Security
Stealthy Payload Delivery: How Ransomware Gangs Exploit ISPsystem VMs

Ransomware Gang Exploiting ISPsystem VMs for Covert Payload Delivery
Amidst recent ‘WantToCry’ ransomware incidents, cybersecurity experts at Sophos have uncovered a concerning trend. Ransomware operators are leveraging virtual machines (VMs) provided by ISPsystem, a legitimate virtual infrastructure management provider, to host and distribute malicious payloads on a large scale.
The researchers observed a pattern where attackers utilized Windows VMs with identical hostnames, indicating the use of default templates generated by ISPsystem’s VMmanager. This tactic was consistent across various ransomware groups, including LockBit, Qilin, Conti, BlackCat/ALPHV, and Ursnif, as well as other malware campaigns involving RedLine and Lummar info-stealers.
Source: Sophos
ISPsystem is a reputable software company known for developing control panels utilized by hosting providers for managing virtual servers and operating systems. Their VMmanager platform enables the provisioning of Windows or Linux VMs for customers.
According to Sophos’ findings, VMmanager’s default Windows templates exhibit a flaw where the same hostname and system identifiers are reused upon deployment. This loophole is exploited by bulletproof hosting providers that knowingly facilitate cybercrime operations, allowing malicious actors to set up VMs for command-and-control (C2) and payload-delivery purposes.
By camouflaging malicious systems within a sea of innocuous ones, attribution becomes challenging, and prompt takedowns are hindered. The majority of these nefarious VMs were traced back to a small group of providers with dubious reputations or sanctions, such as Stark Industries Solutions Ltd., Zomro B.V., First Server Limited, Partner Hosting LTD, and JSC IOT.
Sophos also identified a provider named MasterRDP with direct control over physical infrastructure, leveraging VMmanager for evasion and offering VPS and RDP services that evade legal requests.
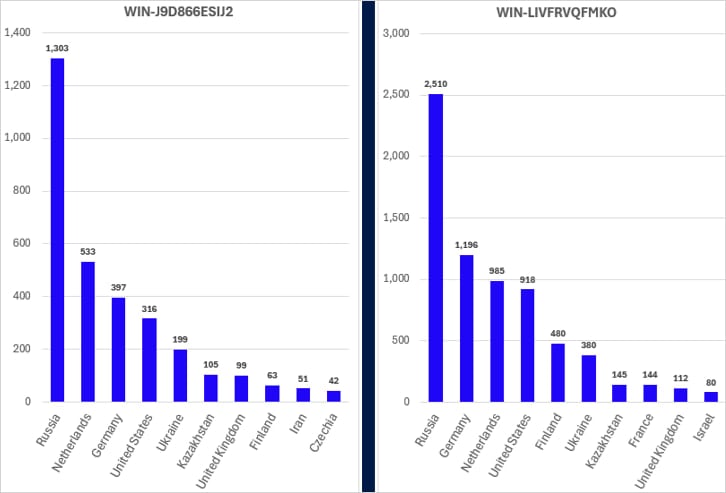
Four specific ISPsystem hostnames were flagged by Sophos, accounting for over 95% of internet-facing VMs associated with cybercriminal activities:
- WIN-LIVFRVQFMKO
- WIN-LIVFRVQFMKO
- WIN-344VU98D3RU
- WIN-J9D866ESIJ2
All these hostnames were detected either in customer data breaches or telemetry linked to cybercrime.
While ISPsystem’s VMmanager serves as a legitimate virtualization management platform, it inadvertently appeals to cybercriminals due to its affordability, ease of deployment, and turnkey capabilities.
ISPsystem has responded to these revelations by implementing randomization in hostname assignment for Windows templates. This update addresses the identified risk of technical identifier overlap, ensuring each new virtual machine is assigned a unique name upon deployment.
Efforts to reach ISPsystem for further comment on addressing the widespread abuse of VM templates were met with a statement acknowledging the issue and affirming their commitment to security enhancements.

Discover how automated workflows can streamline your IT infrastructure in the new Tines guide. Learn to reduce manual delays, enhance reliability, and scale intelligent workflows effortlessly.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS