Security
Massive Data Breach Exposes Financial Data of 1 Million Figure Accounts

Figure Technology Solutions Breach: Nearly 1 Million Accounts Compromised
In a significant cybersecurity incident, hackers have successfully breached the systems of Figure Technology Solutions, a prominent blockchain-native financial technology company. The breach resulted in the theft of personal and contact information from nearly 1 million accounts.
Established in 2018, Figure Technology Solutions utilizes the Provenance blockchain for various financial activities such as lending, borrowing, and securities trading. The company has facilitated over $22 billion in home equity transactions and has collaborated with more than 250 partners, including banks, credit unions, fintech firms, and home improvement companies.
Despite not publicly disclosing the breach initially, a Figure spokesperson later confirmed that the attackers executed a social engineering attack to access a “limited number of files.”
Upon further inquiry by BleepingComputer, Figure Technology Solutions has not yet provided additional information regarding the breach.
Although the exact number of affected individuals remains undisclosed by Figure, Have I Been Pwned, a notification service, revealed that data from 967,200 accounts was compromised in the attack.
According to Have I Been Pwned, the exposed data, dating back to January 2026, included over 900,000 unique email addresses, along with names, phone numbers, physical addresses, and dates of birth. Figure attributed the incident to a social engineering attack that deceived an employee into granting access to the hackers.
The breach was claimed by the ShinyHunters extortion group, who subsequently leaked 2.5GB of data allegedly obtained from numerous loan applicants on the dark web.
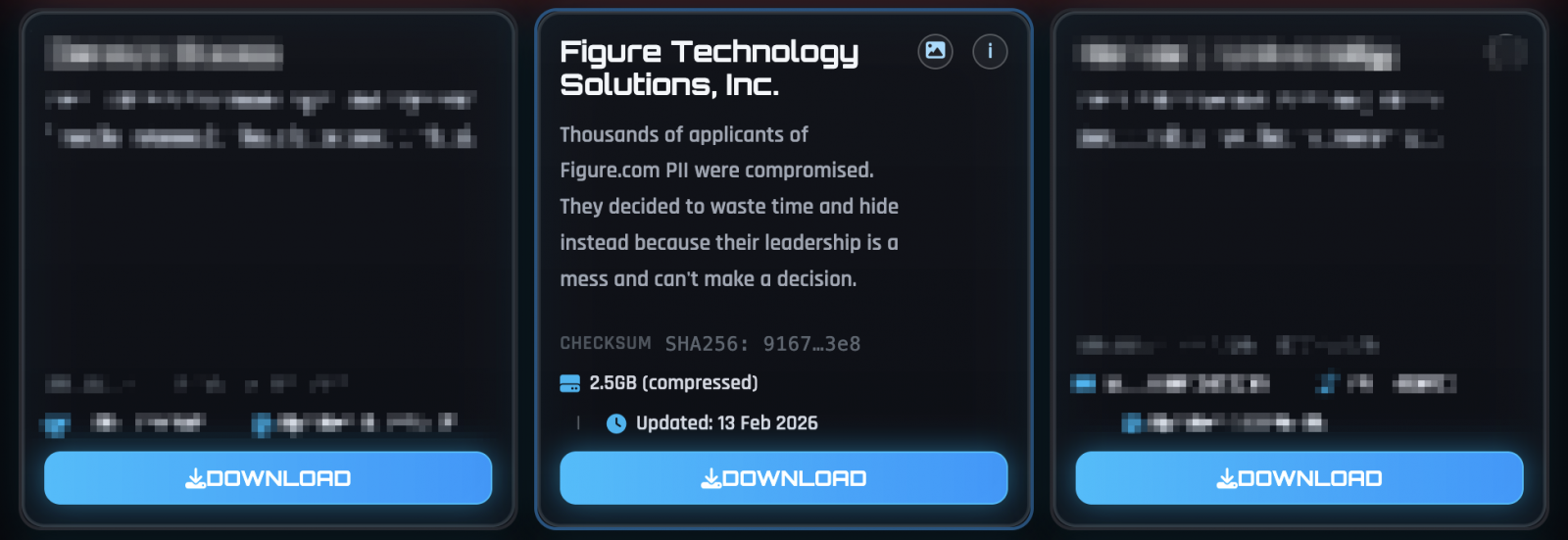
Notably, ShinyHunters has recently claimed responsibility for breaches at several companies, including Canada Goose, Panera Bread, Betterment, SoundCloud, PornHub, and CrowdStrike. While these breaches may not be directly linked, some of the victims were targeted in a voice phishing (vishing) campaign aimed at single sign-on (SSO) accounts of top organizations like Okta, Microsoft, and Google.
By impersonating IT support personnel, the attackers tricked employees into divulging credentials and multi-factor authentication (MFA) codes on phishing sites mimicking their companies’ login portals. This allowed the hackers to access the victims’ SSO accounts and subsequently infiltrate other connected enterprise applications and services.
As part of their campaign, ShinyHunters also breached the online dating giant Match Group, which operates popular services such as Tinder, Hinge, Meetic, Match.com, and OkCupid.

Modern IT infrastructure outpaces manual workflows. Discover how to reduce delays and enhance reliability with automated responses. Learn to build intelligent workflows using existing tools with the new Tines guide.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS