Security
Router Traffic Hijacked: The DKnife Linux Toolkit’s Malicious Mission
An innovative toolkit known as DKnife has recently come to light, being utilized since 2019 to intercept traffic at the edge-device level and distribute malware as part of espionage campaigns.
This framework serves as a post-compromise tool for monitoring traffic and engaging in adversary-in-the-middle (AitM) activities. Its primary purpose is to intercept and manipulate traffic directed towards endpoints such as computers, mobile devices, and IoT devices on the network.
According to researchers at Cisco Talos, DKnife is an ELF framework comprising seven Linux-based components specifically designed for deep packet inspection (DPI), traffic manipulation, credential harvesting, and malware dissemination.

The malware exhibits Simplified Chinese language elements in component names and code comments, with a clear focus on targeting Chinese services like email providers, mobile applications, media domains, and WeChat users.
Talos researchers have confidently identified the operator of DKnife as a threat actor linked to China.
Source: Cisco Talos
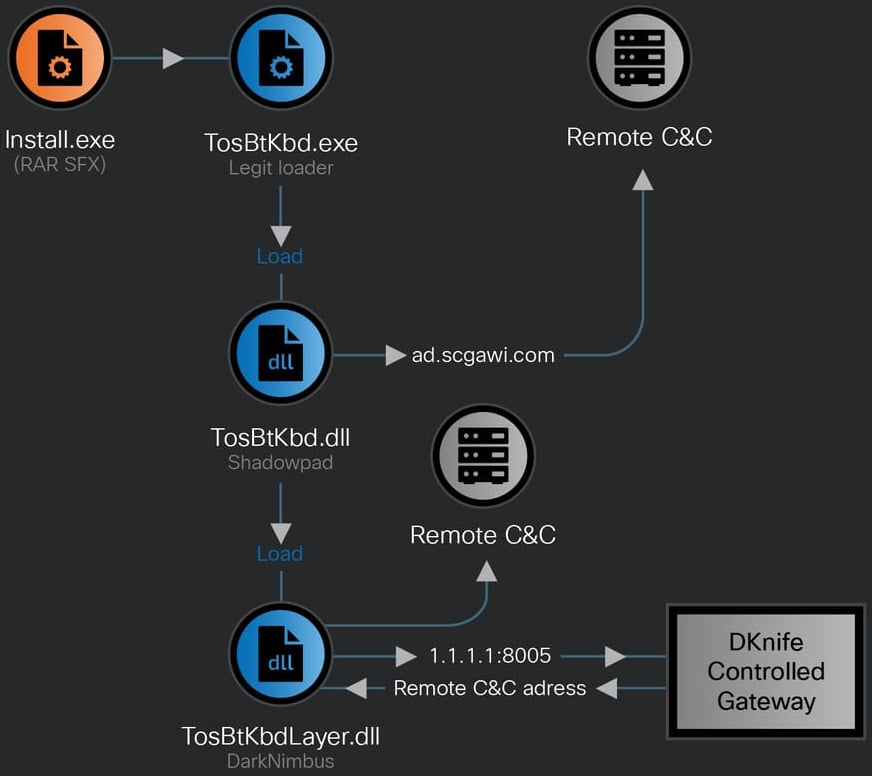
While the exact method of compromising network equipment remains unclear, it has been discovered that DKnife is associated with the delivery and interaction of the ShadowPad and DarkNimbus backdoors, both commonly linked to Chinese threat actors.
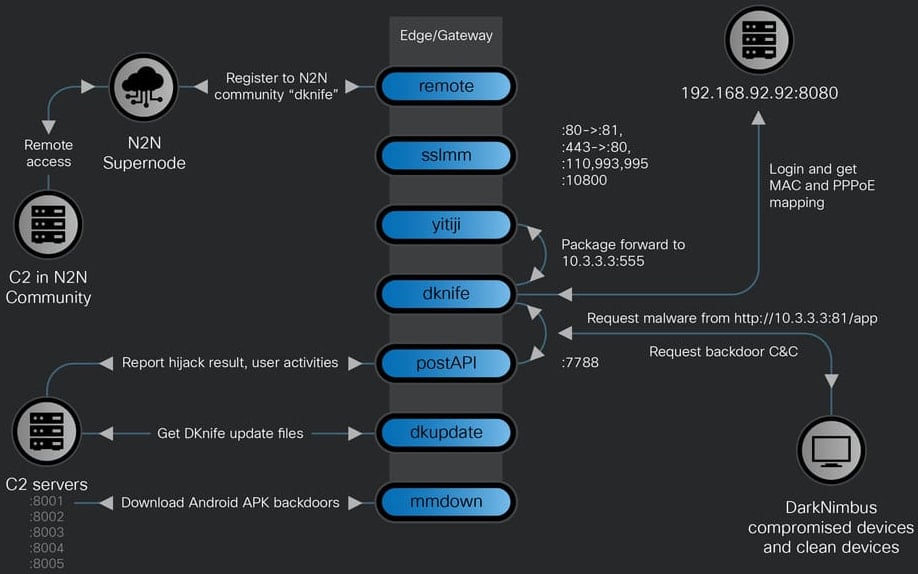
DKnife comprises seven modules, each dedicated to specific tasks related to communication with C2 servers, relaying or altering traffic, and concealing the origin of malicious traffic:
- dknife.bin – responsible for packet inspection, attack logics, reporting attack status, user activities, and data collection
- postapi.bin – acts as a relay component between DKnife.bin and C2 servers
- sslmm.bin – a custom reverse proxy server derived from HAProxy
- yitiji.bin – creates a virtual Ethernet interface (TAP) on the router to route the attacker’s traffic within the LAN
- remote.bin – functions as a peer-to-peer VPN client using n2n VPN software
- mmdown.bin – responsible for downloading and updating Android APK files
- dkupdate.bin – facilitates the download, deployment, and updating of DKnife components
“Its [DKnife’s] key capabilities include serving as an update C2 for backdoors, DNS hijacking, hijacking Android application updates and binary downloads, delivering ShadowPad and DarkNimbus backdoors, selectively disrupting security-product traffic, and exfiltrating user activity to remote C2 servers,” as reported by the researchers.
Upon installation, DKnife utilizes its yitiji.bin component to establish a bridged TAP interface on the router at the IP address 10.3.3.3. This enables threat actors to intercept and modify network packets en route to their intended destination.
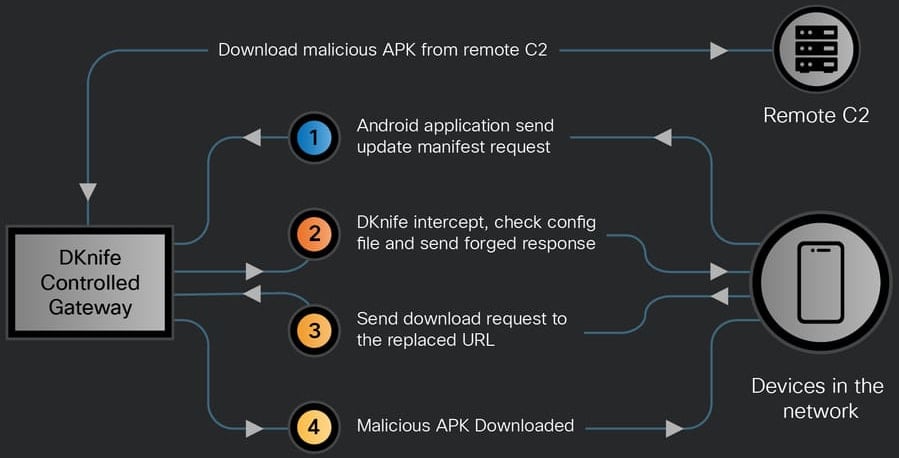
This functionality allows DKnife to distribute malicious APK files to mobile devices or Windows systems within the network.
Cisco researchers have observed DKnife deploying the ShadowPad backdoor for Windows, signed with a certificate from a Chinese company. Subsequently, the DarkNimbus backdoor is introduced. On Android devices, the backdoor is directly delivered by DKnife.
Source: Cisco Talos
Within the same infrastructure associated with DKnife activities, researchers have identified the presence of the WizardNet backdoor, previously associated with the Spellbinder AitM framework by ESET researchers.
In addition to payload distribution, DKnife boasts the following capabilities:
- DNS hijacking
- Hijacking Android app updates
- Hijacking Windows binaries
- Credential harvesting through POP3/IMAP decryption
- Hosting phishing pages
- Disrupting anti-virus traffic
- Monitoring user activities, including messaging app usage (WeChat and Signal), map app usage, news consumption, calls, ride-hailing, and shopping
Specifically, WeChat activities are meticulously monitored, with DKnife tracking voice and video calls, text messages, image exchanges, and articles read on the platform, as outlined by Cisco Talos.
Source: Cisco Talos
User activity events are initially routed internally between DKnife’s components and then exfiltrated through HTTP POST requests to designated command-and-control (C2) API endpoints.
By residing on gateway devices and monitoring events as packets traverse the network, DKnife enables real-time monitoring of user activities and data collection.
As of January 2026, the DKnife C2 servers remain operational, with Cisco Talos releasing a comprehensive list of indicators of compromise (IoCs) associated with this malicious activity.

Modern IT infrastructure moves faster than manual workflows can handle.
Discover how your team can reduce hidden manual delays, enhance reliability through automated responses, and create intelligent workflows using existing tools in this new Tines guide.
Transform the following:
Original: She was unable to attend the meeting due to illness.
Transformed: Due to illness, she was unable to attend the meeting.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































