Security
Exposed: Critical Flaws and Public Exploits Unveiled
Critical Flaws in n8n Exposed, Leading to Server Compromise
Recently, it has been unveiled that the popular open-source workflow automation platform, n8n, harbors multiple critical vulnerabilities that allow attackers to gain complete control over the host server. These vulnerabilities, collectively known as CVE-2026-25049, can be exploited by authenticated users who have the ability to create or edit workflows on the platform, enabling them to execute remote code without restrictions.
Several cybersecurity firms have brought these issues to light, pointing out that they stem from flaws in n8n’s sanitization mechanism that bypassed a previous critical flaw fix for CVE-2025-68613, which was addressed on December 20.
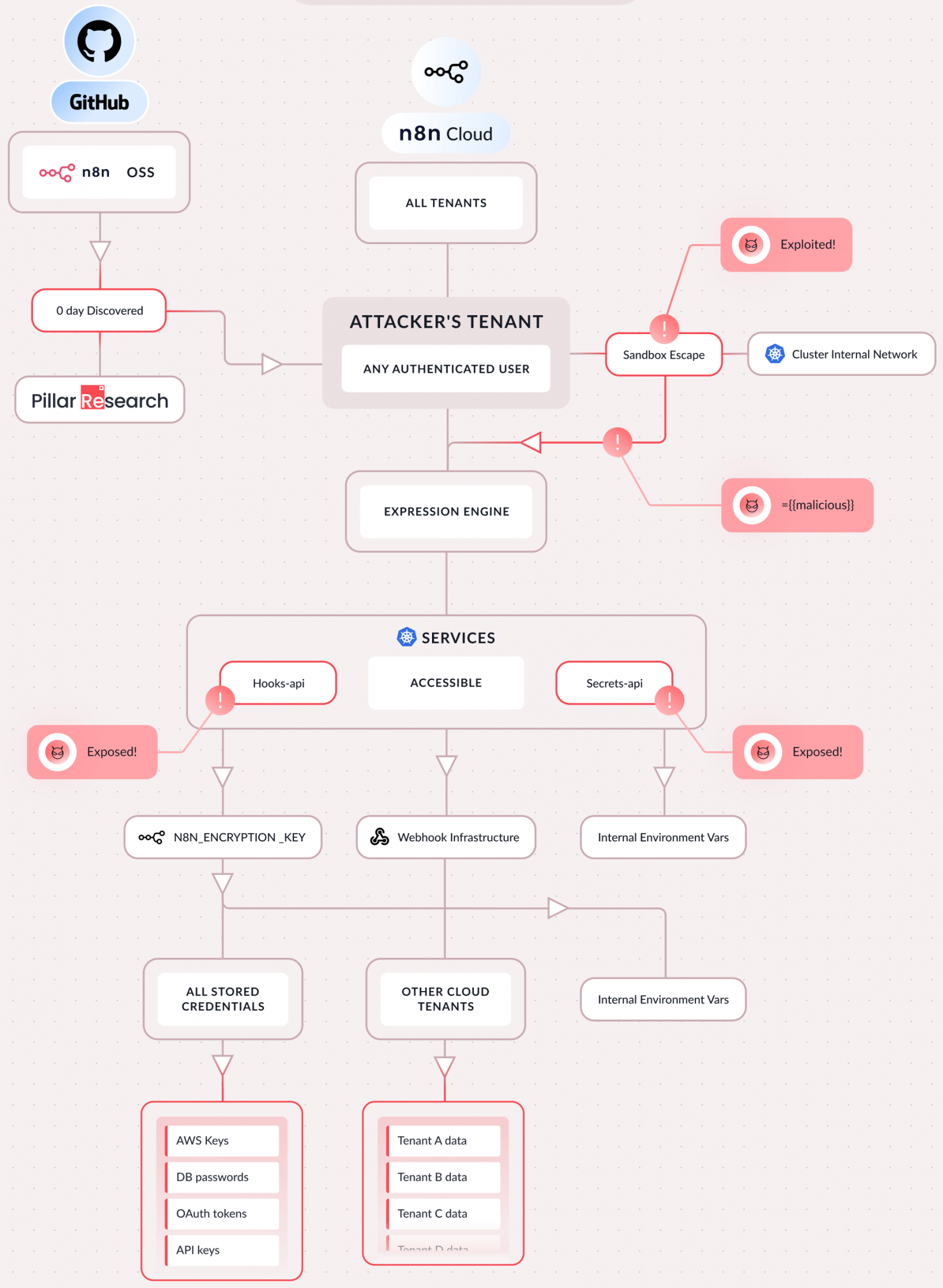
According to Pillar Security, exploiting CVE-2026-25049 allows attackers to compromise the n8n instance entirely, giving them the ability to run arbitrary system commands on the server, steal stored credentials, secrets like API keys and OAuth tokens, and sensitive configuration files.
Moreover, attackers were able to access the filesystem and internal systems, pivot to connected cloud accounts, and manipulate AI workflows, such as intercepting prompts, altering responses, and redirecting traffic. The multi-tenant nature of n8n also poses a risk of unauthorized access to other tenants’ data through internal cluster services.
Pillar Security emphasized the simplicity of the attack, stating, “If you can create a workflow, you can own the server.”
Source: Pillar Security
Pillar Security’s report sheds light on the incomplete AST-based sandboxing in n8n, which arises from weak sandboxing of user-written server-side JavaScript expressions in workflows. They demonstrated a bypass to the n8n team on December 21, 2025, revealing a vulnerability that led to RCE by escaping the sandbox and accessing the Node.js global object.
Although a fix was promptly implemented, further analysis by Pillar revealed its incompleteness, leaving room for a second escape via a different mechanism. n8n developers acknowledged this on December 30, eventually releasing version 2.4.0 on January 12, 2026, to address the issue.
Endor Labs researchers also discovered sanitization bypasses and demonstrated the CVE-2026-25049 vulnerability through a proof-of-concept exploit that achieved remote code execution. Cristian Staicu of Endor Labs highlighted a type-confusion vulnerability that allows attackers to bypass sanitization controls and execute arbitrary code.
SecureLayer7 researchers delved into the technical details of CVE-2026-25049, uncovering the vulnerability while analyzing a previous flaw, CVE-2025-68613. They eventually refined a successful bypass after numerous failed attempts and provided a PoC exploit along with steps for setting up and executing a malicious workflow for full server control.
Recommended Steps for n8n Users
It is imperative for n8n users to update the platform to the latest versions (1.123.17 and 2.5.2) to mitigate the risks posed by these vulnerabilities. Pillar Security advises rotating the ‘N8N_ENCRYPTION_KEY’ and all stored credentials, as well as reviewing workflows for any suspicious expressions.
If immediate updating is not feasible, administrators can implement temporary mitigation measures provided by the n8n team, such as limiting workflow permissions to trusted users and deploying n8n in a secure environment with restricted privileges and network access.
Despite no reported exploits of CVE-2026-25049, the rising popularity of n8n has attracted cybercriminals’ attention, particularly in light of the Ni8mare flaw (CVE-2026-21858). GreyNoise reported suspicious activity targeting vulnerable n8n endpoints, indicating a potential interest in post-exploitation opportunities.
It is crucial for organizations using n8n to stay vigilant, apply necessary updates, and follow recommended security practices to safeguard their systems and data from potential threats.
Modern IT infrastructure moves faster than manual workflows can handle.
Discover how your team can reduce hidden delays, enhance reliability through automation, and create intelligent workflows with Tines’ guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS

































