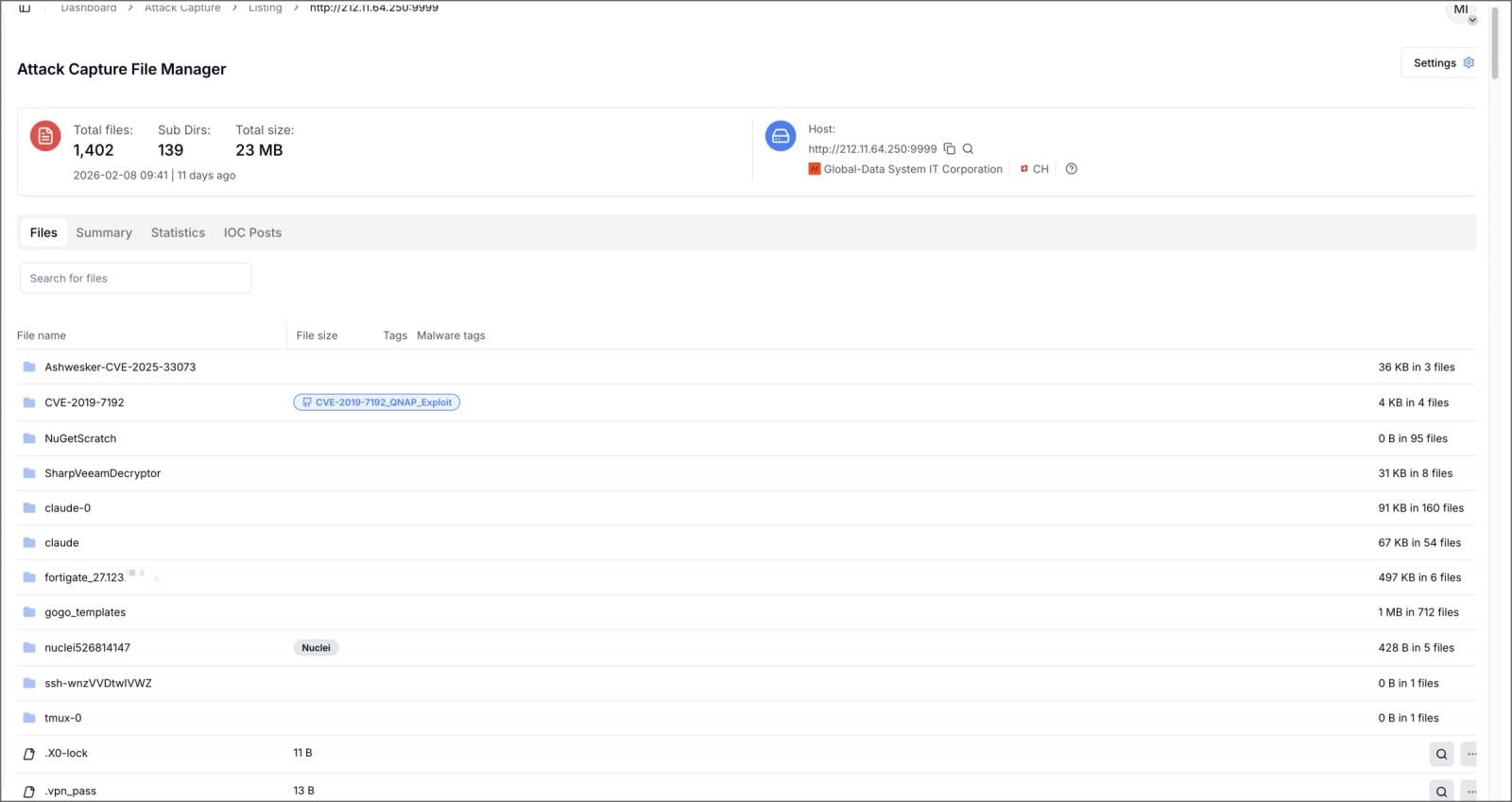
The researcher shared that the misconfigured server at 212.11.64[.]250, also found by Amazon, exposed 1,402 files, including stolen FortiGate configuration backups, Active Directory mapping data, credential dumps, vulnerability assessments, and attack planning documents.
“The server at 212.11.64[.]250:9999, hosted on AS4264 (Global-Data System IT Corporation, Zurich, Switzerland), contained 1,402 files across 139 subdirectories,” explained the threat researcher.
“Folders within the directory included CVE exploit code, FortiGate configuration files, Nuclei scanning templates and Veeam credential extraction tools. Two folders named claude-0 and claude contained over 200 files between the two, including Claude Code task outputs, session diffs, and cached prompt states.”
“A folder titled fortigate_27.123(full IP redacted) held configuration data and credentials from what appeared to be a compromised FortiGate appliance.”
Source: Cyber and Ramen
Included in the exposed files was a custom Model Context Protocol (MCP) server named ARXON, which acted as a bridge between reconnaissance data and commercial large language models. The researcher said they were unable to find any public references to ARXON, indicating it was likely a custom MCP framework created by the threat actor.
An MCP server acts as an intermediary layer that ingests data, feeds it into language models, and then uses the generated output with other tools.
“`
The Role of Data Automation in Cybersecurity Campaigns
Within a recent cybersecurity campaign, data ingestion played a crucial role in automating post-compromise analysis and attack planning. The campaign utilized a separate Go tool named CHECKER2, a Docker-based orchestrator, to simultaneously scan thousands of VPN targets. Logs revealed over 2,500 potential targets across more than 100 countries.
Researchers collected reconnaissance data from compromised FortiGate appliances and internal networks, feeding it into ARXON. ARXON then utilized large language models such as DeepSeek and Claude to generate structured attack plans. These plans included instructions for acquiring Domain Admin, recommended locations for credential searches, exploitation steps, and strategies for lateral movement to other devices.
In certain instances, Claude Code was configured to autonomously execute offensive tools like Impacket scripts, Metasploit modules, and hashcat, eliminating the need for threat actors to approve each command.
Over several weeks, the operation evolved from using the open-source HexStrike MCP framework to the automated and customized ARXON system. Amazon’s assessment highlighted the use of generative AI as a force multiplier for attackers, allowing them to scale intrusions more efficiently. Defenders were advised to prioritize patching edge devices, auditing unusual SSH activity, and monitoring VPN account creation.
Notably, security researcher Germán Fernández discovered a server exposing a directory containing AI-generated tools targeting FortiWeb. Although unrelated to the FortiGate campaign, this finding underscores the trend of threat actors leveraging AI tools in their attacks.
Update 2/21/26: Additional technical insights from Cyber and Ramen security blog and Germán Fernández have been included.

Keeping up with modern IT infrastructure demands automation for faster workflows. Discover how your team can eliminate manual delays, enhance reliability through automated responses, and create intelligent workflows using existing tools in our comprehensive Tines guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook3 months ago
Facebook3 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook3 months ago
Facebook3 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































