Security
Urgent Alert: CISA Mandates Patch for Samsung Zero-Day Exploited in Spyware Attacks

CISA Issues Urgent Patch Order for Critical Samsung Vulnerability Exploited in LandFall Spyware Attacks
The Cybersecurity and Infrastructure Security Agency (CISA) has directed U.S. federal agencies to promptly address a critical security flaw in Samsung devices that has been leveraged in zero-day attacks to distribute the dangerous LandFall spyware via WhatsApp.
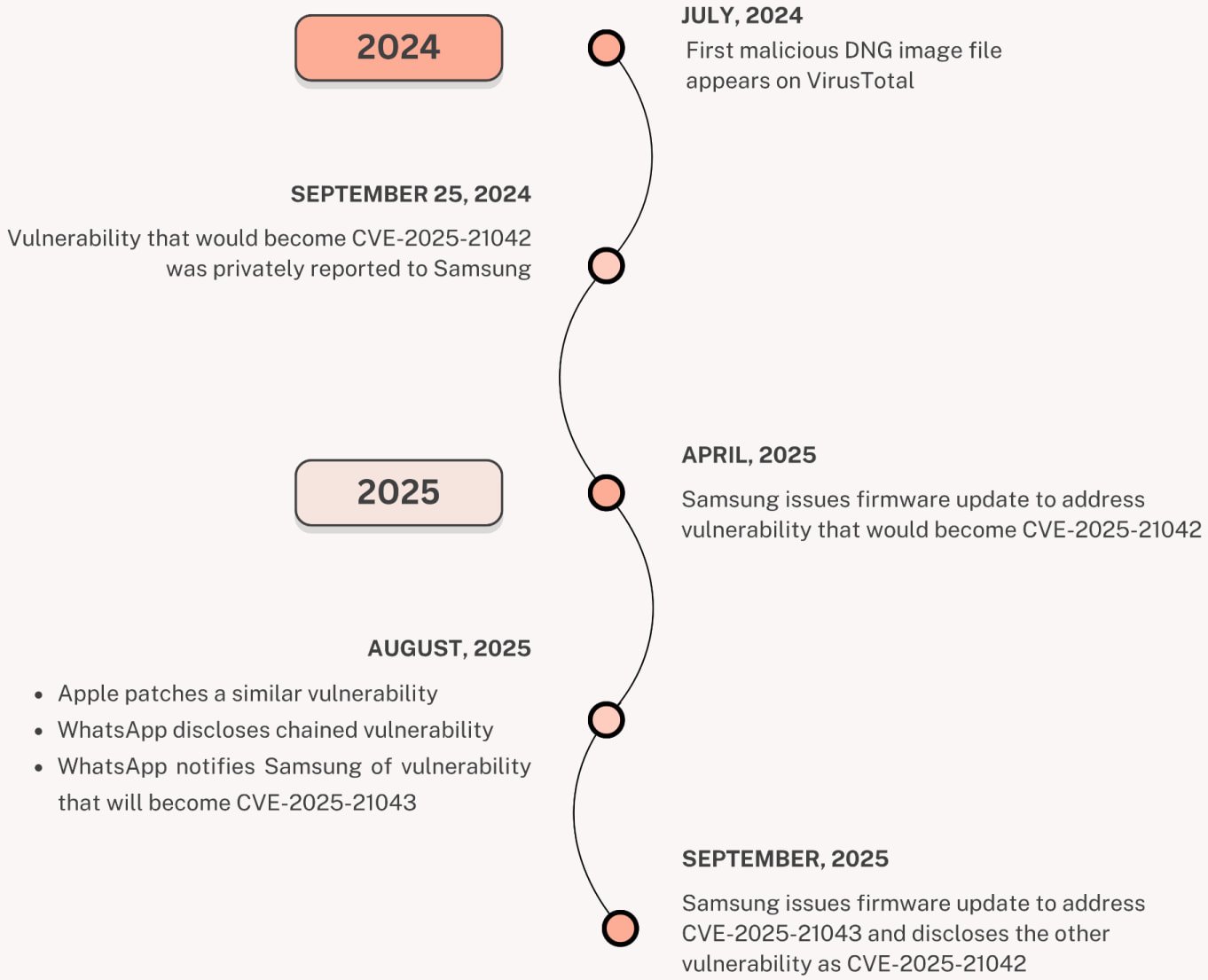
Identified as CVE-2025-21042, this vulnerability in Samsung’s libimagecodec.quram.so library permits remote threat actors to execute malicious code on Android 13 and later versions.
Despite Samsung’s patch release in April, recent findings by Palo Alto Networks’ Unit 42 revealed ongoing exploitation of the flaw since July 2024 to deploy previously unknown LandFall spyware through WhatsApp using malicious DNG images.
The LandFall spyware is capable of invasive actions such as accessing browsing history, recording calls and audio, tracking location, and retrieving photos, contacts, and files.
Unit 42’s analysis indicates that the spyware targets various Samsung flagship models including the Galaxy S22, S23, and S24 series, as well as the Z Fold 4 and Z Flip 4.
Based on VirusTotal samples, potential targets are identified in Iraq, Iran, Turkey, and Morocco. The spyware’s C2 domain infrastructure and registration patterns show similarities to Stealth Falcon operations originating from the United Arab Emirates.
Notably, the spyware’s malware loader component is named “Bridge Head,” a naming convention associated with commercial spyware developed by NSO Group, Variston, Cytrox, and Quadream. However, the direct link to any specific spyware vendor or threat group remains unconfirmed.
CISA has swiftly added the CVE-2025-21042 vulnerability to its Known Exploited Vulnerabilities catalog, mandating Federal Civilian Executive Branch (FCEB) agencies to secure their Samsung devices within three weeks, in accordance with Binding Operational Directive (BOD) 22-01 by December 1.
The directive applies to non-military agencies within the U.S. executive branch, including the Department of Energy, the Department of the Treasury, the Department of Homeland Security, and the Department of Health and Human Services.
While the directive targets federal agencies, CISA advises all organizations to prioritize patching this critical flaw promptly to mitigate potential risks posed by cyber attackers.
“This type of vulnerability is a frequent target for malicious cyber actors and poses substantial risks to the federal enterprise,” CISA cautioned.
It further recommended applying vendor-provided mitigations, adhering to BOD 22-01 guidance for cloud services, or discontinuing product usage if mitigation measures are unavailable.
In a separate effort, Samsung had recently issued security updates to address another vulnerability (CVE-2025-21043) in the libimagecodec.quram.so library exploited in zero-day attacks targeting Android devices.

Amidst budget planning season, over 300 CISOs and security leaders have shared insights on their strategic planning, spending priorities, and emerging trends for the upcoming year. Access this comprehensive report to benchmark strategies, identify trends, and align priorities for 2026.
Discover how top leaders are translating investments into tangible outcomes.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS































