Security
GreyNoise’s Botnet Detection Tool: Keeping Your Devices Safe

GreyNoise Launches Free Scanner to Check for Botnet Involvement
In a bid to help users detect if their IP addresses have been compromised by malicious scanning operations, GreyNoise Labs has unveiled a new tool called GreyNoise IP Check. This tool allows individuals to determine if their IP addresses have been associated with activities such as botnets and residential proxy networks.
According to the threat monitoring firm, the prevalence of this issue has surged in the past year, with many unwitting users inadvertently aiding malicious online activities.
GreyNoise highlighted the proliferation of residential proxy networks, which have been using home internet connections as exit points for illicit traffic. The firm explained, “Over the past year, residential proxy networks have exploded and have been turning home internet connections into exit points for other people’s traffic.”
Whether through intentional installation of software for financial gain or through the stealthy infiltration of malware via dubious apps or browser extensions, individuals may unknowingly become conduits for malicious activities.
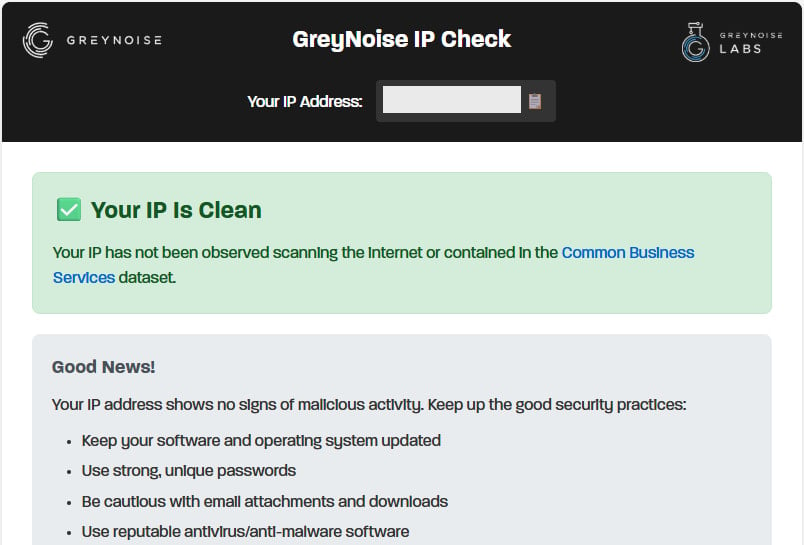
While various methods exist to identify involvement in botnet operations, GreyNoise’s IP address check tool offers a non-intrusive means of detection.
Users who visit the scanner’s webpage will receive one of three possible results:
- Clean: No indication of malicious scanning activity
- Malicious/Suspicious: The IP has exhibited scanning behavior, prompting users to investigate their network devices
- Common Business Service: The IP is associated with a VPN, corporate network, or cloud provider, where scanning activity is deemed normal
Source: BleepingComputer
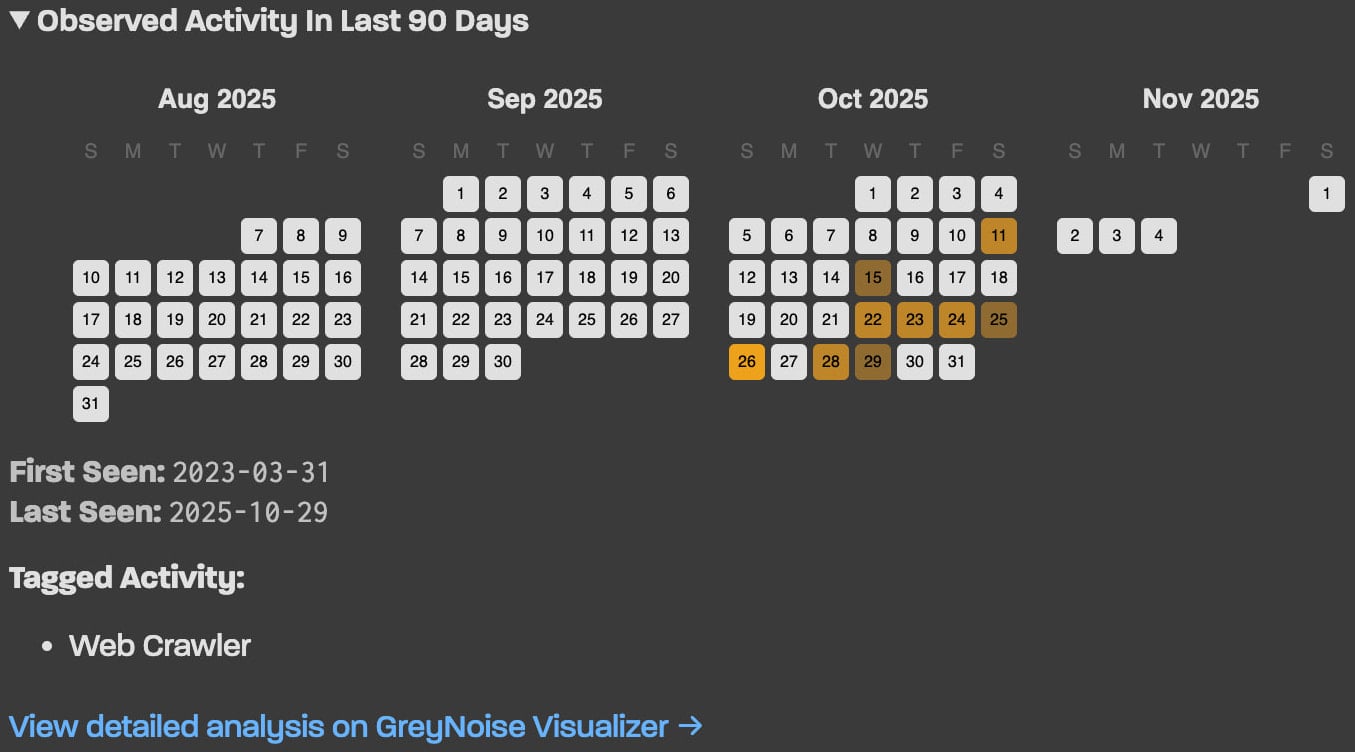
In cases where suspicious activity is linked to an IP address, the platform will present a 90-day historical timeline to help pinpoint potential infection points.
For instance, the installation of bandwidth-sharing clients or questionable applications preceding scanning activities may offer clues for remediation.
Source: GreyNoise
For more technical users, GreyNoise also provides an unauthenticated, rate-limit-free JSON API accessible via curl, enabling integration into scripts or monitoring systems.
If a scan reveals a “Malicious/Suspicious” result, initiating malware scans on all network devices, particularly routers and smart TVs, is recommended.
Users are urged to update device firmware, change admin credentials, and disable unnecessary remote access features to enhance security.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS