Security
Safeguarding Cloud Security: Mandiant Exposes ShinyHunters’ SSO Exploits

Mandiant says a wave of recent ShinyHunters SaaS data-theft attacks is being fueled by targeted voice phishing (vishing) attacks and company-branded phishing sites that steal single sign-on (SSO) credentials and multi-factor authentication (MFA) codes.
As first reported by BleepingComputer, threat actors are impersonating corporate IT and helpdesk staff and calling employees directly, claiming that MFA settings need to be updated. During the call, the targeted employee is directed to a phishing site that resembles their company’s login portal.
According to Okta, these sites are using advanced phishing kits that allow threat actors to display interactive dialogs while on the phone with a victim.

While still talking to a targeted employee, the attacker relays stolen credentials in real-time, triggers legitimate MFA challenges, and tells the target how to respond, including approving push notifications or entering one-time passcodes.
This allows attackers to successfully authenticate with stolen credentials and enroll their devices in MFA.
Once they gain access to an account, they log in to an organization’s Okta, Microsoft Entra, or Google SSO dashboard, which acts as a centralized hub listing all SaaS applications the user has permission to access.

These applications include Salesforce, a primary target of ShinyHunters, Microsoft 365, SharePoint, DocuSign, Slack, Atlassian, Dropbox, Google Drive, and many other internal and third-party platforms.
For threat actors focused on data theft and extortion, the SSO dashboard becomes a springboard to a company’s cloud data, allowing them to access multiple services from a single compromised account.
The ShinyHunters extortion group confirmed to BleepingComputer that they and some of their affiliates are behind these attacks. The extortion group also claims that other threat actors have since conducted similar attacks.
Soon after the information about these attacks became public, the ShinyHunters extortion gang launched a data-leak site, where it began leaking data associated with these attacks.
Today, Google Threat Intelligence Group/Mandiant released a report saying it is tracking this activity across different threat clusters tracked as UNC6661, UNC6671, and UNC6240 (ShinyHunters).
Multiple threat actors are conducting attacks
Mandiant says UNC6661 poses as IT staff when calling targeted employees and directs them to company-branded phishing domains used to capture SSO credentials and MFA codes. After logging in, the attackers registered their MFA device to retain access.
They used this access to steal data from cloud applications based on whatever permissions were available through the compromised SSO session.
Understanding Recent Vishing Attacks by Threat Actors
Recent reports from Mandiant have shed light on the opportunistic nature of ongoing cyber attacks, with threat actors focusing on exploiting various Software as a Service (SaaS) applications available in the digital landscape.
While Mandiant’s analysis points towards a broad opportunistic approach, it’s worth noting that ShinyHunters, a notorious cybercriminal group, has expressed a specific interest in targeting Salesforce data.
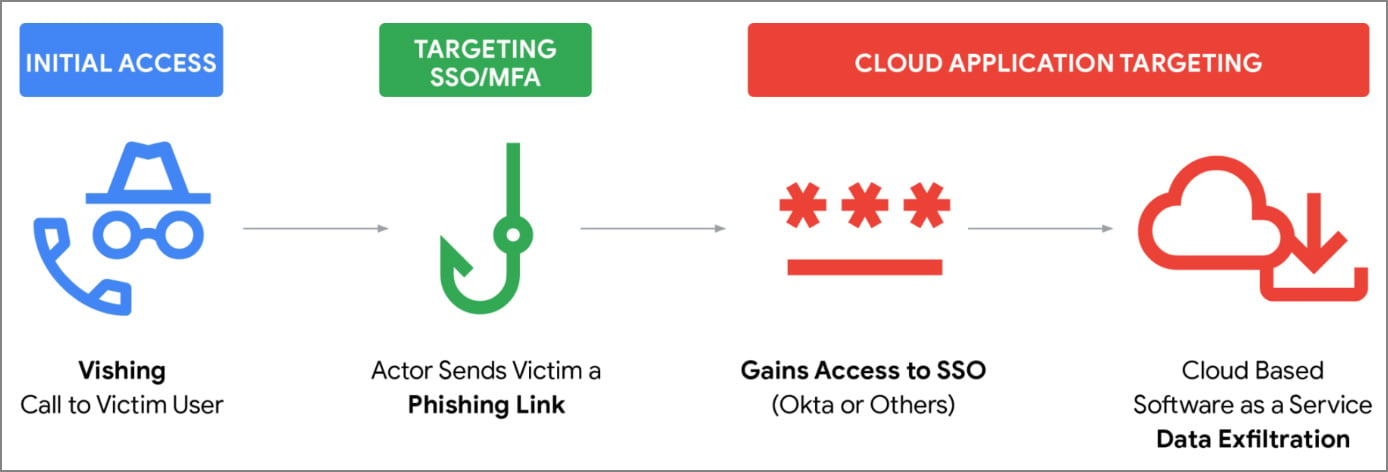
Source: Mandiant
During these attacks, Mandiant has observed various patterns of malicious activities, such as:
- Microsoft 365 and SharePoint events indicating file downloads using PowerShell, suggesting the use of scripts or tools for data exfiltration.
- Salesforce login activities originating from IP addresses associated with the threat actors.
- DocuSign audit logs revealing bulk document downloads linked to similar Indicators of Compromise (IOCs).
In a specific incident involving an Okta customer, the attackers leveraged a Google Workspace add-on called “ToogleBox Recall” to search for and delete emails as a means to cover their tracks.
Mandiant highlights the elaborate tactics employed by threat actors, such as deleting crucial emails related to security notifications to prevent detection of unauthorized access.
Furthermore, the domain names utilized in these attacks typically follow a consistent naming convention, incorporating variations like <companyname>sso.com or <companyname>internal.com.
While the initial breach and data theft activities are attributed to a threat group labeled as UNC6661, Mandiant identifies ShinyHunters (also known as UNC6240) as the entity behind extortion demands, utilizing a Tox messenger ID for communication.
Source: Mandiant
Another threat cluster identified as UNC6671 has been noted for employing similar vishing techniques, albeit with distinct characteristics in their approach, including aggressive pressure tactics and harassment towards targeted organizations.
Mandiant emphasizes the importance of detecting and responding to such attacks promptly by outlining specific behavior indicators, such as SSO account compromises, PowerShell activities, and unusual Google Workspace authorizations.
To fortify defenses against these evolving threats, Mandiant offers comprehensive guidance on enhancing identity workflows, implementing robust logging mechanisms, and deploying effective detection strategies to thwart post-vishing data theft attempts.
Additionally, Mandiant provides specialized rules for Google Security Operations (SecOps) teams to identify and mitigate ShinyHunters’ malicious activities effectively.
Protecting Against Emerging Threats
As organizations navigate the complex cyber threat landscape, it is imperative to stay vigilant and proactive in safeguarding sensitive data and digital assets. By staying informed about the latest attack trends and adopting recommended security measures, businesses can enhance their resilience against cyber threats.
It is crucial for organizations to prioritize cybersecurity measures and invest in robust security solutions to mitigate risks posed by sophisticated threat actors. By fostering a culture of cybersecurity awareness and readiness, businesses can effectively combat evolving cyber threats and safeguard their operations.
Stay informed, stay vigilant, and stay secure.
-

 Facebook3 months ago
Facebook3 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS





























