Security
Security Breach: Hackers Target Gladinet CentreStack with RCE Exploits

A previously undisclosed vulnerability in the cryptographic algorithm utilized by Gladinet’s CentreStack and Triofox products is being exploited by hackers for remote code execution attacks, allowing them to access hardcoded cryptographic keys, security researchers have revealed.
The vulnerability, which has not yet been assigned an official identifier, prompted Gladinet to notify its customers and recommend updating to the latest version of the affected products, released on November 29.
Security experts at Huntress have identified at least nine organizations that have been targeted in attacks leveraging this vulnerability, as well as an older flaw known as CVE-2025-30406, which enables local file access without authentication.
Uncovering the Flaw
By analyzing the Indicators of Compromise provided by Gladinet, Huntress researchers were able to pinpoint the source of the vulnerability and understand how threat actors are exploiting it.
The flaw lies in the custom implementation of the AES cryptographic algorithm in Gladinet CentreStack and Triofox, where the encryption key and Initialization Vector (IV) are hardcoded in the GladCtrl64.dll file, making them easily accessible.
The keys, derived from static 100-byte strings of Chinese and Japanese text, remain consistent across all installations of the products, posing a significant security risk.
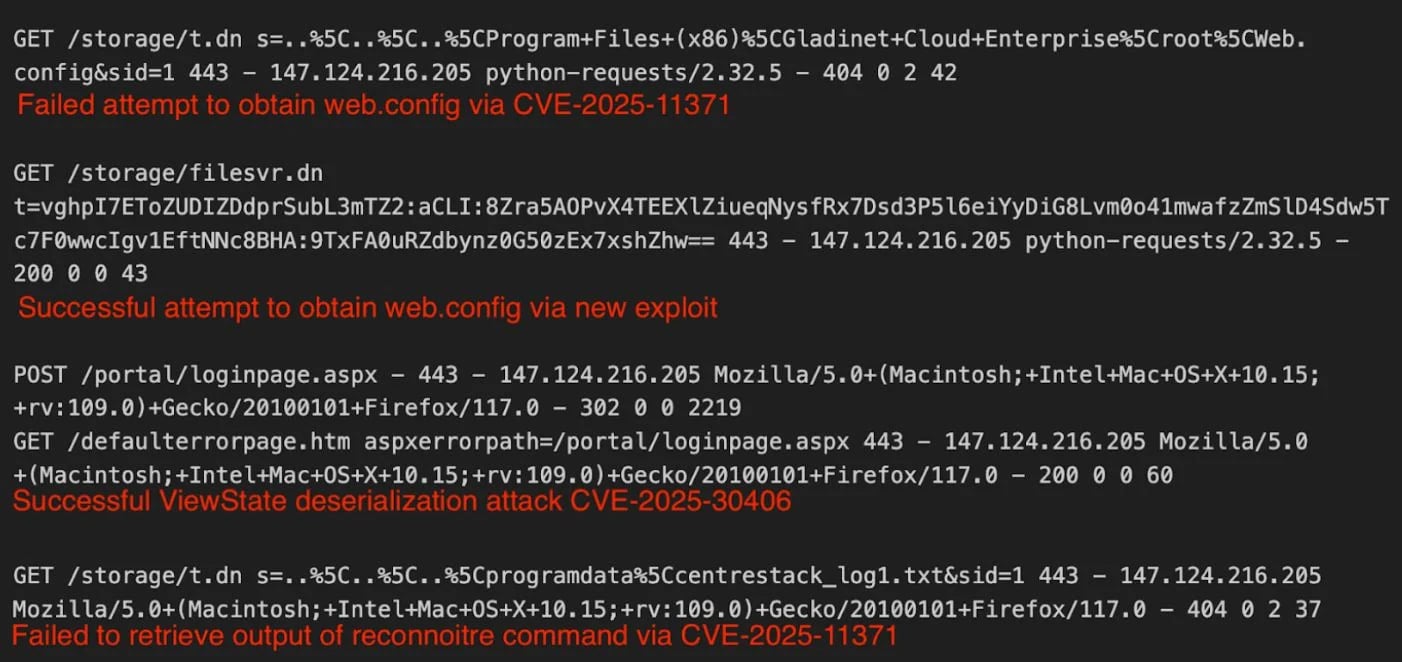
The vulnerability resides in the ‘filesvr.dn’ handler, which decrypts the ‘t’ parameter (Access Ticket) using the static keys, allowing threat actors to decrypt sensitive information such as file paths, usernames, passwords, and timestamps.
Attackers are able to forge Access Tickets using the hardcoded AES keys, setting the timestamp to year 9999 to ensure the ticket never expires. This enables them to request sensitive files from the server and potentially trigger remote code execution through a ViewState deserialization flaw.
Source: Huntress
Despite the identification of an attacking IP address, 147.124.216[.]205, the specific perpetrators behind these attacks remain unknown.
Huntress has confirmed that as of December 10, nine organizations across various sectors, including healthcare and technology, have been affected by these attacks.
Users of Gladinet CentreStack and Triofox are strongly advised to update to version 16.12.10420.56791, released on December 8, and to rotate their machine keys as a precautionary measure.
Additionally, organizations are recommended to scan their logs for the presence of the ‘vghpI7EToZUDIZDdprSubL3mTZ2’ string, which serves as a reliable indicator of compromise associated with the encrypted file path.
Huntress has provided detailed mitigation guidance and indicators of compromise to assist defenders in safeguarding their environments and detecting potential breaches.

Addressing broken IAM practices is crucial for businesses, as it impacts various aspects of operations. Learn about effective IAM strategies and practices in this comprehensive guide.
Discover why traditional IAM approaches may fall short in modern environments, explore examples of successful IAM implementations, and access a checklist for developing a scalable IAM strategy.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS






























