Security
Silent Surveillance: How Predator Spyware Conceals Mic and Camera Activity on iOS SpringBoard

Predator Spyware Hooks iOS SpringBoard to Conceal Mic and Camera Activity
Intellexa’s Predator spyware has the capability to conceal iOS recording indicators while surreptitiously streaming camera and microphone feeds to its operators.
The malware does not exploit any vulnerabilities in iOS but rather utilizes previously acquired kernel-level access to manipulate system indicators that would typically expose its surveillance activities.
Apple introduced recording indicators on the status bar in iOS 14 to notify users when the camera or microphone is in use, denoted by a green or orange dot, respectively.
US-sanctioned surveillance firm Intellexa developed the Predator commercial spyware, deploying it through attacks that exploited Apple and Chrome zero-day flaws and 0-click infection methods.
While the spyware’s ability to suppress camera and microphone activity indicators is well-documented, the specific mechanism behind this functionality was previously unclear.

Source: Jamf
How Predator Conceals Recording Activity
Researchers at mobile device management company Jamf conducted an analysis of Predator samples, uncovering the process by which it hides privacy-related indicators.
According to Jamf, Predator conceals all recording indicators on iOS 14 by utilizing a single hook function (‘HiddenDot::setupHook()’) within SpringBoard, triggering the method whenever sensor activity changes (such as camera or microphone activation).
By intercepting this function, Predator prevents sensor activity updates from reaching the UI layer, thereby preventing the green or red dot from appearing.
“The target method _handleNewDomainData: is called by iOS whenever sensor activity changes – camera turns on, microphone activates, etc.,” explained Jamf researchers.
“By hooking this single method, Predator intercepts ALL sensor status updates before they reach the indicator display system.”
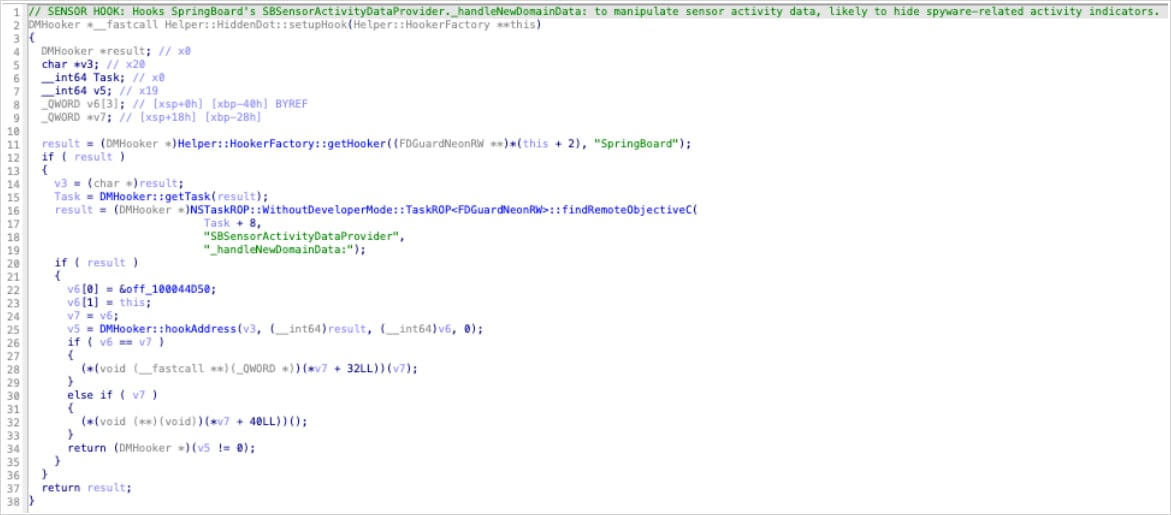
Source: Jamf
The hook functions by neutralizing the object responsible for sensor updates (SBSensorActivityDataProvider in SpringBoard). In Objective-C, calls to a null object are disregarded, preventing SpringBoard from processing camera or microphone activation and thus no indicator is displayed.
As SBSensorActivityDataProvider consolidates all sensor activity, this single hook disables both the camera and microphone indicators.
Additionally, researchers discovered “dead code” that attempted to hook ‘SBRecordingIndicatorManager’ directly. Although this does not execute, it likely represents an earlier development path that was abandoned in favor of the more effective approach that intercepts sensor data upstream.
For VoIP recordings supported by Predator, the associated module lacks an indicator suppression mechanism and relies on the HiddenDot function for stealth.
Jamf further explained that camera access is facilitated through a separate module that identifies internal camera functions using ARM64 instruction pattern matching and Pointer Authentication Code (PAC) redirection to bypass camera permission checks.
With no indicators lighting up on the status bar, the spyware’s activities remain completely concealed from the average user.
Jamf highlighted that technical analysis reveals signs of malicious processes, such as unexpected memory mappings or exception ports in SpringBoard and mediaserverd, breakpoint-based hooks, and audio files written by mediaserverd to atypical paths.
BleepingComputer reached out to Apple for a comment on Jamf’s findings, but the company did not respond.

Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook3 months ago
Facebook3 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS