Security
GlassWorm Strikes Back: 3 New VSCode Extensions Infected on OpenVSX

An alarming resurgence of the GlassWorm malware campaign has been detected, impacting the OpenVSX and Visual Studio Code marketplaces once again. This time, three new VSCode extensions have surfaced, garnering over 10,000 downloads within a short span.
Characterized by its utilization of Solana transactions to retrieve a payload targeting account credentials from GitHub, NPM, and OpenVSX, as well as cryptocurrency wallet data from 49 extensions, GlassWorm poses a significant threat to users.
The malware employs invisible Unicode characters that appear as blanks but execute as JavaScript, enabling malicious activities to be carried out seamlessly.

Initially introduced through 12 extensions on Microsoft’s VS Code and OpenVSX platforms, with a total of 35,800 downloads, the true extent of the campaign’s impact remains uncertain due to potential inflation of download numbers by the threat actor.
In response to the breach, Open VSX took proactive measures by rotating access tokens for compromised accounts, implementing enhanced security protocols, and officially closing the incident.
The Resurgence of GlassWorm
Recent observations by Koi Security, a cybersecurity firm monitoring the campaign, reveal that the attacker has revisited OpenVSX, leveraging familiar infrastructure but with updated command-and-control (C2) endpoints and Solana transactions.
The three tainted OpenVSX extensions identified as carriers of the GlassWorm payload are:
- ai-driven-dev.ai-driven-dev — 3,400 downloads
- adhamu.history-in-sublime-merge — 4,000 downloads
- yasuyuky.transient-emacs — 2,400 downloads
Koi Security notes that all three extensions utilize the same covert Unicode character obfuscation technique seen in the original files, effectively evading OpenVSX’s enhanced defenses.
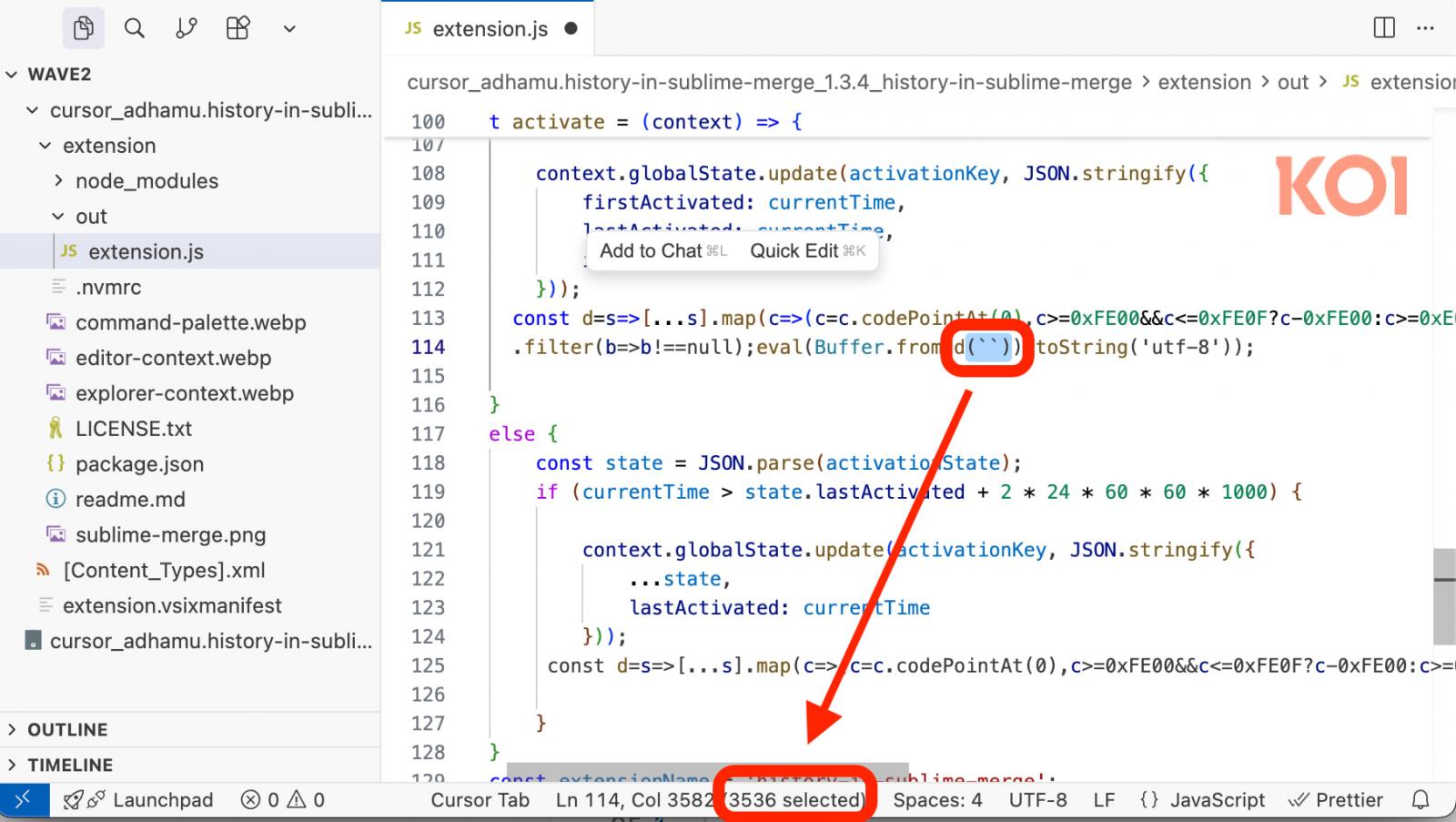
Source: Koi Security
Despite previous exposure, GlassWorm operators persisted in their malicious activities and had pivoted to GitHub. The return to OpenVSX through new extensions signifies a strategic move to resume operations across multiple platforms.
Unveiling the Attack Infrastructure
An anonymous tip received by Koi Security led to the discovery of the attackers’ server, providing crucial insights into the victims impacted by the campaign.
Data retrieved indicates a global reach, with GlassWorm infections identified in systems across the United States, South America, Europe, Asia, and even within a government entity in the Middle East.
Further investigation reveals that the operators, who predominantly speak Russian, rely on the RedExt open-source C2 browser extension framework for their operations.
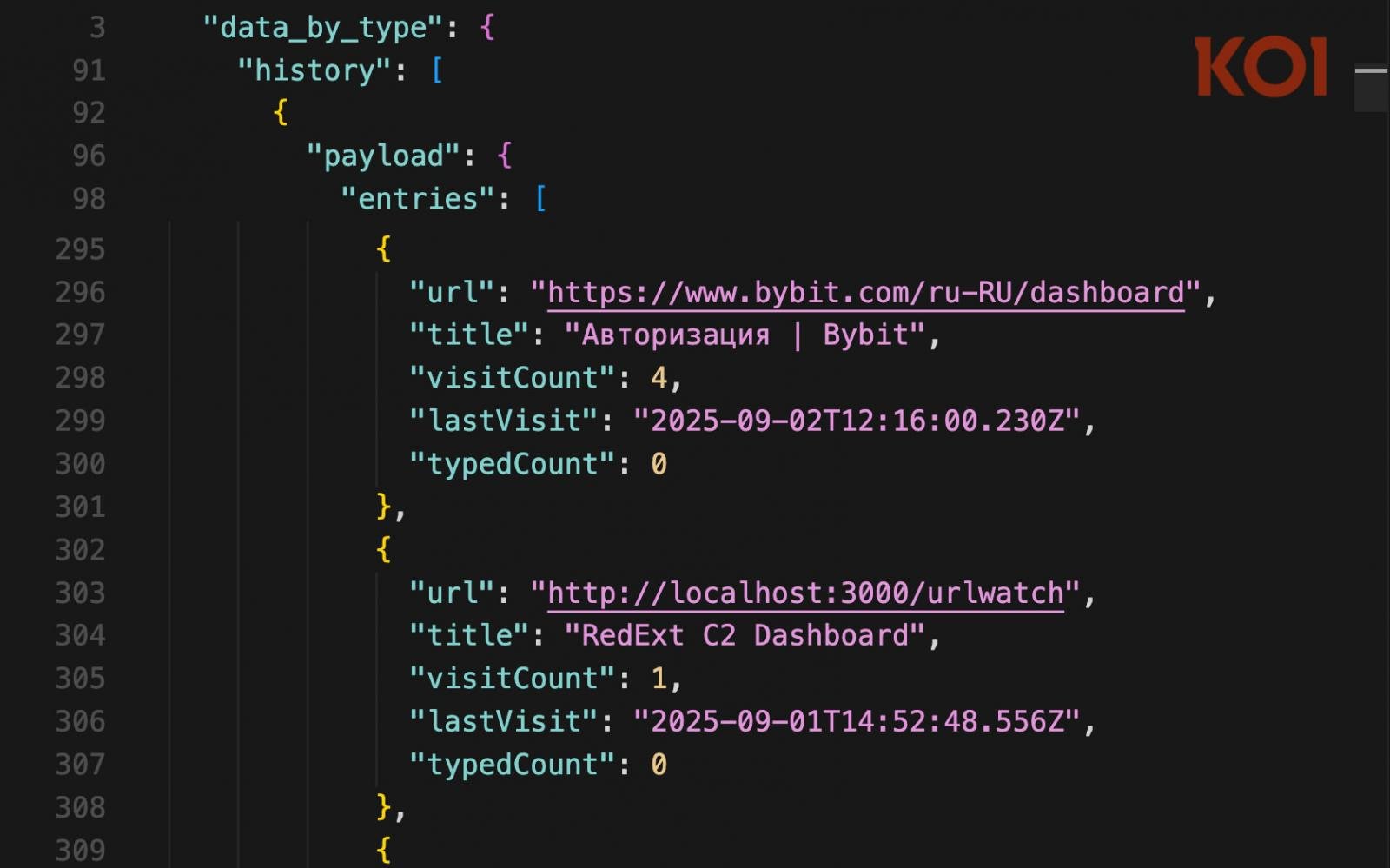
Source: Koi Security
Koi Security has cooperated with law enforcement, sharing critical data such as user IDs from multiple cryptocurrency exchanges and messaging platforms. Efforts are underway to notify organizations impacted by the breach.
With 60 distinct victims identified so far, based on information extracted from a single exposed endpoint, the severity of the situation is evident. The GlassWorm-infected extensions remain accessible for download on OpenVSX at present.

Empower your team with essential guidance on secrets management and secure coding practices. Download the cheat sheet now for comprehensive insights.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































