Security
The Rise and Fall of Arkanix Stealer: An AI Info-Stealer Experiment

An innovative malware operation known as Arkanix Stealer emerged on various dark web platforms in late 2025, believed to have been developed with the assistance of artificial intelligence.
The project featured a control panel and a Discord server for user communication. However, the creator abruptly shut down these platforms just two months after the operation commenced.
Arkanix Stealer offered a range of data theft functionalities commonly used by cybercriminals, including a modular structure and anti-analysis features.

According to Kaspersky researchers, an analysis of Arkanix Stealer revealed indications of AI-assisted development, potentially leading to significantly reduced development time and costs.
Source: Kaspersky
The researchers speculate that Arkanix was a short-term venture aimed at quick financial gains, making detection and tracking more challenging.
Arkanix Stealer Emerges Online
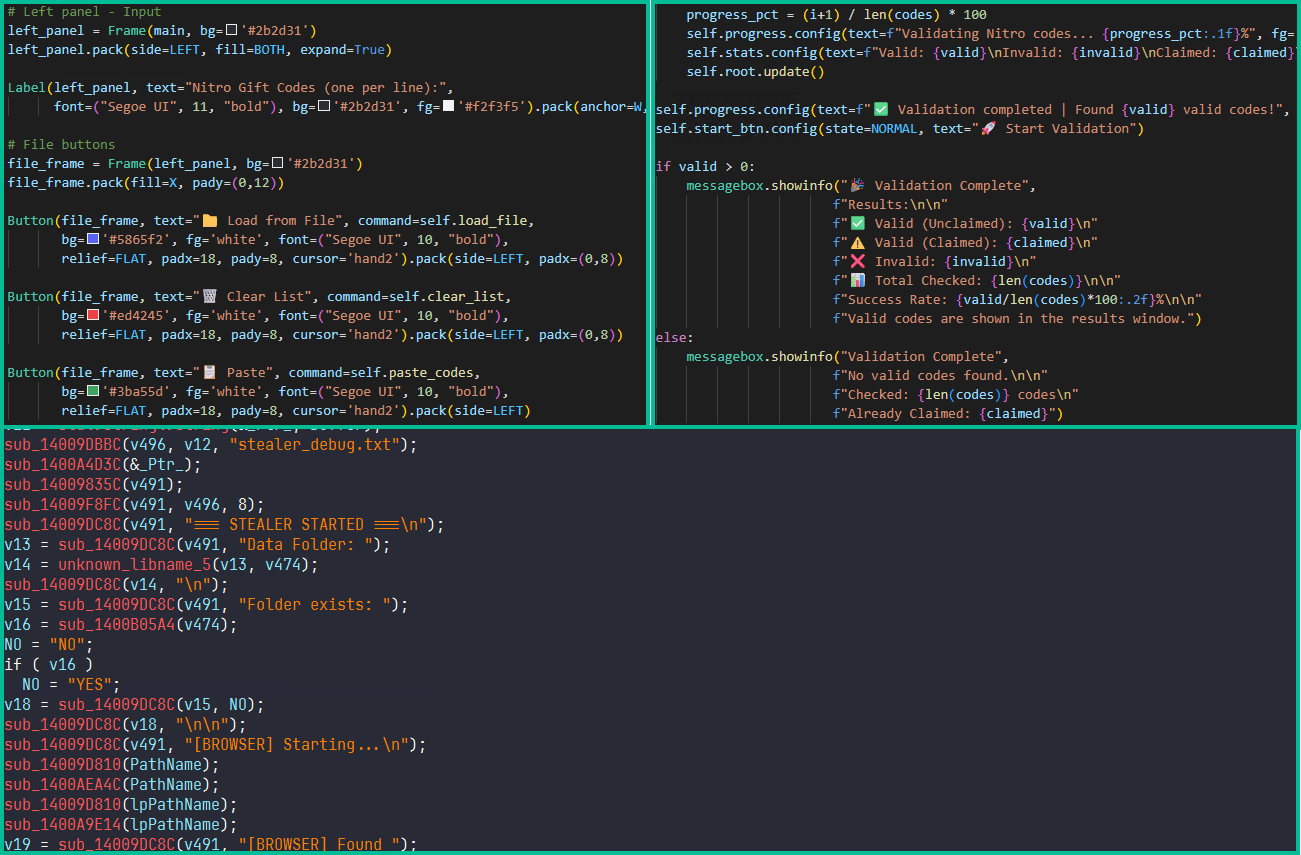
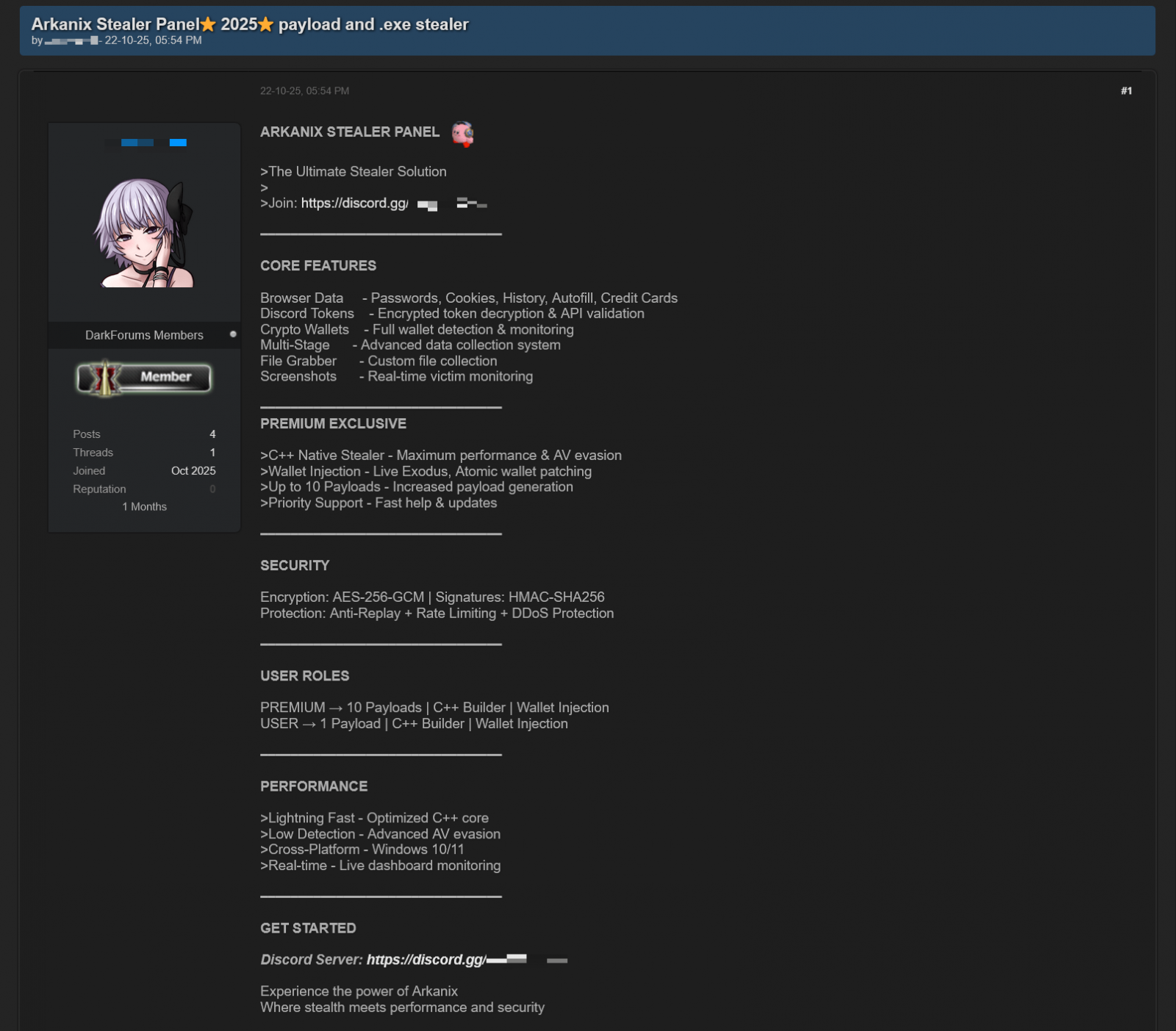
In October 2025, Arkanix Stealer began gaining traction on hacker forums, offering two tiers to potential clients: a basic version utilizing Python and a “premium” edition featuring a native C++ payload with VMProtect protection, AV evasion, and wallet injection capabilities.
Source: Kaspersky
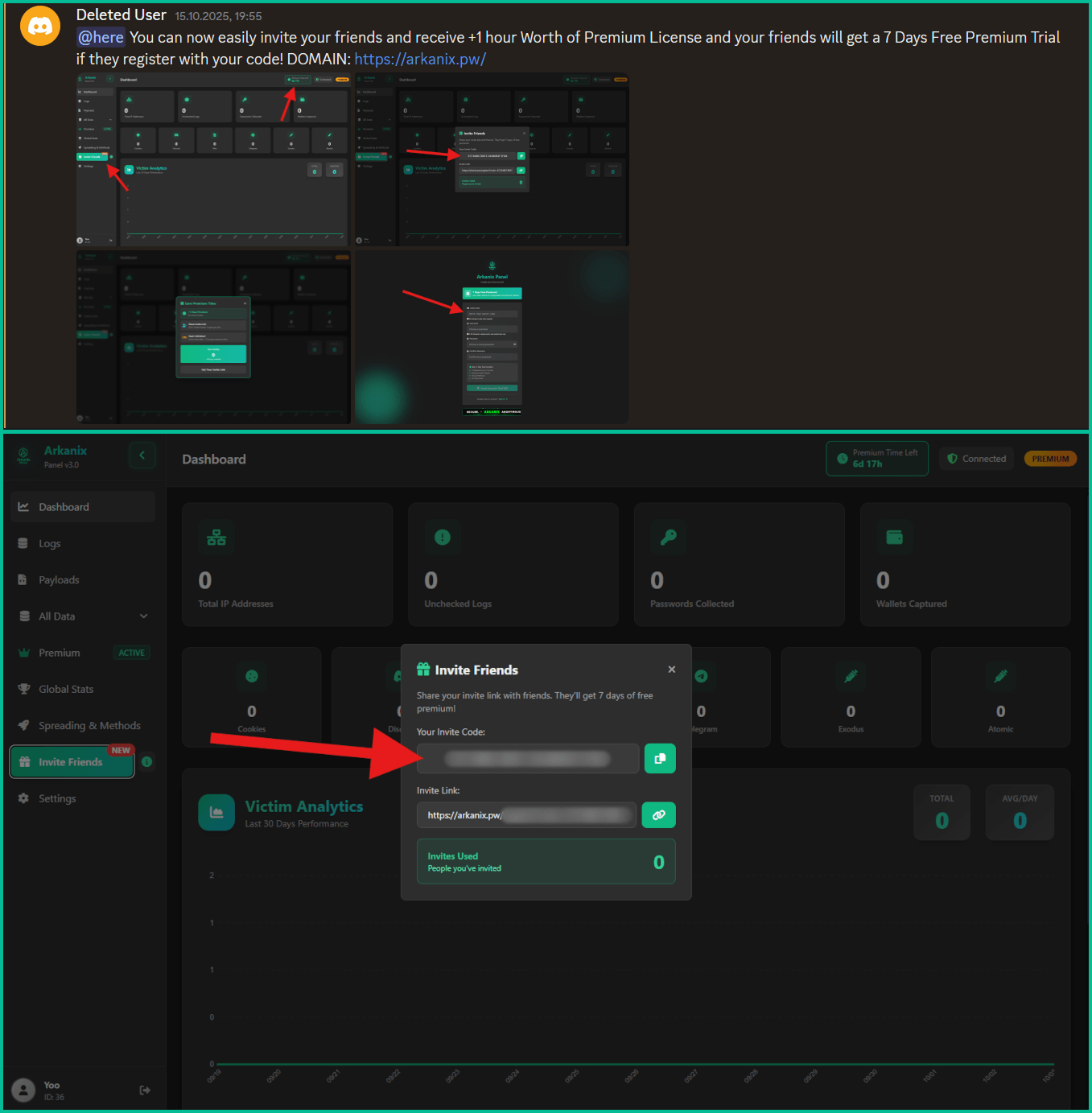
The developer established a Discord server to serve as a community hub for project updates, feature feedback, and user support.
Furthermore, a referral scheme was implemented to boost project visibility, offering referrers extra premium access time and new users a free week of the premium version.
Source: Kaspersky
Data Theft Capabilities
Arkanix Stealer is capable of gathering system data, extracting browser-stored information (history, autofill data, cookies, passwords), and harvesting cryptocurrency wallet details from 22 browsers. Kaspersky experts note its ability to retrieve 0Auth2 tokens on Chromium-based browsers.
Additionally, the malware can acquire data from Telegram, pilfer Discord credentials, propagate via the Discord API, and send messages to the victim’s contacts/channels.
Arkanix also targets credentials for VPN services like Mullvad, NordVPN, ExpressVPN, and ProtonVPN, and can archive files from the local filesystem for asynchronous exfiltration.
Additional modules available for download from the command-and-control server include a Chrome grabber, a wallet patcher for Exodus or Atomic wallets, a screenshot tool, HVNC, and stealers for FileZilla and Steam.
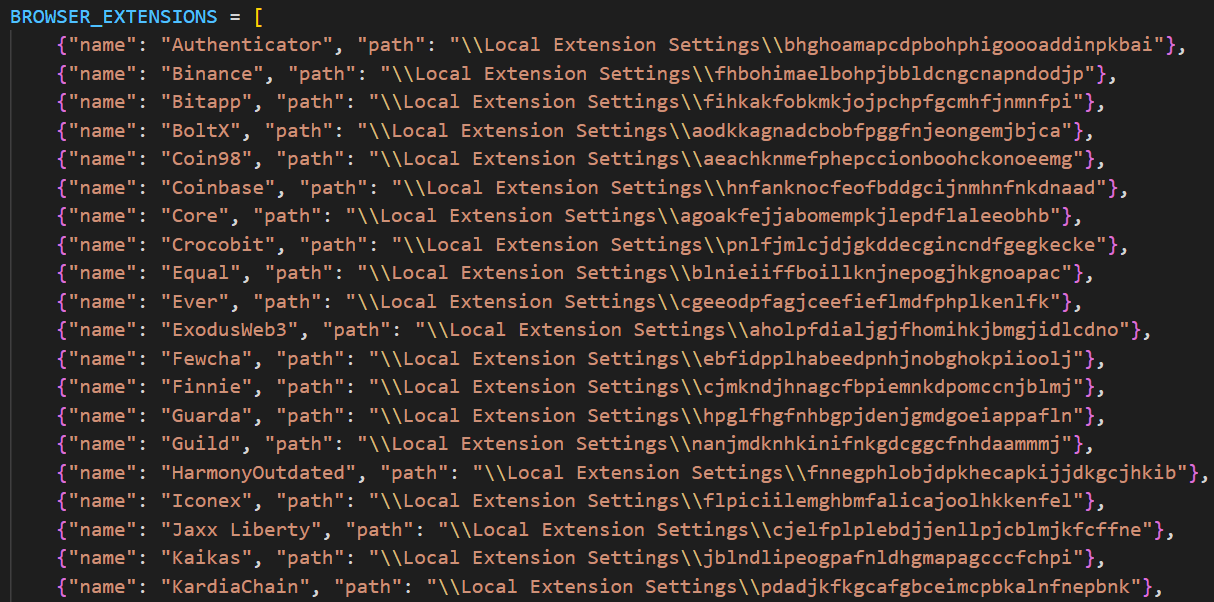
Source: Kaspersky
The premium native C++ version of Arkanix Stealer includes RDP credential theft, anti-sandbox and anti-debugging mechanisms, WinAPI-based screen capture, and targets gaming platforms such as Epic Games, Battle.net, Riot, Unreal Engine, Ubisoft Connect, and GOG.
Moreover, the advanced variant introduces the ChromElevator post-exploitation tool, designed to infiltrate suspended browser processes for data theft and circumvent Google’s App-Bound Encryption (ABE) for unauthorized access to user credentials.
The ultimate goal of the Arkanix Stealer initiative remains ambiguous. The project could be an experiment to assess how AI assistance enhances malware development and speeds up feature deployment within the community.
Kaspersky’s evaluation suggests that Arkanix functions more as a public software product than a clandestine data stealer.
The researchers provide a detailed list of compromise indicators (IoCs), comprising file hashes, domains, and IP addresses.

Modern IT infrastructure outpaces manual workflows. Discover how automated responses can reduce delays and enhance reliability with Tines’ comprehensive guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook3 months ago
Facebook3 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook3 months ago
Facebook3 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS