Security
Germany Issues Alert on Signal Account Hacking Targeting High-Level Officials

Germany Warns of State-Sponsored Phishing Attacks Targeting Senior Figures
In a recent development, Germany’s domestic intelligence agency has issued a warning regarding suspected state-sponsored threat actors launching phishing attacks targeting high-ranking individuals through messaging apps like Signal.
These sophisticated attacks combine social engineering tactics with legitimate features to unlawfully obtain data from politicians, military officers, diplomats, and investigative journalists not only in Germany but also across Europe.
The security advisory is based on intelligence gathered by the Federal Office for the Protection of the Constitution (BfV) and the Federal Office for Information Security (BSI).
The agencies emphasize that a key characteristic of these attacks is the absence of malware usage or exploitation of technical vulnerabilities in messaging services.
According to the advisory, the attackers initiate direct contact with the target, posing as either the support team of the messaging service or the support chatbot.
The primary objective is to surreptitiously access one-to-one and group chats as well as contact lists of the affected individuals.
The attacks come in two variations: one involves a complete account takeover, while the other pairs the account with the attacker’s device to monitor chat activities.
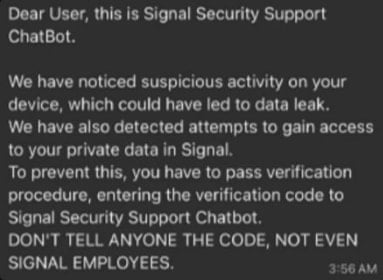
In the first scenario, the attackers masquerade as Signal’s support service and send a fake security alert to induce a sense of urgency.
The target is then deceived into divulging their Signal PIN or an SMS verification code, enabling the attackers to register the account to a device under their control, subsequently hijacking the account and locking out the victim.
Source: BSI
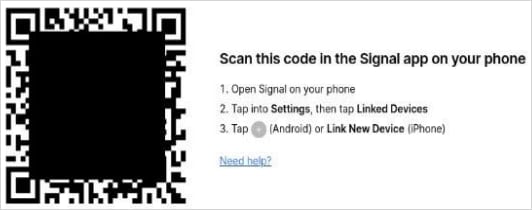
In the second variation, the attacker employs a plausible pretext to persuade the target to scan a QR code, exploiting Signal’s legitimate linked-device feature that allows adding the account to multiple devices.
Consequently, the victim’s account gets paired with a device controlled by the malicious actor, granting access to chats and contacts without raising suspicion.
Source: BSI
While these attacks have been observed on Signal, the advisory cautions that WhatsApp also offers similar functionality and could potentially be exploited in a similar manner.
Previously, Google threat researchers reported the utilization of the QR code pairing technique by Russian state-aligned threat groups like Sandworm.
Ukraine’s Computer Emergency Response Team (CERT-UA) attributed similar attacks to Russian hackers, specifically targeting WhatsApp accounts.
Furthermore, various threat actors, including cybercriminals, have adopted this technique in campaigns such as GhostPairing to compromise accounts for fraudulent activities.
The German authorities advise users to refrain from responding to Signal messages from supposed support accounts, as the messaging platform never initiates direct contact with users.
Instead, recipients of such messages are encouraged to block and report these accounts.
As an additional security measure, Signal users can activate the ‘Registration Lock’ option under Settings > Account. Once enabled, Signal prompts for a personally set PIN whenever someone attempts to register the user’s phone number with the application.
Failure to provide the PIN code results in the registration of the Signal account on another device being unsuccessful. It is crucial to safeguard the PIN, as its loss could lead to a loss of access to the account.
Users are strongly advised to routinely review the list of devices with access to their Signal account under Settings > Linked devices and eliminate any unrecognized devices.

Modern IT infrastructure progresses at a pace faster than manual workflows can keep up with.
Discover in this comprehensive Tines guide how your team can diminish hidden manual delays, enhance reliability through automated responses, and construct and amplify intelligent workflows utilizing tools already in use.
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS