Security
FortiCloud SSO Vulnerability Exposes Thousands of Devices to Remote Attacks

Fortinet Devices Exposed to Cybersecurity Threats
Recent findings by internet security watchdog Shadowserver have revealed a concerning trend of over 25,000 Fortinet devices being exposed online with FortiCloud SSO enabled. This comes amidst a wave of attacks targeting a critical authentication bypass vulnerability.
Fortinet addressed this security flaw on December 9th, patching the issue known as CVE-2025-59718 (affecting FortiOS, FortiProxy, and FortiSwitchManager) and CVE-2025-59719 (impacting FortiWeb). The vulnerable FortiCloud SSO login feature is typically not activated until administrators register the device with Fortinet’s FortiCare support service.
According to cybersecurity company Arctic Wolf, threat actors are actively exploiting this vulnerability to compromise admin accounts through malicious single sign-on (SSO) logins. By exploiting a maliciously crafted SAML message, attackers can gain admin-level access to the web management interface and download sensitive system configuration files.
These compromised files expose critical information such as hashed passwords, internet-facing services, network layouts, and firewall policies, putting organizations at risk of cyberattacks.
Shadowserver reported tracking over 25,000 IP addresses with a FortiCloud SSO fingerprint, with a significant number located in the United States and India. However, the current status of securing these devices against CVE-2025-59718/CVE-2025-59719 exploitation remains unclear.
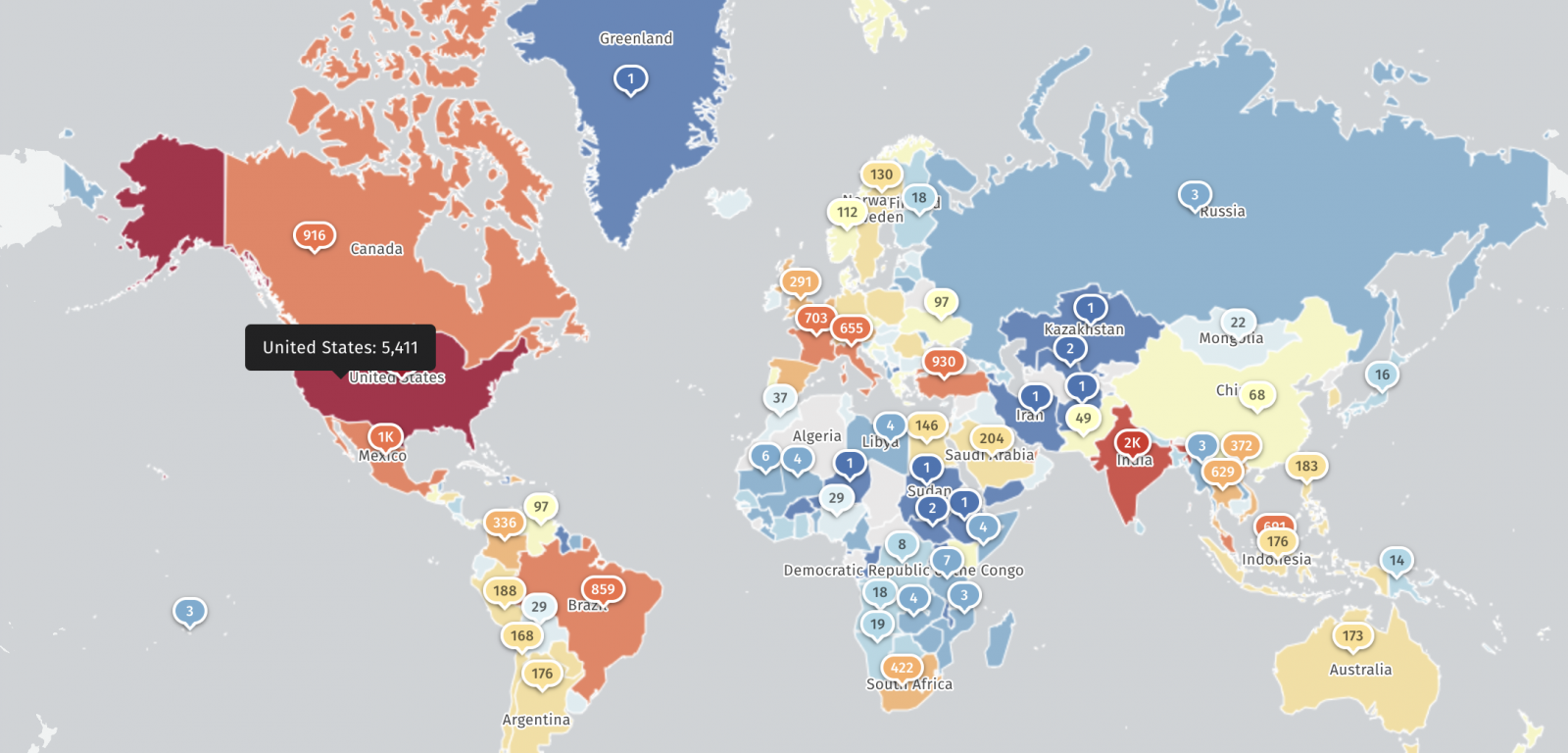
Further investigation by Macnica threat researcher Yutaka Sejiyama revealed over 30,000 Fortinet devices with FortiCloud SSO enabled and vulnerable web management interfaces accessible online. This extensive exposure raises concerns regarding the security practices of organizations using Fortinet products.
Recognizing the severity of the situation, the Cybersecurity and Infrastructure Security Agency (CISA) added the FortiCloud SSO authentication bypass flaw to its list of actively exploited vulnerabilities. U.S. government agencies have been instructed to patch their systems by December 23rd to mitigate the risk.
Fortinet security flaws have been a prime target for cyber-espionage, cybercrime, and ransomware groups, often exploited as zero-day vulnerabilities. Past incidents include the Chinese Volt Typhoon group exploiting FortiOS SSL VPN flaws to infiltrate a Dutch Ministry of Defence network and the recent discovery of FortiWeb zero-day vulnerabilities being used in widespread attacks.
It is crucial for organizations using Fortinet devices to promptly address security vulnerabilities and implement robust cybersecurity measures to prevent potential breaches and data compromises.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS