Security
Not all ASUS Live Update Alerts are Critical: Understanding CVE-2025-59374

The Truth Behind the ASUS Live Update CVE-2025-59374
Reports of a vulnerability in ASUS Live Update, known as CVE-2025-59374, have been circulating in the cybersecurity community, sparking concerns about potential exploitation. However, a closer examination reveals that this vulnerability is not a new threat but rather a historical supply-chain attack on an End-of-Life (EoL) software product.
Decoding CISA’s Known Exploited Vulnerabilities
The recent coverage of CVE-2025-59374 has portrayed it as a current security risk due to its inclusion in CISA’s Known Exploited Vulnerabilities catalog. Nevertheless, the reality is more nuanced than sensational headlines suggest.
The CVE documents the “ShadowHammer” supply-chain attack that occurred between 2018 and 2019, where maliciously altered ASUS Live Update binaries were distributed to a select group of targeted systems.
The severity of the compromise, now rated as a 9.3 (Critical) on the CVSS scale, is highlighted in the CVE entry:
“UNSUPPORTED WHEN ASSIGNED” Certain versions of the ASUS Live Update client were distributed with unauthorized modifications introduced through a supply chain compromise. The modified builds could cause devices meeting specific targeting conditions to perform unintended actions. Only devices that met these conditions and installed the compromised versions were affected. The Live Update client has already reached End-of-Support (EOS) in October 2021, and no currently supported devices or products are affected by this issue.
The designation “unsupported when assigned” clearly indicates that the CVE pertains to an EoL product.
The primary vendor advisory linked in the CVE entry dates back to 2019 and includes a link to an FAQ page with the last updated timestamp of December 6, 2025.
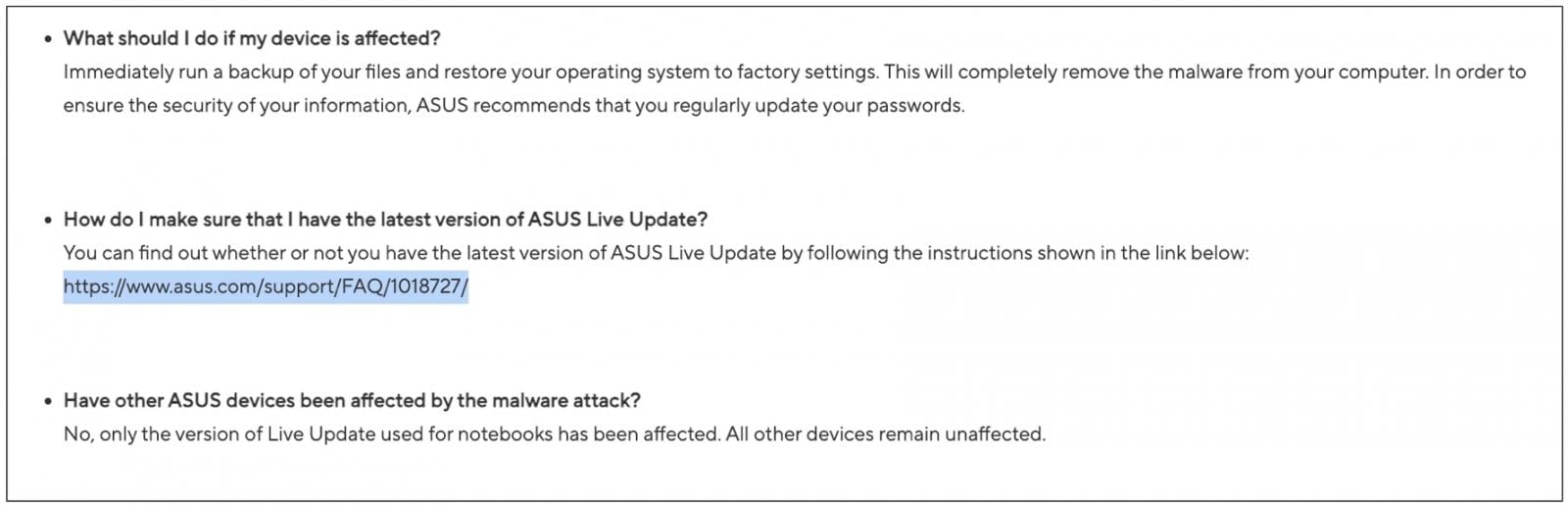
Despite recent updates to the FAQ page, the absence of original publication dates suggests that the page serves as a repository of information rather than an indicator of renewed risk.

(BleepingComputer)
Upon scrutiny, it becomes evident that the FAQ page serves as a reference point for users seeking guidance on upgrading the ASUS Live Update utility.
For more insights on the CVE assignment, ASUS and CISA were approached for comments, with CISA referring to Binding Operational Directive 22-01, which clarifies the criteria for inclusion in the Known Exploited Vulnerabilities catalog.
“Addition of a vulnerability to the KEV catalog does not indicate that CISA is observing current active exploitation. If there is accurate reporting of active exploitation, any vulnerability, despite its age, can qualify for KEV catalog addition”
Navigating the ASUS Live Update Vulnerability
Despite the historical context of CVE-2025-59374, users are advised to ensure they are using the latest patched version of the affected software. ASUS Live Update reached End-of-Support in October 2021, with no currently supported devices impacted by the issue.
The updated FAQ from December 2025 mentions the end of support on December 4, 2025, indicating version 3.6.15 as the final release. However, previous versions of the FAQ recommended upgrading to version 3.6.8 or higher to address security concerns.
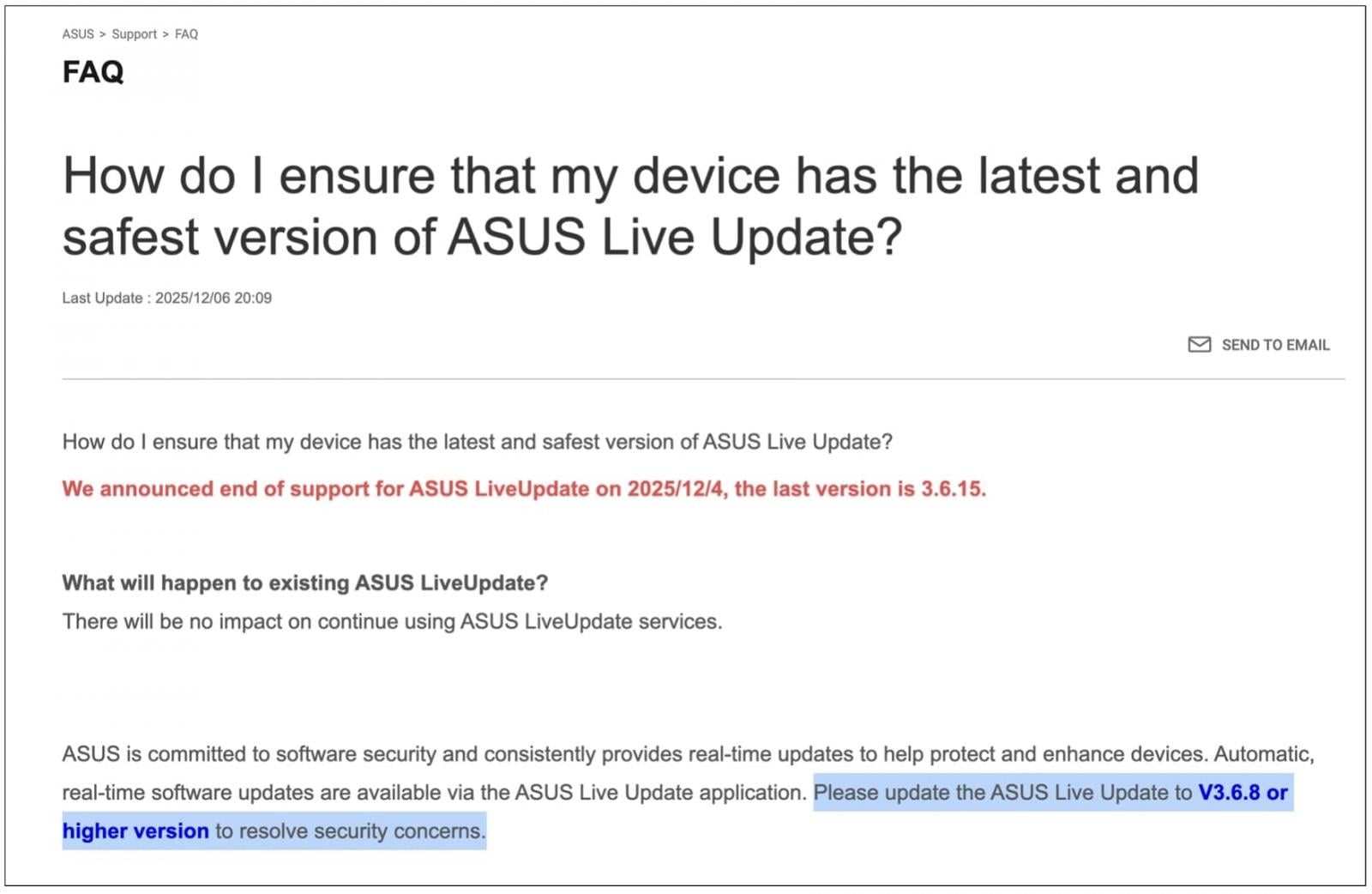
(BleepingComputer)
The release of version 3.6.15, although mentioned in the recent FAQ update, has been available since March 2024, indicating no immediate urgency for upgrades.
CVE-2025-59374 serves as a retrospective classification of a well-known attack, with FAQ updates and CISA’s context shedding light on the documentation-driven nature of recent updates.
Security teams are advised to exercise caution when reacting to CISA-linked CVEs, especially concerning outdated software or resolved incidents.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































