Security
Preparing for the Storm: Essential Steps for Defense Contractors Before Compliance Enforcement Arrives

The Countdown to CMMC Enforcement: What Contractors Need to Know
The Cybersecurity Maturity Model Certification (CMMC) is no longer a distant concept – enforcement is set to begin in November 2025. For those handling Controlled Unclassified Information (CUI), the time to act is now. This is not just an abstract issue; it affects contracts, revenue, and reputation.
The Department of Defense has laid out clear milestones for CMMC implementation. The final CMMC program rule was published in October 2024 and became effective in December of the same year. The Defense Federal Acquisition Regulation Supplement (DFARS) rule, enabling enforcement, was finalized on September 10, 2025, with enforcement starting on November 10, 2025.
The rollout will happen in phases, with Phase 1 starting in November 2025, Phase 2 in November 2026, and full coverage expected by November 2028.
There is no room for extensions, and many program offices and prime contractors are already seeking evidence of maturity before awarding work. It’s time to view the next few quarters as a countdown, not a debate.
Figure 1: CMMC Timelines 2018 – 2032
The Significance of Recent Changes and Their Impact
The key change with CMMC is the removal of ambiguity. The program rule is finalized and in effect, while the acquisition rule that incorporates CMMC language into contracts is also finalized with a clear enforcement timeline. The phased approach makes the timing explicit.
- Phase 1: Starting November 10, 2025, program offices can choose to include CMMC.
- Phase 2: Beginning November 10, 2026, most organizations handling CUI will need third-party Level 2 assessments.
- Phases 3 and 4 will lead to full coverage by November 10, 2028.
Across the industrial base, this marks the end of a “wait and see” attitude. The capacity challenge remains, and companies must address this constraint effectively.
The Challenge of Capacity in the Industry
The market is facing a shortage of qualified assessors compared to the companies needing Level 2 assessments. Despite efforts to train more assessors, the pipeline cannot expand overnight, leading to backlogs and increased costs. Companies seeking experienced assessors may face longer lead times stretching into quarters.
To navigate this challenge:
- Define the scope first.
- Automate fundamental processes to generate reliable evidence.
- Continuously build evidence as you progress.
- Conduct a readiness review following the assessment guide.
- Address any issues under pressure and schedule an assessment with a C3PAO that suits your organization’s size and structure.
Other Hurdles Slowing Down Implementation
There are three recurring sources of friction in the CMMC implementation process:
Structural separation between consulting and assessment: C3PAOs and advisory firms must maintain a clear separation, adding coordination overhead but ensuring integrity. Effective programs maintain a distinct line between builders and validators.
Workforce and quality: While the number of assessors is increasing, quality remains crucial. Inexperienced assessors or advisors can prolong the assessment process. Choose partners with proven track records and experience similar to your organization’s needs.
Challenges for small businesses: Many Defense Industrial Base (DIB) firms operate with limited IT resources and budgets. They need a strategic approach that allows for gradual implementation without disrupting operations.
Key Governance Lessons and Controversies
The journey towards CMMC has been accompanied by industry activity and governance concerns, with some high-profile controversies. The lesson is clear: anchor compliance efforts in governance, evidence, and reliable partners, not hype or personalities.
Request evidence aligning with the CMMC assessment guide, references from similar-sized companies, and clarity on who conducts the work and signs off on reports. Leadership distractions or scrutiny can jeopardize timelines and reputation.
A Strategic Approach to Achieving Level 2 Compliance
CloudRaider.ai, a boutique company based near Atlanta, offers a methodical approach to addressing the CMMC challenge. Their strategy focuses on making compliance work predictable and routine, as audits reward consistency.
Scope The Environment
Identify where CUI is present, who has access, and how it moves. Minimize complexity by using a dedicated enclave. A smaller scope reduces costs and accelerates the evidence-gathering process.
Design To the Controls
For each NIST SP 800-171 requirement, define technical configurations, operating procedures, and evidence. Link these elements in an evidence register. If you can’t demonstrate it on demand, it’s not sufficient. Develop this capability from the outset.
Automate The Baselines
Automate identity and access management, endpoint configuration, vulnerability scanning, and logging processes to streamline evidence collection and reduce errors.
Sequence Realistically
Prioritize addressing high-risk items first. Implement measures like multifactor authentication, least privilege access, encryption, and logging. Document these processes with timestamps and change records.
Rehearse
Conduct readiness reviews to identify weak areas and practice presenting evidence. This preparation ensures a smoother assessment process.
Essential Criteria for Level 2 Compliance
By the time enforcement begins, a Level 2 organization should be able to demonstrate five key elements:
- A clear scope and System Security Plan (SSP) that outsiders can understand easily, including diagrams and inventories.
- Enforced technical baselines aligning with policies, covering identity, access, endpoint security, encryption, logging, and backups, with mechanisms to detect and correct deviations.
- Defined operating procedures with assigned responsibilities and frequencies, documented runs, and resolution of exceptions.
- A continuous improvement process with findings from various sources feeding into action plans with clear ownership and timelines.
- Evidence packages tailored to assessors’ requirements, containing screenshots, exports, and logs with timestamps and system identifiers.
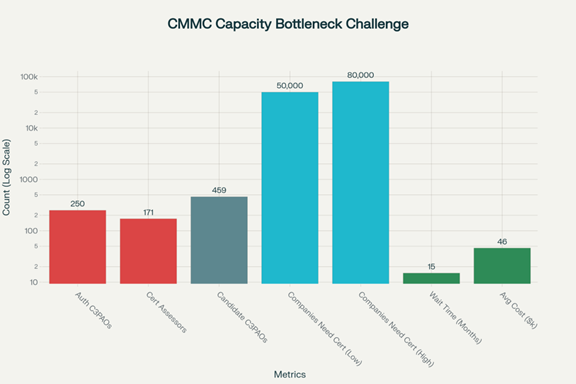
Figure 2: CMMC Capacity Bottleneck Challenge
A Case Study: CloudRaider.ai’s Delivery Approach
CloudRaider.ai emphasizes repeatability in their approach, providing clients with a comprehensive kit that includes playbooks, evidence registers, templates, example screenshots, and procedures. This kit can be customized based on the client’s needs, aiming for a smooth first-pass compliance and a sustainable program.
Operational Discipline and Contracting Strategies
Execution requires coordination with contracting mechanisms to capitalize on opportunities. David Bell from CloudRaider.ai stresses the importance of clear action items and contractual readiness to secure contracts without delays.
CloudRaider.ai’s CEO, Carric Dooley, highlights the significance of leadership focus as timelines tighten. His advice centers on disciplined scoping, automation of critical processes, and readiness rehearsals to ensure a smooth assessment.
Common Pitfalls in Level 2 Programs
- Attempting to address all issues simultaneously: Sequencing tasks is essential to avoid disruptions.
- Emphasizing policy over configuration: Policies alone are insufficient; actual configurations and proofs are crucial.
- Overreliance on multiple tools: Choose fewer platforms with extensive coverage over numerous tools with limited capabilities.
- Outdated evidence: Ensure evidence includes timestamps and identifiers to remain valid.
- Procedural gaps: Implement procedures that are actively used and documented.
- Lack of segregation for CUI: Keep CUI separate to minimize scope and costs.
- Poor service account management: Maintain strict control over service accounts and keys.
- Inconsistent POA&M practices: Track findings with clear owners and deadlines to mitigate risk effectively.
- Delayed engagement with assessors: Involve assessors early in the process to align expectations and avoid surprises.
- Assuming primes will wait for compliance: Private sector entities may move faster than government timelines, so be proactive in meeting requirements.
The 90-Day Execution Checklist
Week 1 to 2: Define the scope, set up tools, draft diagrams, and schedule cleanup tasks.
Week 3 to 4: Implement multifactor authentication, secure service accounts, configure encryption, and test procedures.
Week 5 to 8: Address high-risk issues, set up status dashboards, conduct incident response drills, and expand procedures.
Week 9 to 10: Strengthen weak areas, refine documentation, and prepare control owners for presenting evidence.
Week 11 to 12: Conduct a dress rehearsal, organize evidence, finalize gaps in the POA&M, and secure executive support for the assessment.
Post-Certification Strategy
After achieving certification, organizations must integrate CMMC practices into their standard operations, including metrics, reviews, and budgeting. This sustained effort pays off during recompetitions and complex bidding processes.
Conclusion: Act Now for CMMC Compliance
The clock is ticking for CMMC enforcement, and proactive companies stand to gain better contract opportunities and smoother audits. Partner with lean, evidence-driven organizations, build sustainable compliance kits, and make steady progress towards compliance. The time for action is now.
 Pete Green, the CISO/CTO of Anvil Works, brings over 25 years of IT and cybersecurity experience to the table. With a Master’s in Computer Information Systems from Boston University, Pete has supported clients across various sectors and held leadership roles in cybersecurity.
Pete Green, the CISO/CTO of Anvil Works, brings over 25 years of IT and cybersecurity experience to the table. With a Master’s in Computer Information Systems from Boston University, Pete has supported clients across various sectors and held leadership roles in cybersecurity.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































