Security
ModeloRAT: Enhancing Browser Security with CrashFix Chrome Extension
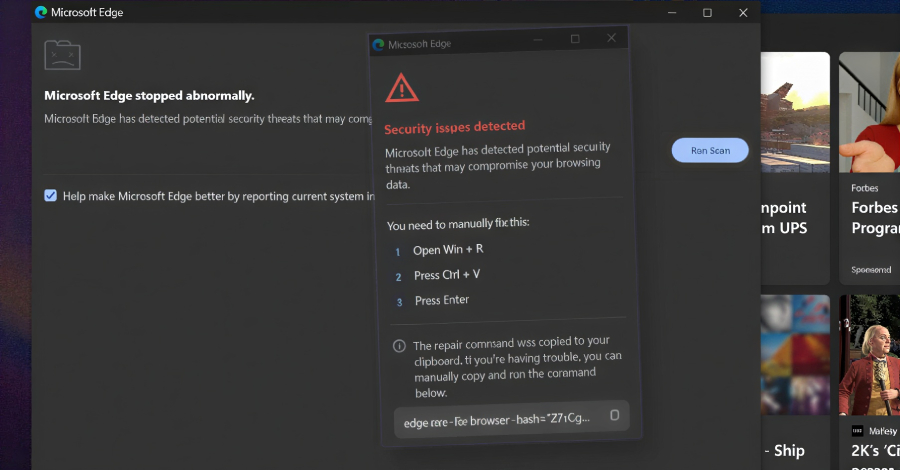
Enhancing Cybersecurity: Understanding KongTuke’s Advanced Tactics
After facing a single communication failure, KongTuke employs a reconnection interval of 150 seconds to resume normal operations, showcasing its resilience in overcoming obstacles.
Recent incidents involving the deployment of ModeloRAT on domain-joined machines reveal KongTuke’s strategic focus on infiltrating corporate environments to gain extensive access. Moreover, users utilizing standalone workstations encounter a complex multi-stage infection process culminating in the reception of a test message “TEST PAYLOAD!!!!” from the C2 server, hinting at a potential testing phase.
The CrashFix campaign by KongTuke serves as a prime example of threat actors adapting their social engineering techniques to exploit vulnerabilities. By masquerading as a reputable open-source project like uBlock Origin Lite, deliberately crashing the user’s browser, and offering a deceptive solution, KongTuke creates a vicious cycle of infection that preys on user frustration.
According to cybersecurity experts, such as the aforementioned cybersecurity company, this campaign underscores the continuous evolution of cyber threats and the need for heightened vigilance. By understanding the modus operandi of threat actors like KongTuke, organizations can bolster their defenses and protect themselves from sophisticated cyber attacks.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS