Security
Beware: Fake Recruiters’ Malware-Ridden Coding Challenges

Fake Job Recruiters Conceal Malware in Developer Coding Challenges
An emerging trend in the realm of cyber threats involves North Korean actors targeting JavaScript and Python developers with cryptocurrency-related tasks under the guise of fake job recruiters.
This deceptive campaign, ongoing since at least May 2025, is characterized by its modular nature, allowing the threat actor to swiftly resume activities in the event of a partial compromise.
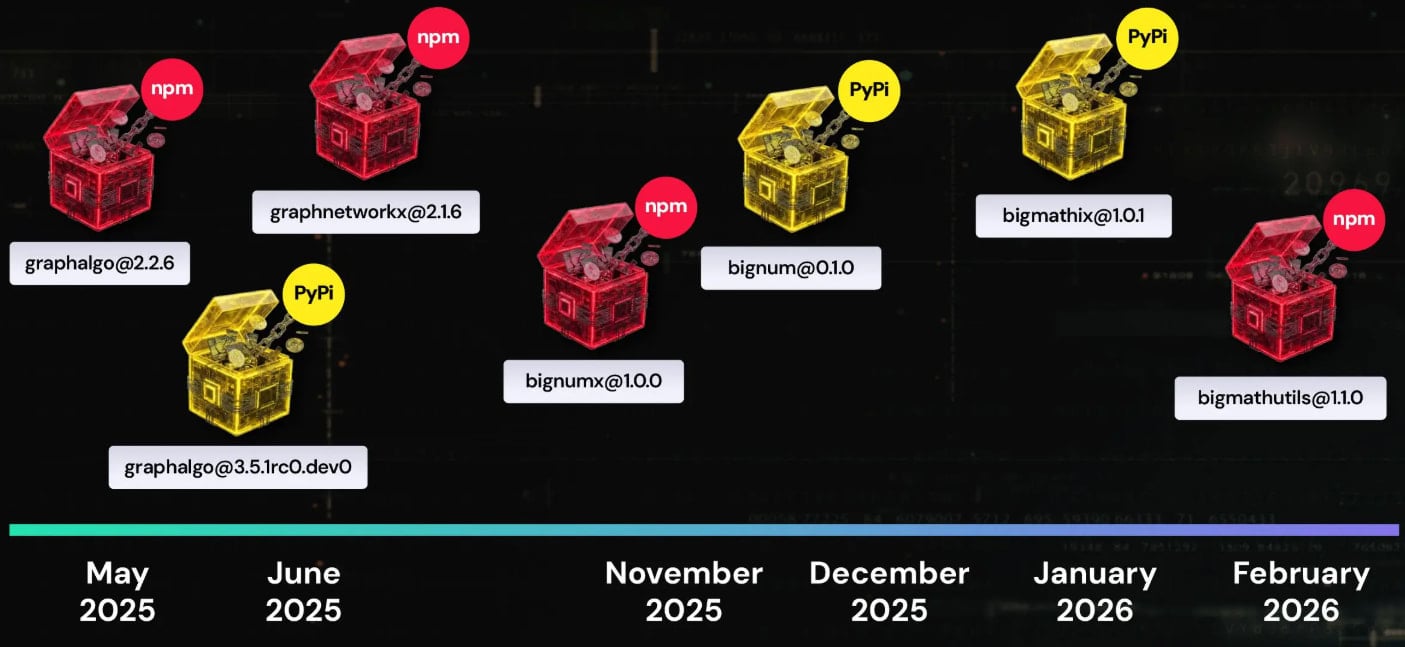
Utilizing packages from the npm and PyPi registries, the malicious actor deploys a remote access trojan (RAT) via downloaders hidden within 192 malicious packages associated with this campaign, affectionately named ‘Graphalgo’ by researchers.

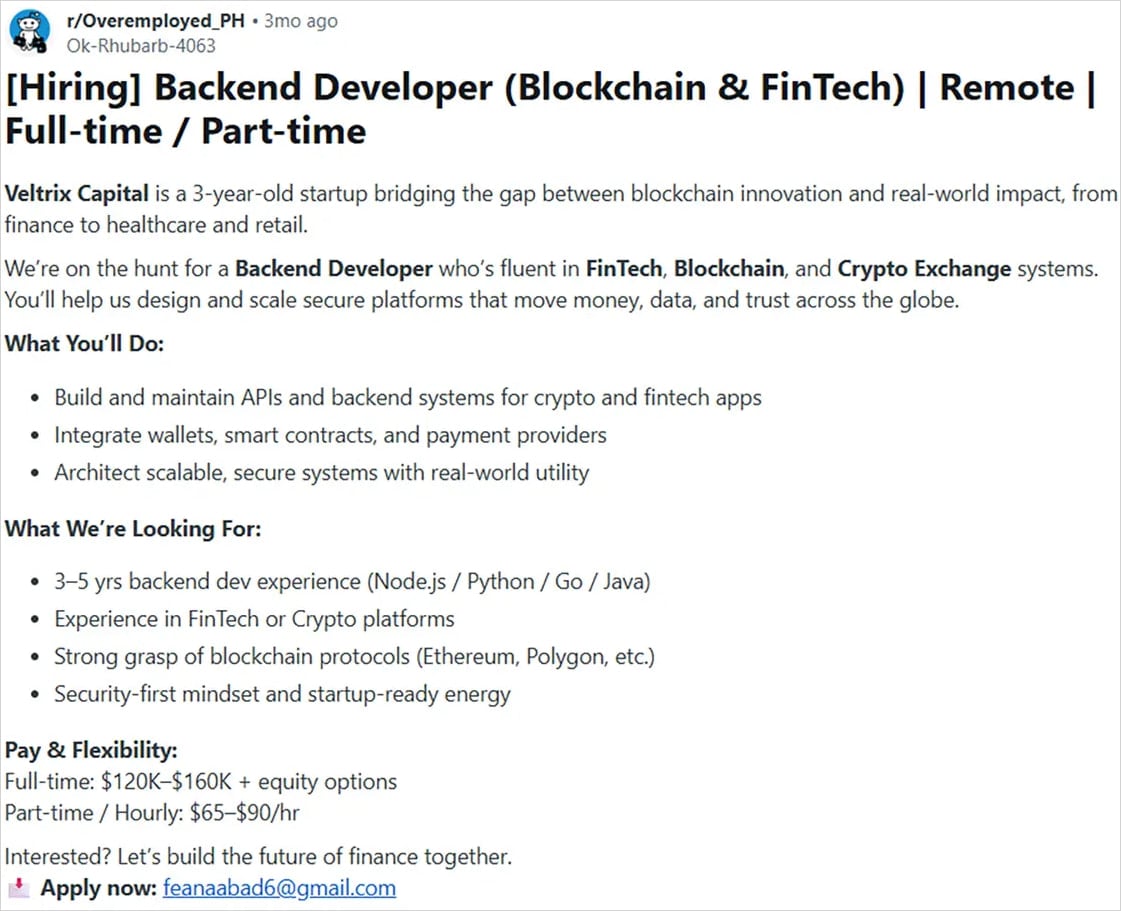
Experts at ReversingLabs, a software supply-chain security firm, have unveiled the modus operandi of this threat actor, uncovering a scheme where fake companies in the blockchain and crypto-trading sectors post job listings on popular platforms like LinkedIn, Facebook, and Reddit to lure unsuspecting developers.
Source: ReversingLabs
Prospective applicants are tasked with running, debugging, and enhancing a provided project to showcase their skills. However, the underlying motive of the attacker is to trick applicants into executing malicious code embedded within the project.
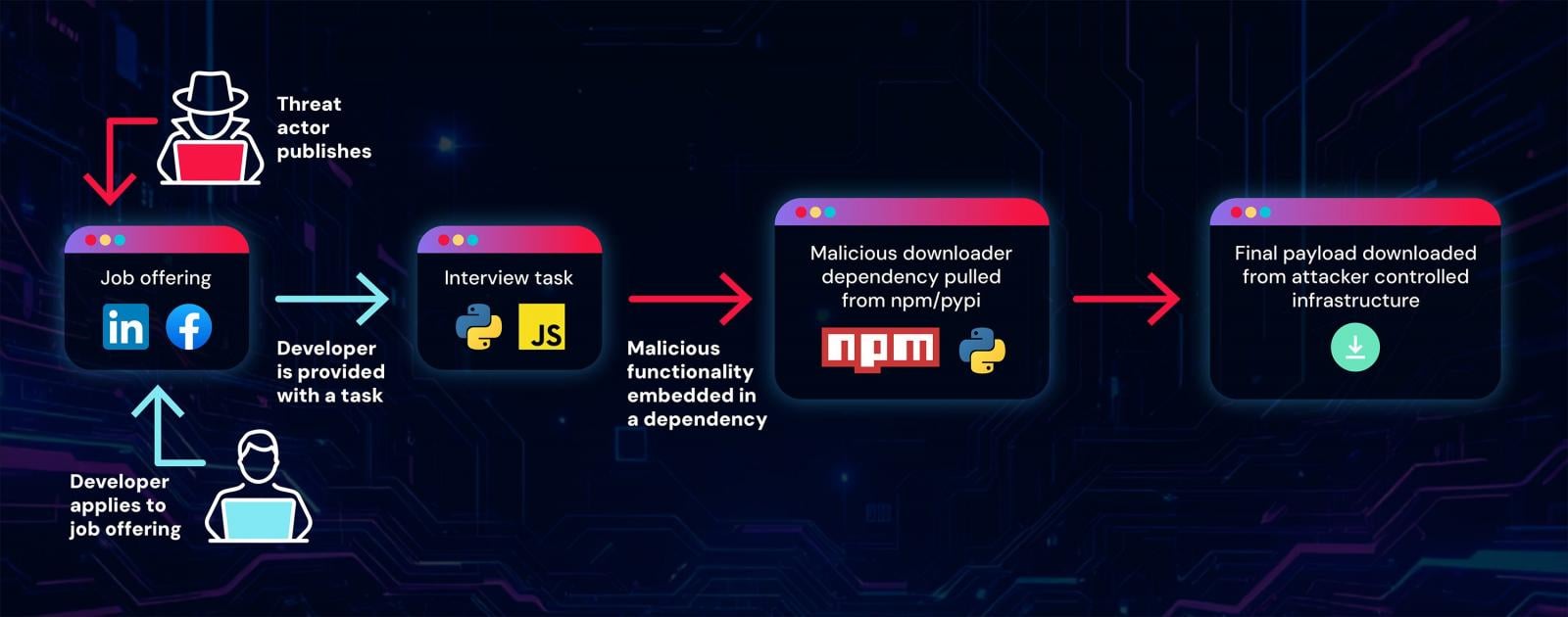
This deceptive tactic results in the unwitting installation and execution of a malicious dependency from a legitimate repository.
According to researchers, threat actors easily create these job task repositories by injecting a legitimate project with a malicious dependency, ready to be served to potential targets.
To mask the malicious intent of these dependencies, hackers host them on reputable platforms such as npm and PyPi.
source: ReversingLabs
In a highlighted case from the ReversingLabs report, a package named ‘bigmathutils,’ initially benign with 10,000 downloads, turned malicious with version 1.1.0, prompting the threat actor to swiftly remove the package, marking it as deprecated to conceal their activities.
The campaign name, ‘Graphalgo,’ stems from packages containing “graph” in their titles, often masquerading as popular libraries like graphlib, as detailed by the researchers.
Starting from December 2025, the North Korean actor transitioned to packages featuring “big” in their names, although ReversingLabs has yet to uncover the recruiting element or campaign frontend associated with these packages.
Source: ReversingLabs
The threat actor leverages Github Organizations, shared accounts for collaborative project work, to introduce malicious code indirectly through dependencies hosted on npm and PyPi, i.e., the Graphalgo packages.
Unsuspecting victims, following the project instructions, inadvertently infect their systems with these packages, installing a RAT payload that compromises their machines.
Of note, ReversingLabs researchers identified several developers who fell victim to this ploy and reached out to them for additional insights into the recruitment process.
The RAT enables processes monitoring, execution of remote commands from the command-and-control (C2) server, and data exfiltration or payload deployment.
Source: ReversingLabs
The RAT specifically checks for the MetaMask cryptocurrency extension on the victim’s browser, indicating a focus on financial theft.
Its C2 communication is token-protected to prevent unauthorized access, a tactic commonly employed by North Korean hackers.
ReversingLabs has uncovered multiple RAT variants in JavaScript, Python, and VBS, demonstrating a comprehensive approach to targeting various platforms.
Experts attribute the Graphalgo fake recruiter campaign to the Lazarus group with medium-to-high confidence, based on the infection vector of coding tests, the cryptocurrency-centric targeting, and the strategic alignment with previous North Korean threat activities.
Additionally, delayed activation of malicious code in packages and GMT +9 time zone timestamps in Git commits further substantiate the Lazarus group’s involvement.
For detailed indicators of compromise (IoCs), refer to the original report. Developers who inadvertently installed these malicious packages should reset all tokens, change account passwords, and consider reinstalling their operating systems.

Modern IT infrastructure moves faster than manual workflows can handle.
Discover how your team can streamline operations, enhance reliability through automated responses, and scale intelligent workflows using existing tools in the comprehensive Tines guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































