Security
Nike’s Cybersecurity Crisis: Uncovering the Data Breach and Extortion Scheme

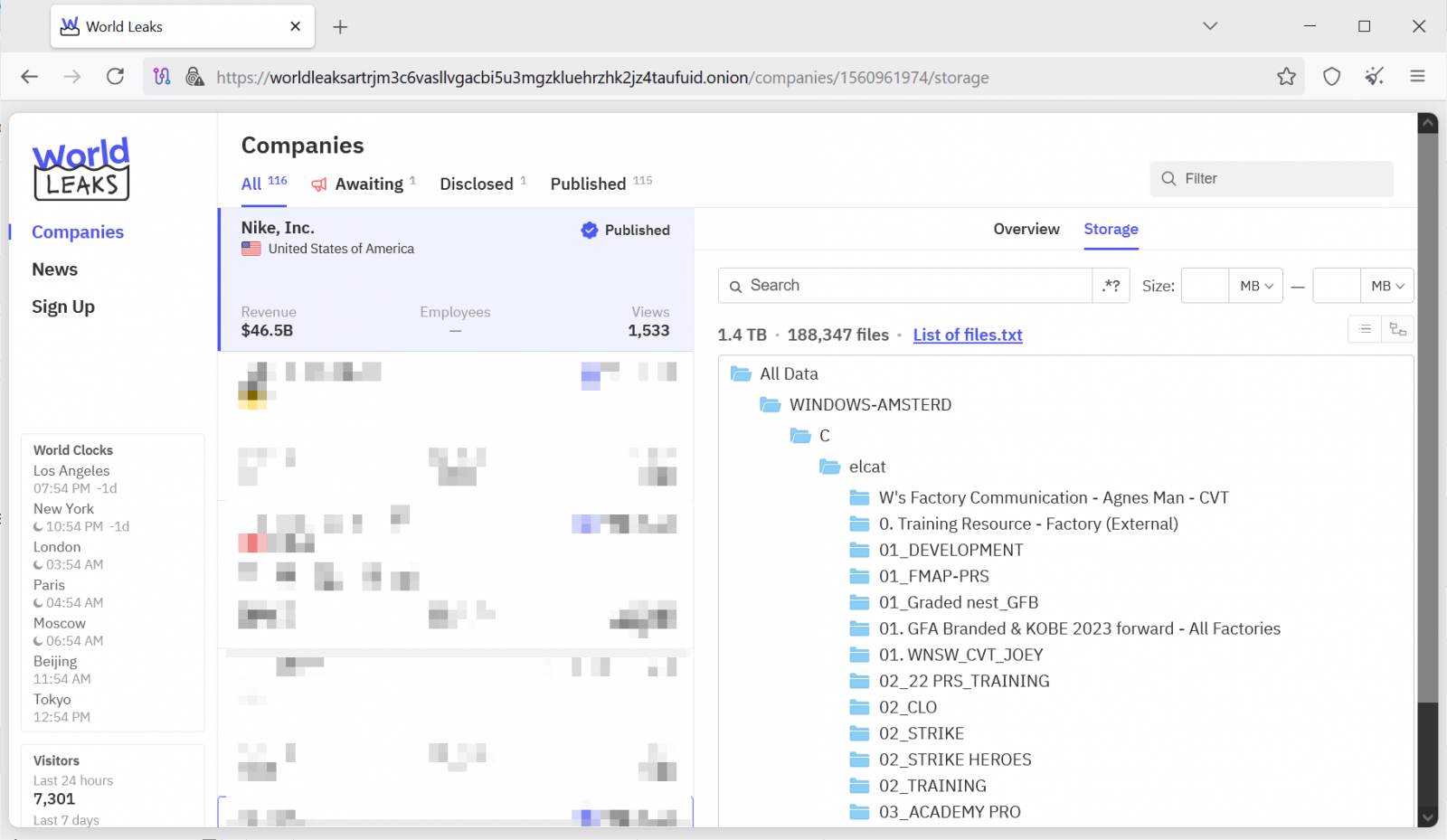
Nike Investigating Potential Cyber Security Incident After Data Leak
Nike is currently looking into what it has described as a “potential cyber security incident” following the release of 1.4 TB of files by the World Leaks ransomware gang. The sportswear giant is taking consumer privacy and data security seriously and is actively assessing the situation.
The extortion group, World Leaks, recently announced that they had acquired nearly 190,000 files containing corporate data related to Nike’s business operations. This information was added to their dark web data-leak site.

Prior to the publication of this article, World Leaks removed the Nike entry from its leak. This action suggests that negotiations may be ongoing between the company and the extortion group, or that Nike has already paid a ransom to have the allegedly stolen documents removed.
Despite these claims by the extortion gang, Nike has not confirmed the data theft. Additionally, BleepingComputer has not been able to independently verify whether the leaked files actually contain legitimate data.
World Leaks is believed to be a rebrand of the Hunters International ransomware group, which transitioned from file encryption to data theft and extortion-only attacks in January 2025. This shift was driven by concerns that traditional ransomware operations were no longer as profitable.
Hunters International, initially identified in late 2023, was suspected of being a possible Hive ransomware rebrand due to code similarities. The group claimed responsibility for over 280 attacks, targeting organizations such as the U.S. Marshals Service, Tata Technologies, Hoya, AutoCanada, and Austal USA.
World Leaks has since exposed data stolen from numerous organizations worldwide on its data leak site. In July, affiliates of the group were linked to breaches on Dell’s product demonstration platforms and the exploitation of end-of-life SonicWall SMA 100 devices to deploy custom OVERSTEP rootkit malware.

Discover how to securely manage old keys and set AI-generated code guardrails with this comprehensive guide. Eliminate guesswork and enhance your team’s security practices.
Download the cheat sheet now for seamless secrets management.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS





























