Security
Uncovering the Threat: BadAudio Malware Unveiled in APT24 Espionage Operations

A cyber espionage campaign linked to China, known as APT24, has been utilizing a newly discovered malware named BadAudio over the course of a three-year operation. Recently, the group has shifted to more advanced attack methods.
Since 2022, BadAudio has been distributed to targets through various means, including spearphishing, supply-chain compromise, and watering hole attacks.
Evolution of the Campaign
Between November 2022 and September 2025, APT24 compromised over 20 legitimate public websites across different domains to insert malicious JavaScript code that targeted specific visitors, particularly those using Windows systems.

Researchers at Google Threat Intelligence Group (GTIG) have identified that the malicious script employed by APT24 fingerprinted visitors deemed as targets and displayed a fake software update prompt to entice them into downloading BadAudio.
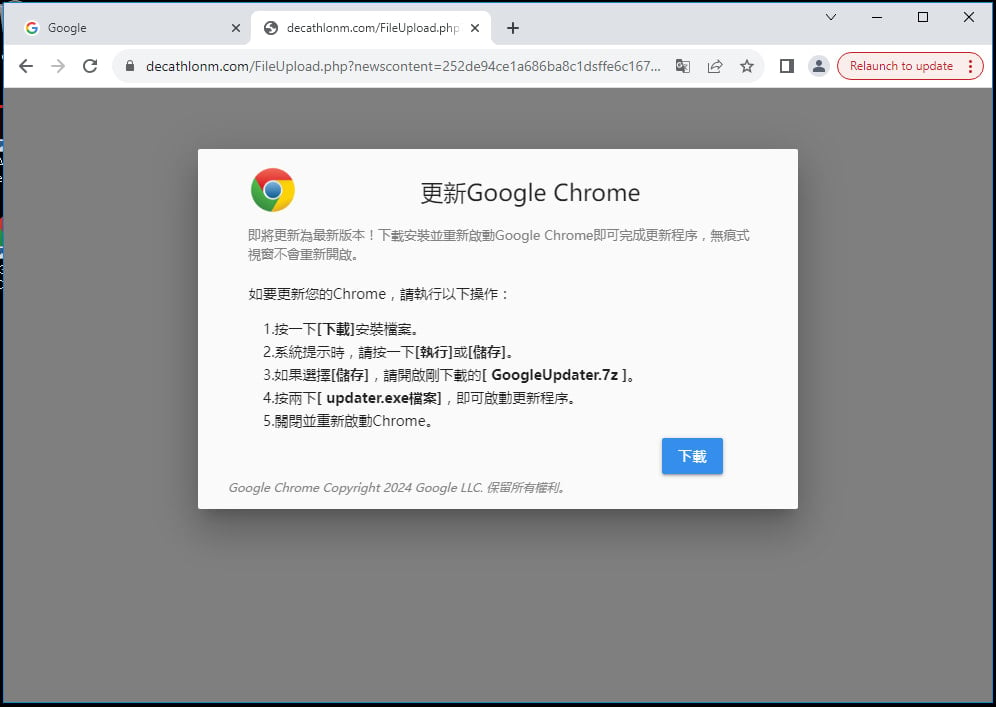
Source: Google
From July 2024, APT24 targeted a digital marketing company in Taiwan, injecting malicious JavaScript into a widely used library distributed by the firm. This tactic allowed the attackers to compromise over 1,000 domains.
Between late 2024 and July 2025, APT24 repeatedly compromised the same marketing firm by injecting obfuscated JavaScript into a modified JSON file, enabling them to fingerprint website visitors and send reports to their server.
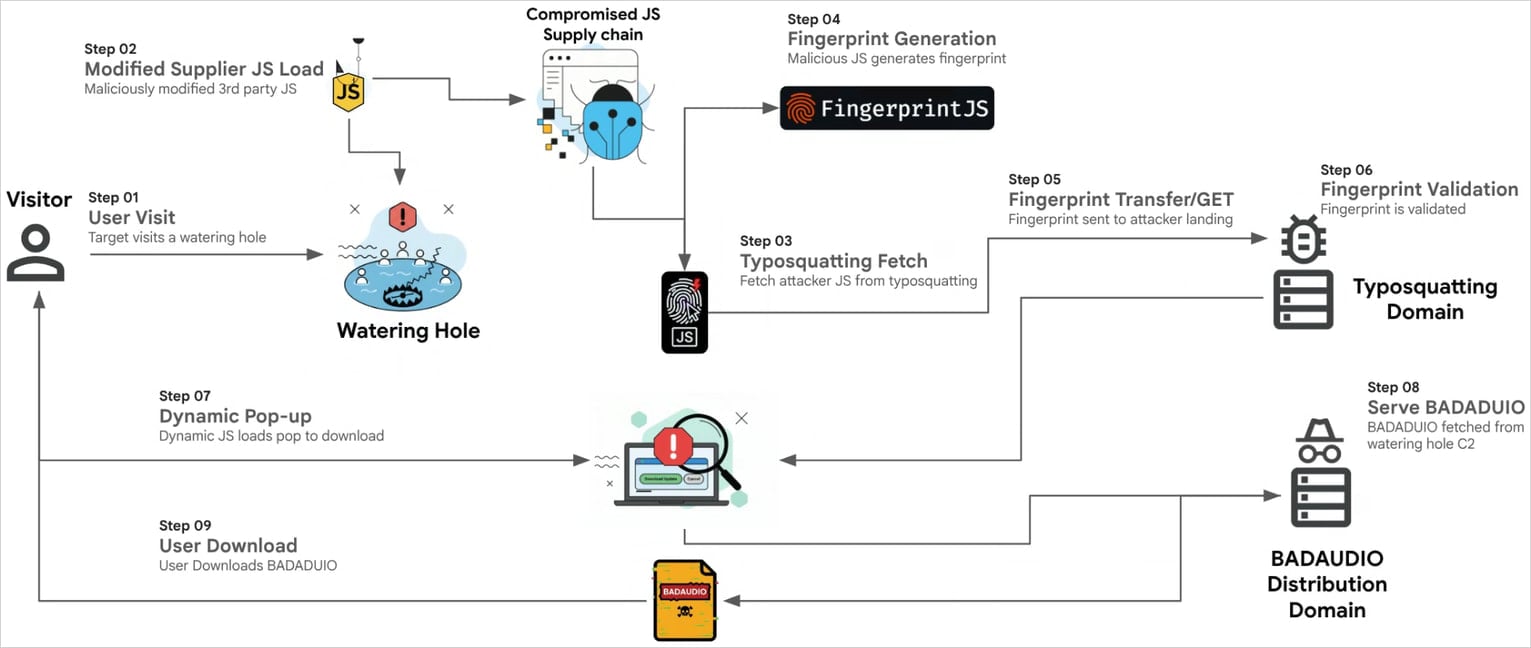
Source: Google
Additionally, starting from August 2024, APT24 initiated spearphishing campaigns using emails impersonating animal rescue organizations to deliver the BadAudio malware. They also utilized cloud services like Google Drive and OneDrive for distribution.
In parallel, APT24 included tracking pixels in emails to monitor recipient engagement, while also focusing on evasive techniques such as DLL search order hijacking to execute BadAudio.
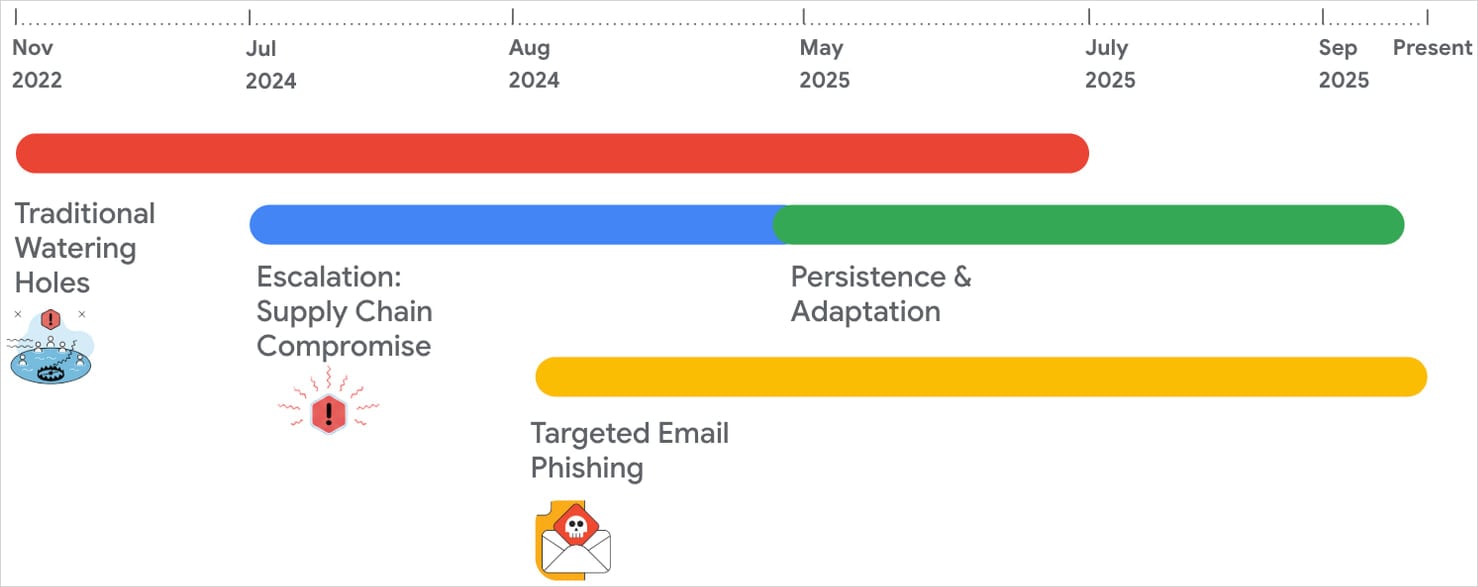
Source: Google
Insights into BadAudio Malware Loader
Google Threat Intelligence Group’s analysis reveals that BadAudio is heavily obfuscated to avoid detection, utilizing techniques like control flow flattening to impede reverse engineering efforts.
Once executed, BadAudio collects system information, encrypts it, and communicates with a command-and-control server to download and execute additional payloads. Google researchers observed instances where the Cobalt Strike Beacon was deployed via BadAudio.
Despite APT24’s use of BadAudio for three years, the malware has remained largely undetected, with only a few samples being flagged as malicious by antivirus engines.
GTIG emphasizes that APT24’s shift towards stealthier attacks reflects the group’s operational capabilities and focus on persistent espionage.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS
































