Security
Harmful 7-Zip Website Disguises Proxy Tool as Installer

A counterfeit version of the popular archiving software 7-Zip is being distributed through a fake website, leading to the installation of a trojan that transforms the user’s device into a residential proxy node.
Residential proxy networks exploit home user devices to route traffic, aiming to bypass restrictions and carry out malicious activities like credential stuffing, phishing, and malware dissemination.
Following a user’s report, it was discovered that the malicious installer was obtained from a deceptive website posing as the official 7-Zip project, promoted in a YouTube tutorial on PC building. The fraudulent website, 7zip[.]com, is still operational according to BleepingComputer.

The cybercriminal behind this scheme registered the deceptive domain 7zip[.]com, which can easily deceive users into believing they are on the legitimate website.
Furthermore, the attacker replicated the content and structure of the original 7-Zip website located at 7-zip.org.
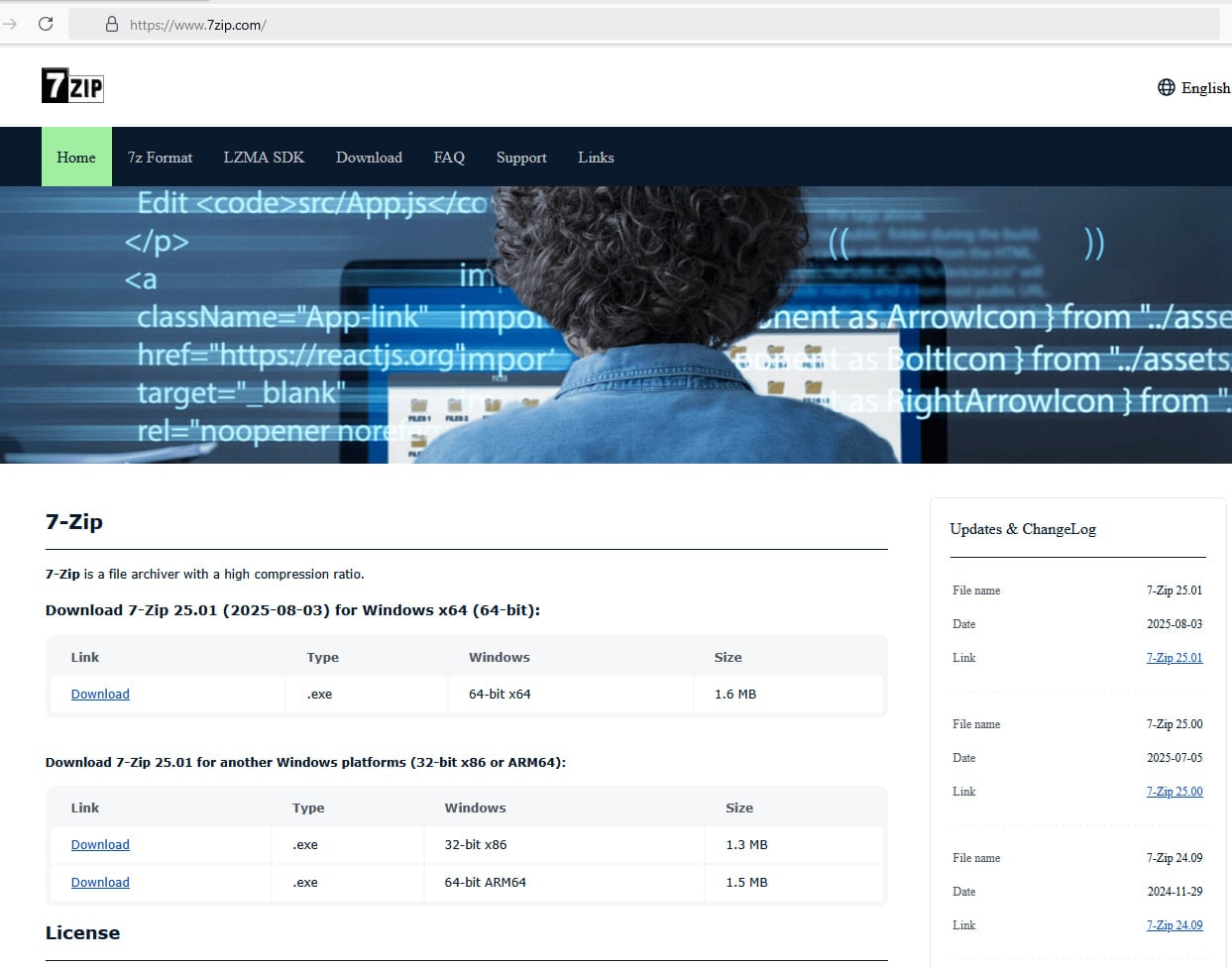
Source: BleepingComputer
Security experts at Malwarebytes analyzed the installer file and discovered that it is signed with a now-revoked certificate issued to Jozeal Network Technology Co., Limited.
The fraudulent copy includes the 7-Zip program, providing regular functionality. However, the installer also deploys three malicious files:
- Uphero.exe – service manager and update loader
- hero.exe – primary proxy payload
- hero.dll – supporting library
These files are placed in the ‘C:\Windows\SysWOW64\hero\’ directory, and a Windows service running as SYSTEM is created for the two malicious executables.
Additionally, the malware modifies firewall rules using ‘netsh’ to enable the binaries to establish inbound and outbound connections.
The infected system is profiled using Windows Management Instrumentation (WMI) and Windows APIs to gather hardware, memory, CPU, disk, and network information, which is then sent to ‘iplogger[.]org.’
Malwarebytes clarifies that while initial signs pointed to backdoor capabilities, further examination revealed that the malware primarily functions as proxyware.
“The compromised host acts as a residential proxy node, allowing third parties to channel traffic through the victim’s IP address,” explains Malwarebytes.
The malware, hero.exe, retrieves configuration from rotating C2 domains with a “smshero” theme, establishing outbound proxy connections on non-standard ports like 1000 and 1002. Control messages are obfuscated using a lightweight XOR key.
Malwarebytes also uncovered that the campaign extends beyond the 7-Zip deception, involving trojanized installers for HolaVPN, TikTok, WhatsApp, and Wire VPN.
The malware utilizes a rotating C2 infrastructure centered around hero/smshero domains, with traffic routed through Cloudflare and transmitted over TLS-encrypted HTTPs.
It leverages DNS-over-HTTPS through Google’s resolver to minimize detection of standard DNS traffic by defenders.
The malware also checks for virtualization platforms like VMware, VirtualBox, QEMU, Parallels, and debuggers to identify analysis attempts.
Following independent security researchers’ findings on the malware’s true intent, Malwarebytes initiated an investigation. Researcher Luke Acha revealed the purpose of the Uphero/hero malware.
The xor-based communication protocol was decoded by s1dhy, confirming the proxy functionality. DFIR engineer Andrew Danis linked the fake 7-Zip installer to a broader campaign impersonating various software brands.
Malwarebytes provides indicators of compromise (domains, file paths, IP addresses) and host-related data observed during their analysis.
Users are advised to avoid clicking URLs from YouTube videos or sponsored search results and instead bookmark the official download portals of frequently used software.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, discover how your team can eliminate hidden manual delays, enhance reliability with automated responses, and construct and expand intelligent workflows using your existing tools.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































