Security
GlassWorm Strikes Again: macOS Under Siege by Malicious OpenVSX Extensions

New GlassWorm Malware Attack Targets macOS via Compromised OpenVSX Extensions
A recent malware attack known as GlassWorm has been identified targeting macOS systems through compromised OpenVSX extensions. This sophisticated attack aims to steal sensitive information such as passwords, crypto-wallet data, and developer credentials and configurations.
The attack was initiated when a threat actor gained unauthorized access to the account of a legitimate developer named oorzc. The attacker then proceeded to push malicious updates containing the GlassWorm payload to four extensions that had collectively been downloaded 22,000 times.
GlassWorm attacks initially surfaced in late October, utilizing “invisible” Unicode characters to conceal malicious code and extract cryptocurrency wallet and developer account details. The malware is also equipped with capabilities for VNC-based remote access and SOCKS proxying.
Subsequently, GlassWorm expanded its reach across multiple attack waves, affecting both Microsoft’s official Visual Studio Code marketplace and the open-source alternative, OpenVSX.
Recent reports from Socket’s security team have unveiled a new campaign where GlassWorm trojanized several extensions, including oorzc.ssh-tools v0.5.1, oorzc.i18n-tools-plus v1.6.8, oorzc.mind-map v1.0.61, and oorzc.scss-to-css-compile v1.3.4. These extensions had remained benign for two years before the malicious updates were pushed on January 30, indicating a compromise of the oorzc account by GlassWorm operators.
Researchers have noted that this campaign exclusively targets macOS systems and retrieves instructions from Solana transaction memos. Interestingly, the attacker seems to exclude Russian-locale systems, potentially hinting at the origin of the threat actor.
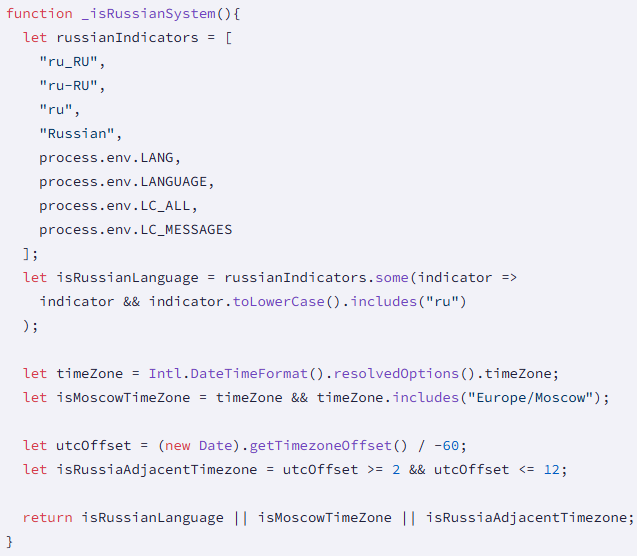
Source: Socket
GlassWorm deploys a macOS information stealer that establishes persistence on infected systems through a LaunchAgent, ensuring execution upon login. The malware harvests various data, including browser information from Firefox and Chromium, wallet extensions, keychain data, Safari cookies, developer secrets, and documents from the local filesystem, transmitting them to the attacker’s infrastructure at 45.32.150[.]251.
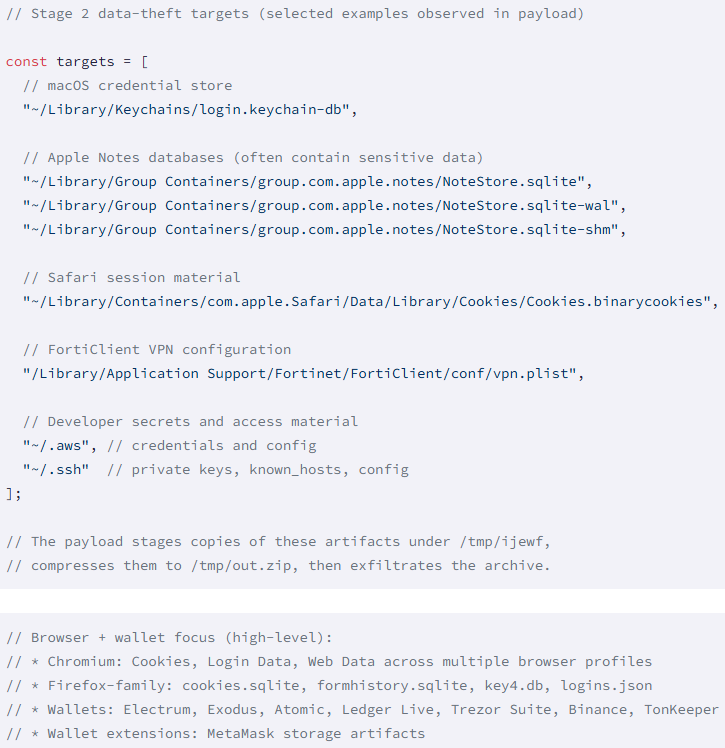
Source: Socket
Upon discovery, Socket promptly reported the compromised packages to the Eclipse Foundation, the entity overseeing the Open VSX platform. The security team took swift action by revoking unauthorized publishing access, invalidating tokens, and removing the malicious releases. Notably, the extension oorzc.ssh-tools was entirely removed from Open VSX due to multiple instances of malicious releases.
Although the affected extensions currently appear clean on the market, developers who downloaded the compromised versions are advised to conduct a thorough system cleanup and update all passwords and secrets as a precautionary measure.

Modern IT infrastructure operates at a rapid pace that manual workflows struggle to match. Discover how your team can streamline processes, enhance reliability, and automate responses with Tines in this comprehensive guide.
-

 Facebook3 months ago
Facebook3 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































