Security
Signal and WhatsApp Messages at Risk: The Dangerous Multi-Threat Android Malware Sturnus

A recent discovery in the realm of Android threats is the emergence of a sophisticated banking trojan known as Sturnus. This malware has the capability to intercept communications from end-to-end encrypted messaging platforms such as Signal, WhatsApp, and Telegram while also gaining complete control over the infected device.
Despite still being in the developmental phase, Sturnus is fully operational and specifically designed to target accounts at various financial institutions across Europe using region-specific overlay templates.
Setting itself apart from existing Android malware families, Sturnus utilizes a combination of plaintext, RSA, and AES-encrypted communication with its command-and-control (C2) server, making it a more advanced and potent threat.

Complete Takeover of Android Devices
An analysis by online fraud prevention and threat intelligence solutions provider ThreatFabric reveals that Sturnus can pilfer messages from secure messaging applications by capturing decrypted content directly from the device screen.
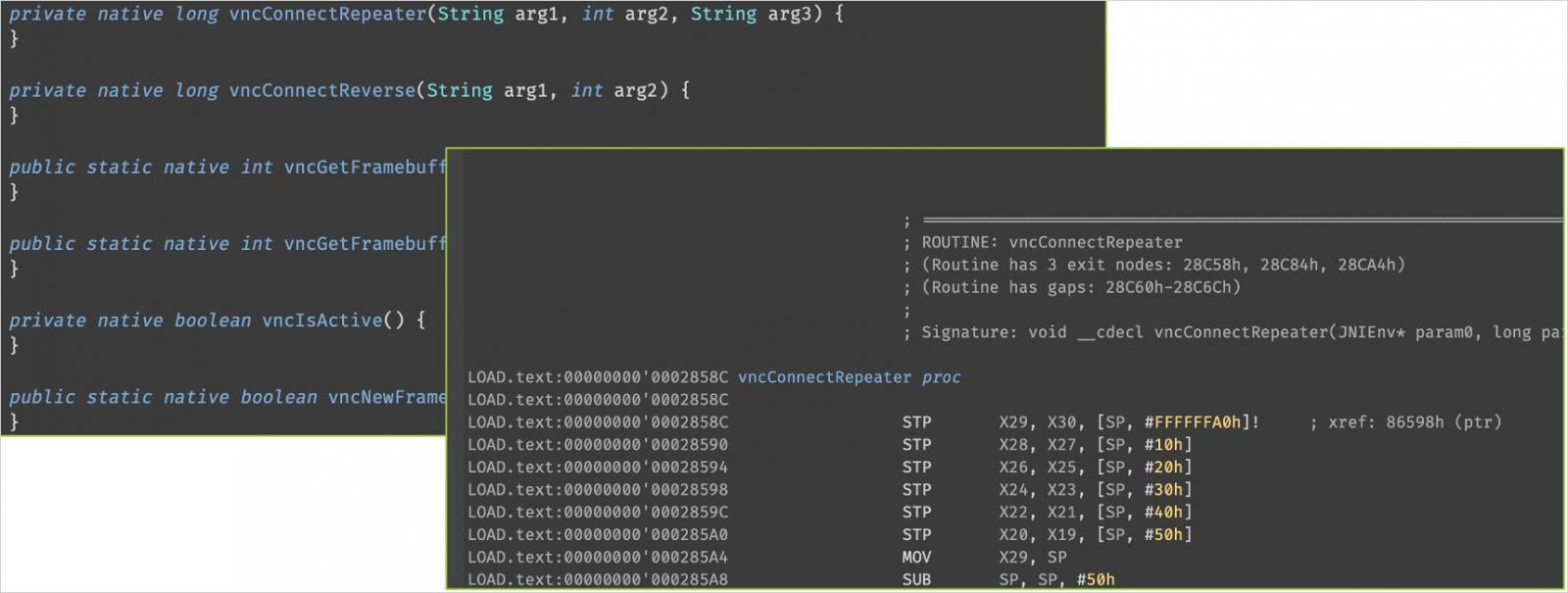
Moreover, the malware is adept at stealing banking credentials through HTML overlays and also supports real-time remote control via VNC sessions.
According to ThreatFabric’s report, Sturnus is likely disguised as legitimate applications such as Google Chrome or Preemix Box. However, the distribution method of the malware remains undisclosed by researchers.
Upon installation, the malware connects to the C2 infrastructure to enroll the victim through a cryptographic exchange process.
It establishes secure communication channels, including an encrypted HTTPS channel for commands and data extraction, as well as an AES-encrypted WebSocket channel for live VNC operations and monitoring.
By leveraging Accessibility services on the infected device, Sturnus gains the ability to read on-screen text, capture user inputs, analyze the UI structure, monitor app launches, simulate button presses, scroll through content, insert text, and navigate the device.
To gain complete control over the device, Sturnus acquires Android Device Administrator privileges, enabling it to monitor password changes, unlock attempts, and remotely lock the device.
The malware also employs tactics to prevent users from revoking its privileges or uninstalling it from the device.
“Until its administrator rights are manually revoked, both ordinary uninstallation and removal through tools like ADB are blocked, giving the malware strong protection against cleanup attempts” – ThreatFabric
When users interact with messaging apps like WhatsApp, Telegram, or Signal, Sturnus utilizes its permissions to extract message content, typed text, contact details, and conversation threads.
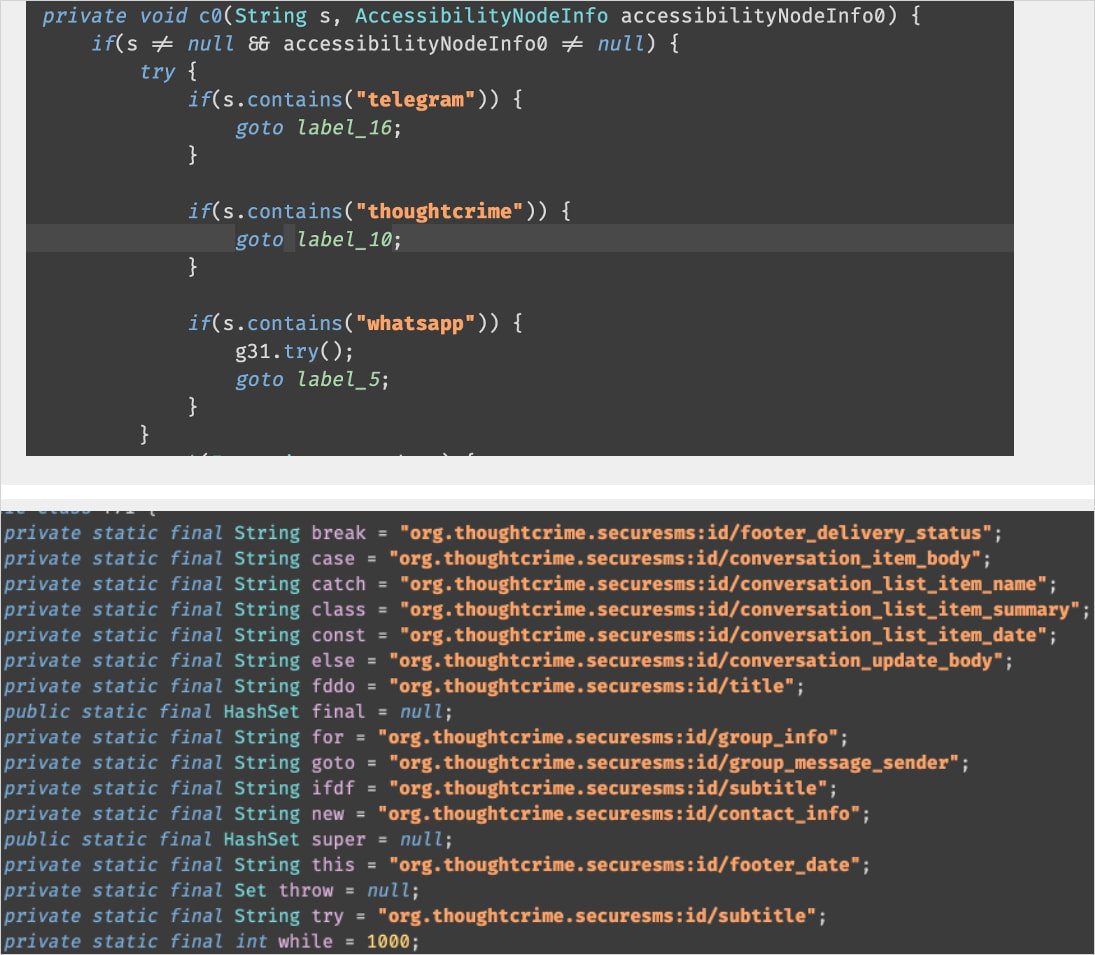
Source: Threat Fabric
By relying on Accessibility Service logging instead of network interception, Sturnus can intercept all on-screen content, including contacts, complete conversations, and message contents in real-time, bypassing end-to-end encryption.
The VNC mode allows attackers to remotely interact with the device, performing actions such as clicking buttons, entering text, scrolling, and navigating the phone’s operating system and applications, all facilitated by Accessibility features.
Source: Threat Fabric
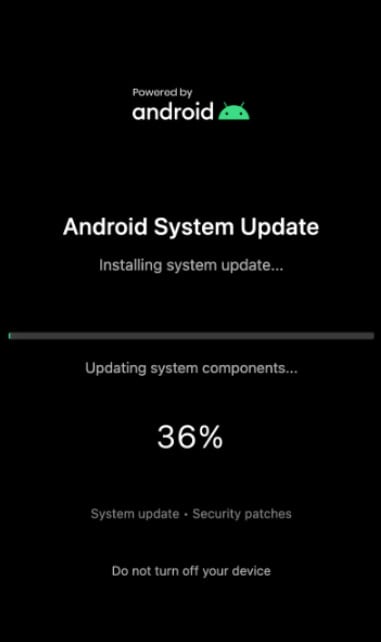
During malicious activities, attackers can overlay a black screen to conceal their actions, which may include unauthorized money transfers, confirming prompts, bypassing multi-factor authentication, modifying settings, or installing additional apps.
ThreatFabric’s report showcases an example of an overlay mimicking a fake Android System Update screen to mask fraudulent operations being executed discreetly.
Source: Threat Fabric
Although still in its initial stages of development, Sturnus has been observed in sporadic attacks, indicating potential testing phases rather than large-scale campaigns. However, its advanced feature set and scalable architecture position it as a significant threat.
ThreatFabric’s monitoring has detected Sturnus activity primarily targeting users in Southern and Central Europe in limited volumes, hinting at preliminary testing by threat actors for future expansive operations.
To mitigate the risk posed by such threats, Android users are advised to refrain from downloading APK files from unofficial sources, maintain active Play Protect security features, and exercise caution when granting Accessibility permissions to applications.

As organizations plan their budgets, security leaders can benefit from insights shared by over 300 CISOs on planning, spending, and prioritizing for the upcoming year. This comprehensive report offers a benchmark for strategies, trends, and priorities in the evolving cybersecurity landscape of 2026.
Discover how industry leaders are translating investments into tangible results.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS