Security
Phishing Protection: Innovative Malware Service for Chrome Users

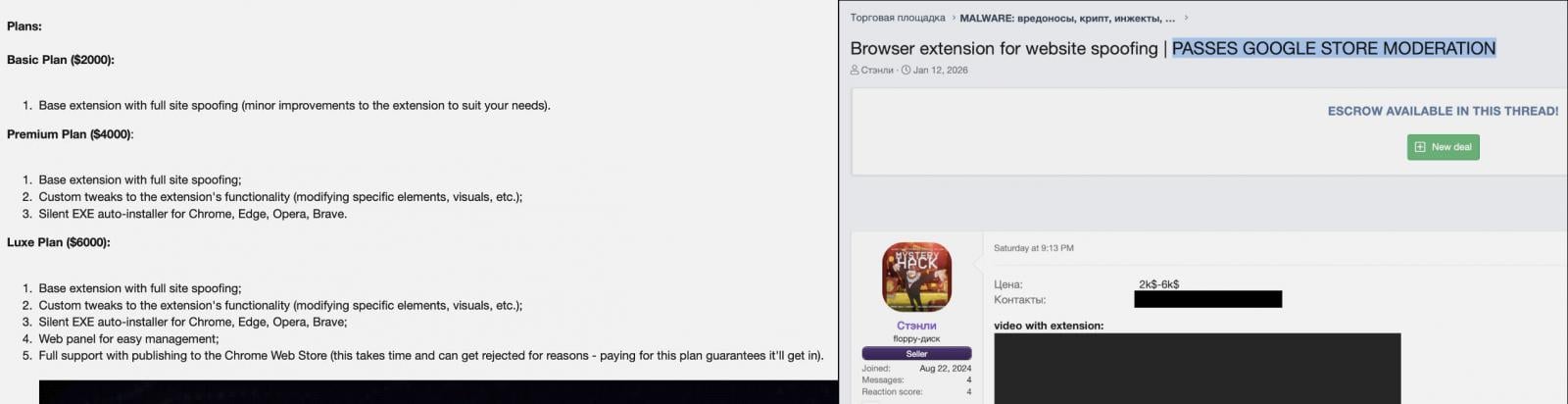
Malware Service “Stanley” Offers Malicious Chrome Extensions
A new malware service known as ‘Stanley’ has emerged, offering malicious Chrome extensions that can bypass Google’s review process and be published on the Chrome Web Store.
Varonis, a data security company, uncovered this malware-as-a-service (MaaS) project named Stanley, after the seller’s alias. Stanley promises easy phishing attacks by intercepting navigation and covering a webpage with an iframe displaying content of the attacker’s choice.
This new MaaS provides malicious Chrome extensions that can overlay a webpage with a full-screen iframe containing phishing content of the attacker’s choosing. It also boasts silent auto-installation on Chrome, Edge, and Brave browsers, along with support for custom tweaks.

The MaaS offers various subscription tiers, with the Luxe Plan being the most expensive, providing a web panel and full support for publishing the malicious extension on the Chrome Web Store.
Source: Varonis
Google has been contacted by BleepingComputer for a comment on the claims regarding Stanley, and updates will be provided on this matter.
According to Varonis, Stanley functions by superimposing a full-screen iframe with malicious content while keeping the victim’s browser address bar unaltered, displaying the legitimate domain.
.jpg)
Source: Varonis
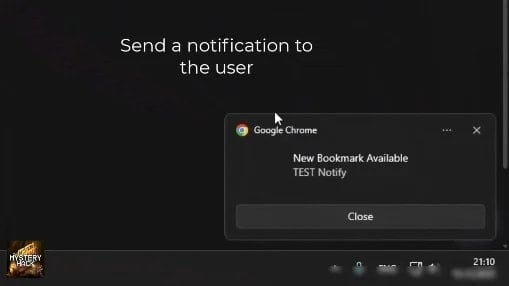
Operators with access to Stanley’s panel can activate or deactivate hijacking rules as needed or send notifications directly to the victim’s browser to lure them to specific pages, intensifying the phishing process.
Source: Varonis
Stanley supports IP-based victim identification, enabling geographic targeting and correlation across sessions and devices.
Furthermore, the malicious extension conducts persistent command-and-control (C2) polling every 10 seconds and implements backup domain rotation to enhance resilience against takedowns.
Varonis notes that Stanley, from a technical perspective, lacks advanced features and opts for a simple approach to implementing well-known techniques. The code contains Russian comments, empty catch blocks, and inconsistent error handling.
What sets this new MaaS apart is its distribution model, particularly the assurance of passing the Chrome Web Store review to infiltrate the trusted platform of browser add-ons.
Given the instances of such extensions slipping through security measures, users are advised to install only essential extensions, review user feedback, and verify the publisher’s credibility.

As MCP (Model Context Protocol) gains prominence in connecting LLMs to tools and data, security teams are swiftly enhancing the safety of these new services.
This handy cheat sheet outlines 7 best practices that can be implemented immediately.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































