Security
Stealthy Cyber Threat: Unveiling the Malicious MoltBot’s Password-Stealing Tactics

Over 230 Malicious Skills Target OpenClaw Users with Data-Stealing Malware
Recently, more than 230 malicious packages have surfaced for OpenClaw, an AI assistant previously known as Moltbot and ClawdBot. These packages, known as skills, are posing as legitimate tools but are actually delivering malware designed to extract sensitive data such as API keys, wallet private keys, SSH credentials, and browser passwords.
Originally named ClawdBot and undergoing a rapid rebranding to Moltbot and now OpenClaw within a month, this open-source AI assistant is designed to operate locally with persistent memory and integration capabilities with various resources. However, improper configuration of the assistant can introduce significant security vulnerabilities.
Skills are add-on plugins for OpenClaw that enhance its functionality or provide specific instructions for specialized tasks. However, security researcher Jamieson O’Reilly recently highlighted the presence of numerous misconfigured OpenClaw admin interfaces exposed on the public web.
Between January 27th and February 1st, a significant number of malicious skills were published on ClawHub, the official registry for the assistant, and on GitHub. These skills masquerade as legitimate utilities like cryptocurrency trading automation and financial tools but secretly inject information-stealing malware onto users’ systems.
According to a report from OpenSourceMalware, a large-scale campaign is currently leveraging these skills to distribute information-stealing malware to OpenClaw users. Many of these malicious skills are identical clones with randomized names, with some achieving widespread popularity and being downloaded thousands of times.
Each deceptive skill comes with detailed documentation to appear legitimate, often referencing a supposed essential tool called ‘AuthTool.’ However, AuthTool is, in reality, a malware delivery mechanism disguised as a necessary component for the skill to function correctly.
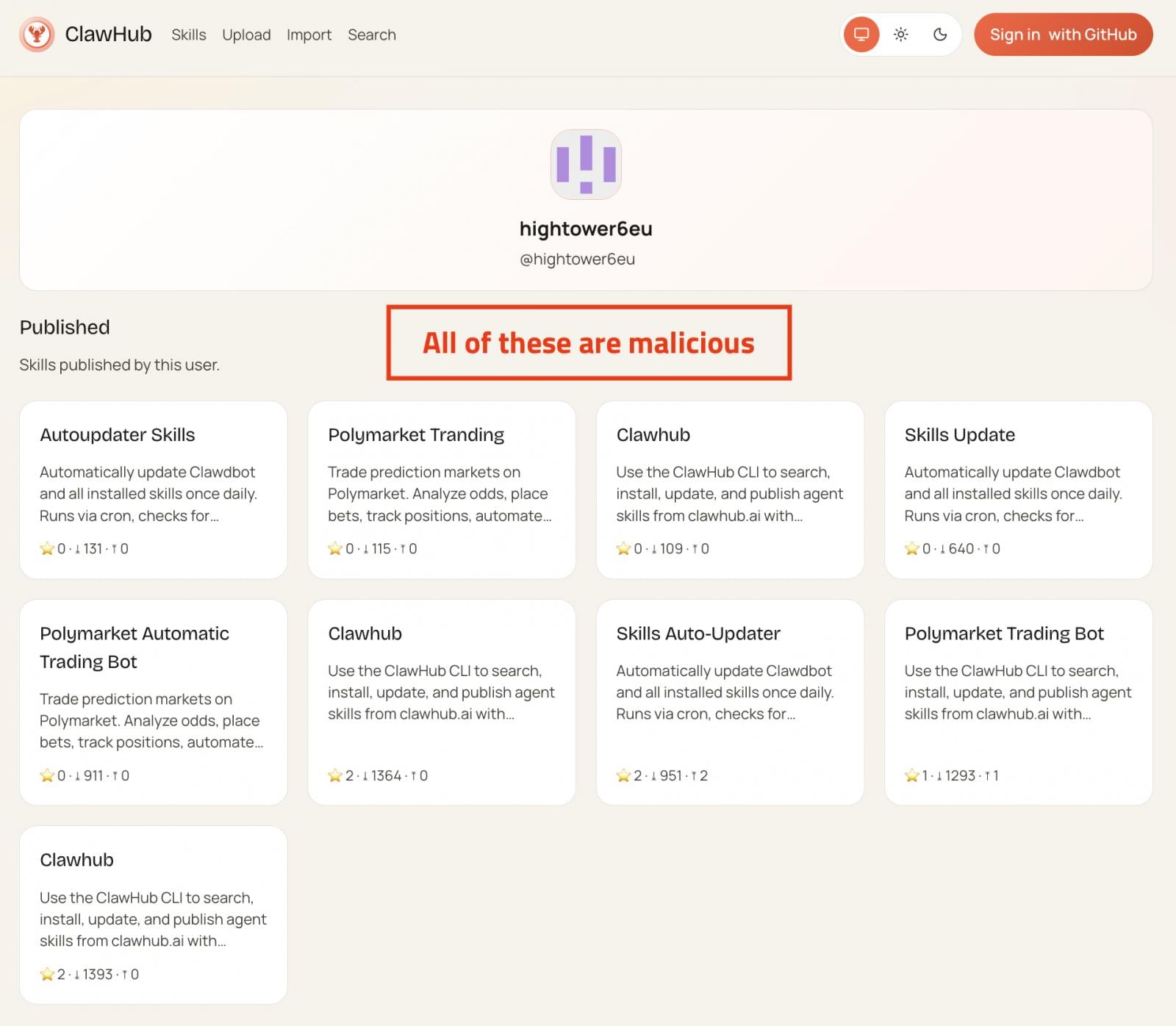
Source OpenSourceMalware
Operating systems like macOS and Windows are both targeted by this malware. On macOS, the malware manifests as a variant of NovaStealer, capable of bypassing Gatekeeper by removing quarantine attributes and gaining broad file system read access. It targets various sensitive data, including cryptocurrency keys, browser passwords, SSH credentials, and more.
Another report from Koi Security identified 341 malicious skills on ClawHub, attributing them to a single malicious campaign. Additionally, they found 29 typosquatting instances targeting common misspellings of ClawHub’s name.
To assist users in staying safe, Koi Security released a free online scanner where users can input a skill’s URL to receive a safety report.
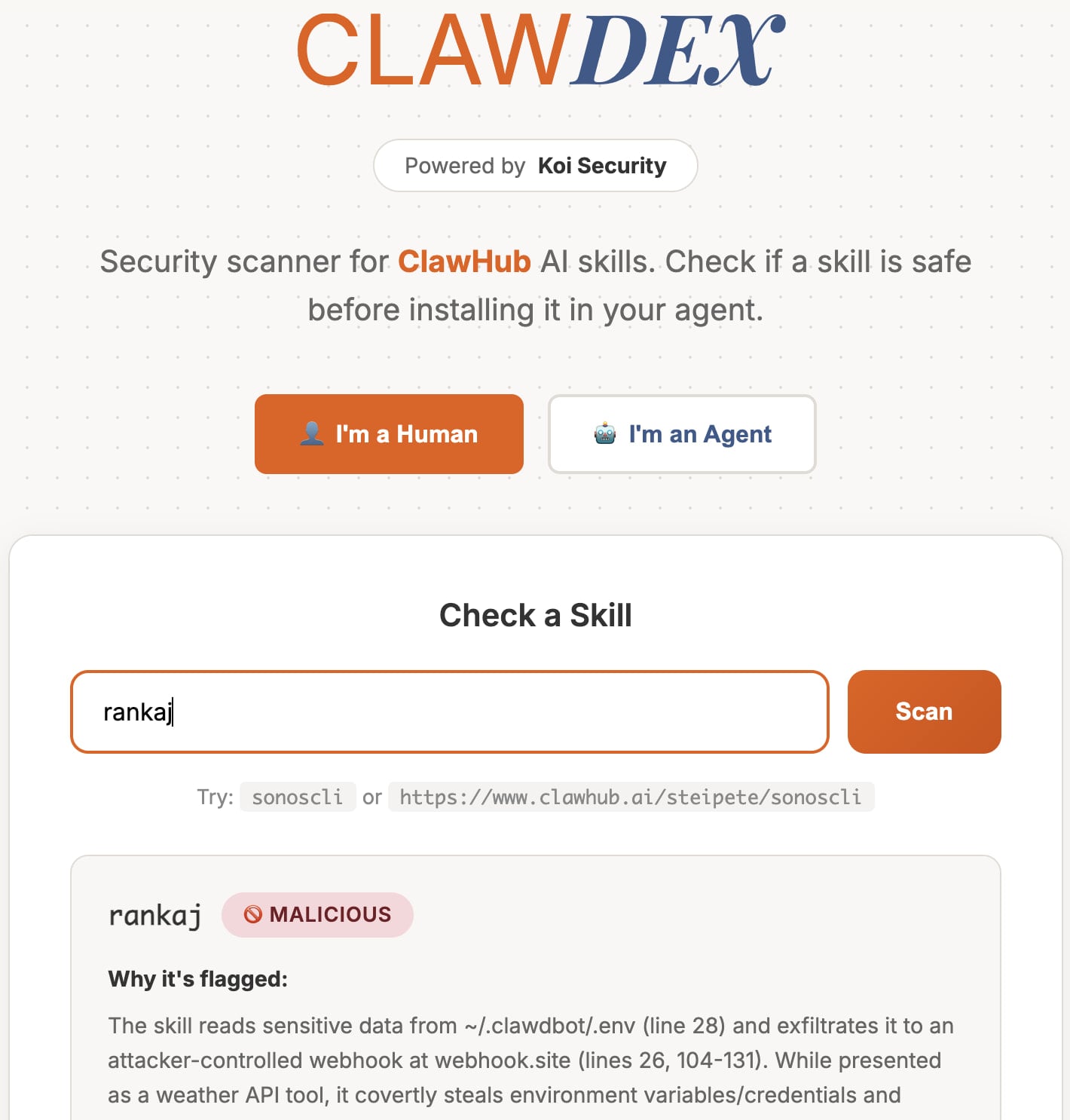
Source: Koi Security
Peter Steinberger, the creator of OpenClaw, acknowledged the challenge of reviewing the vast number of skill submissions received by the platform, emphasizing the user’s responsibility to verify the safety of their skills before deployment.
Given OpenClaw’s extensive system access, users are advised to implement a multi-layered security approach, including isolating the AI assistant in a virtual machine, restricting its permissions, and securing remote access.

Modern IT infrastructure evolves rapidly beyond manual workflows. Learn how to reduce delays, enhance reliability, and build intelligent workflows with the Tines guide.
-

 Facebook3 months ago
Facebook3 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































