Security
Infiltrating the Cyber Jungle: Chinese Mustang Panda Hackers Unleash Infostealers through CoolClient Backdoor

Mustang Panda, a Chinese cyber espionage group, has recently upgraded its CoolClient backdoor to a new version capable of extracting login information from web browsers and monitoring clipboard activities.
Researchers at Kaspersky have identified that the malware has been enhanced to include a previously unseen rootkit, with a detailed technical analysis expected in an upcoming report.
For some time now, CoolClient has been linked to Mustang Panda and has been utilized as a supplementary backdoor alongside PlugX and LuminousMoth.

The updated version of the malware has been observed in attacks targeting governmental organizations in several countries, including Myanmar, Mongolia, Malaysia, Russia, and Pakistan. These attacks were initiated using legitimate software from Sangfor, a Chinese company specializing in cybersecurity, cloud computing, and IT infrastructure products.
Prior to this, CoolClient operators distributed the malware through DLL side-loading by exploiting signed binaries from reputable sources like Bitdefender, VLC Media Player, and Ulead PhotoImpact.
According to Kaspersky researchers, the CoolClient backdoor is designed to collect information about the compromised system and its users, such as computer name, operating system version, RAM capacity, network details, and descriptions of loaded driver modules.
CoolClient utilizes encrypted .DAT files in a multi-stage execution process and achieves persistence through Registry modifications, addition of new Windows services, and scheduled tasks. It also supports User Account Control (UAC) bypassing and privilege escalation.
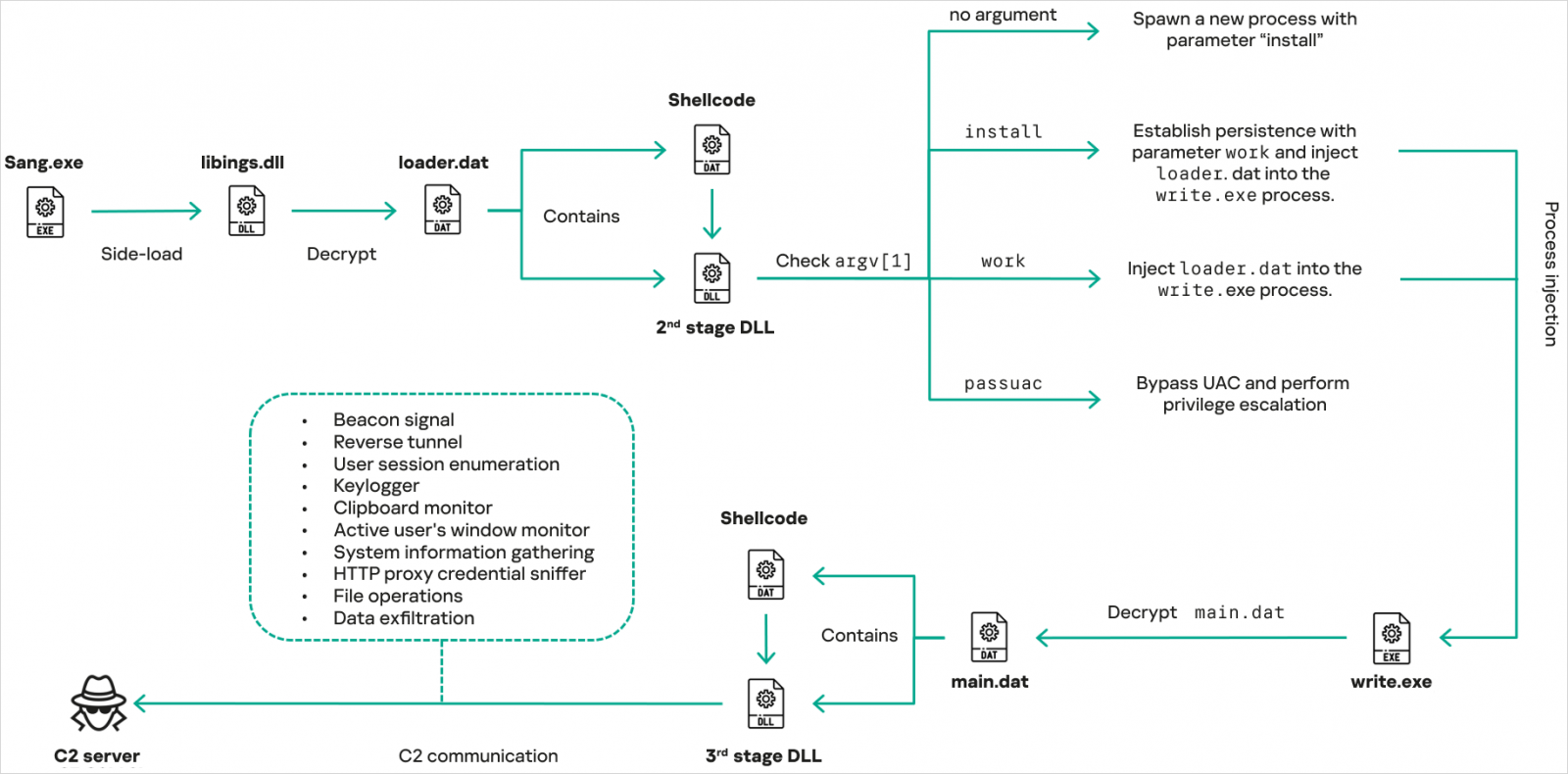
Source: Kaspersky
The key functionalities of CoolClient, such as system and user profiling, file operations, keylogging, TCP tunneling, reverse-proxying, and in-memory execution of dynamically fetched plugins, are present in both old and new versions, but have been refined in the latest iterations.
Notable additions in the recent CoolClient variant include a clipboard monitoring module, active window title tracking, and HTTP proxy credential sniffing utilizing raw packet inspection and headers extraction techniques.
Furthermore, the plugin ecosystem has been expanded to include a dedicated remote shell plugin, a service management plugin, and an enhanced file management plugin.
The service management plugin enables operators to enumerate, create, start, stop, delete, and modify Windows services’ startup configuration, while the file management plugin offers advanced file operations like drive enumeration, file search, ZIP compression, network drive mapping, and file execution.
Remote shell functionality is facilitated through a separate plugin that initiates a hidden cmd.exe process and redirects its standard input and output through pipes, enabling interactive command execution via the command-and-control (C2) channel.
A novel addition to CoolClient’s operations is the deployment of infostealers to extract login data from browsers. Kaspersky has identified three distinct families targeting Chrome (variant A), Edge (variant B), and a versatile variant C that covers any Chromium-based browser.
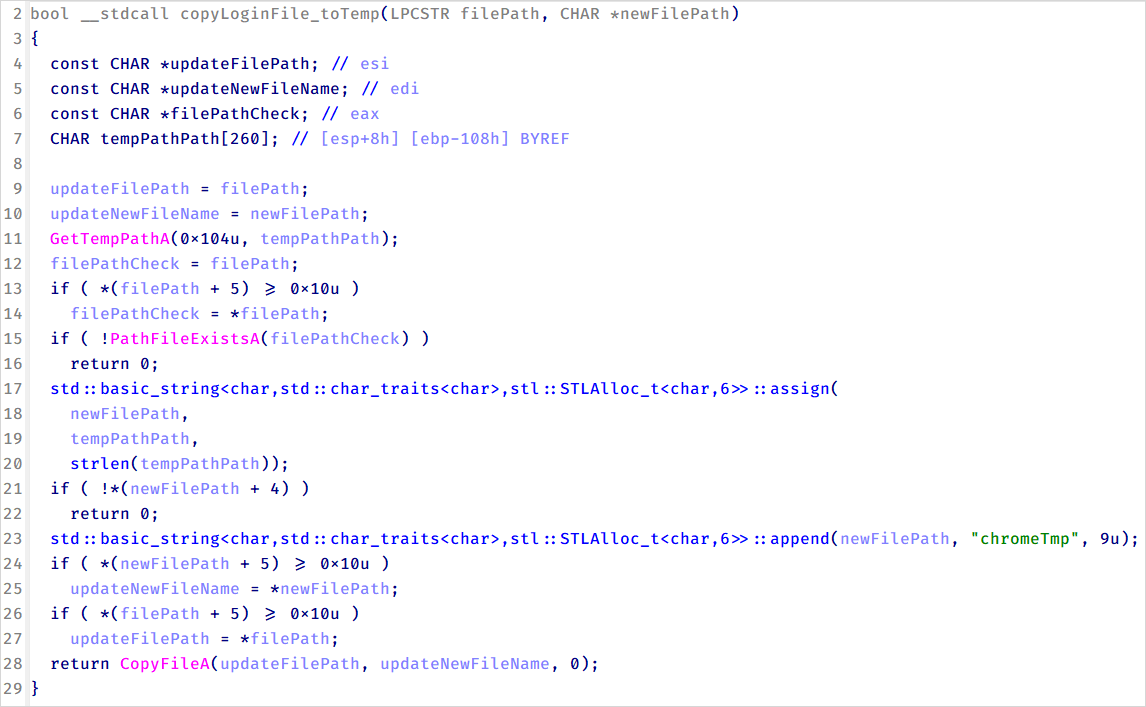
Source: Kaspersky
Another noteworthy shift in operations is the utilization of hardcoded API tokens for legitimate public services like Google Drive or Pixeldrain to evade detection during browser data theft and document exfiltration.
Mustang Panda continues to evolve its toolset and modus operandi. Recently, Kaspersky reported on a new kernel-mode loader that deployed a variant of the ToneShell backdoor on government systems.
Earlier this month, Taiwan’s National Security Bureau identified Mustang Panda as a significant threat to its critical infrastructure, highlighting the group’s prolific and high-volume targeting activities.

As the budget season approaches, more than 300 CISOs and security leaders have shared their strategies, spending plans, and priorities for the upcoming year. This comprehensive report compiles their insights, providing readers with benchmarks, emerging trends, and a comparison of priorities for 2026.
Discover how top leaders are translating investments into measurable impact.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































