Security
Hidden Threat: The Lumma Stealer and Ninja Browser Malware Campaign Targeting Google Groups
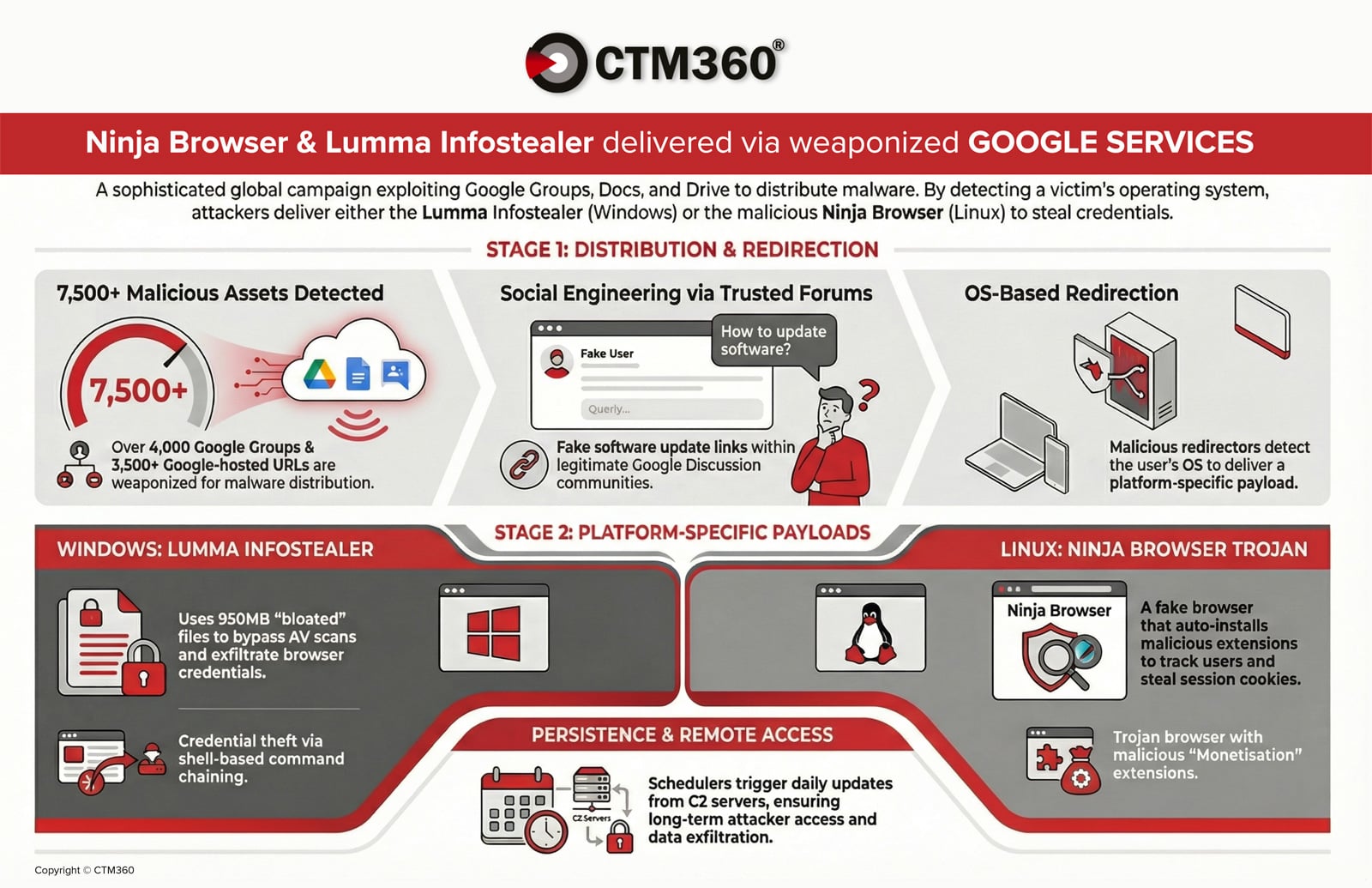
According to CTM360, a recent malware campaign is utilizing over 4,000 malicious Google Groups and 3,500 Google-hosted URLs to target organizations worldwide.
Criminals are exploiting Google’s trusted environment to distribute malware that steals credentials and gains persistent access to compromised devices.
This global activity involves attackers incorporating organization names and industry-specific keywords into posts to enhance credibility and encourage downloads.
For a comprehensive report on the issue, visit: CTM360 Report on Ninja Browser & Lumma Infostealer
Understanding the Malware Campaign
The attack starts with social engineering within Google Groups, where threat actors engage in industry-related discussions that seem legitimate, covering topics like network problems and software configurations.
Within these discussions, attackers include download links disguised as “Download {Organization_Name} for Windows 10.”
To avoid detection, they utilize URL shorteners or Google-hosted redirectors through Docs and Drive. The redirector identifies the victim’s operating system and deploys different payloads based on whether the target is using Windows or Linux.
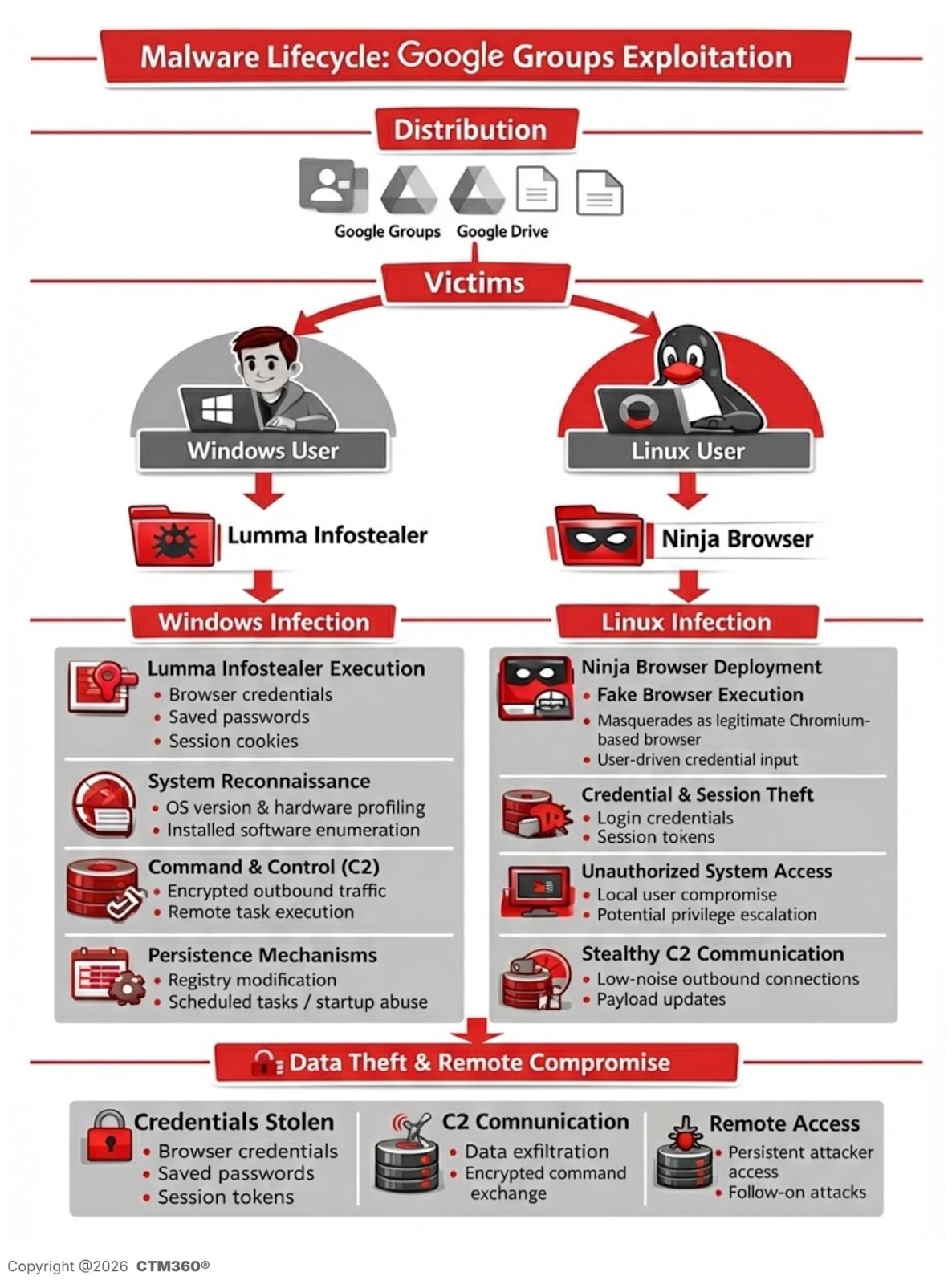
Windows Infection Process: Lumma Info-Stealer
For Windows users, the campaign delivers a password-protected compressed archive hosted on a malicious file-sharing platform.
Use of Oversized Archives to Avoid Detection
The decompressed archive appears to be around 950MB in size, while the actual malicious payload is only about 33MB. Researchers discovered that the executable was filled with null bytes to surpass antivirus file-size scanning thresholds and disrupt static analysis engines.
Execution via AutoIt
Upon execution, the malware:
- Reconstructs segmented binary files.
- Launches an AutoIt-compiled executable.
- Decrypts and runs a memory-resident payload.
This behavior aligns with Lumma Stealer, a commercially available infostealer commonly used in credential-harvesting operations.
Observed activities include:
- Stealing browser credentials.
- Harvesting session cookies.
- Executing shell-based commands.
- Sending HTTP POST requests to C2 infrastructure (e.g., healgeni[.]live).
- Using multipart/form-data POST requests to conceal exfiltrated data.
CTM360 identified numerous IP addresses and SHA-256 hashes associated with the Lumma-stealer payload.
CTM360 has uncovered thousands of deceptive HYIP websites mimicking legitimate crypto and forex trading platforms, luring victims into high-risk investment schemes.
Learn more about the attacker infrastructure, fake compliance signals, and how these scams profit from crypto wallets, cards, and payment gateways. Read the full intelligence report here.
Linux Infection Process: Trojanized “Ninja Browser”
Linux users are directed to download a trojanized Chromium-based browser named “Ninja Browser.”
The software presents itself as a privacy-focused browser with built-in anonymity features.
However, CTM360’s analysis reveals that it silently installs malicious extensions without user consent and implements hidden mechanisms for future compromise by threat actors.
Malicious Extension Functions
An in-built extension called “NinjaBrowserMonetisation” was observed to:
- Track users using unique identifiers.
- Inject scripts into web sessions.
- Load remote content.
- Manipulate browser tabs and cookies.
- Store data externally.
The extension contains heavily obfuscated JavaScript using XOR and Base56-like encoding.
While not immediately activating all embedded domains, the setup indicates potential for future payload deployment.
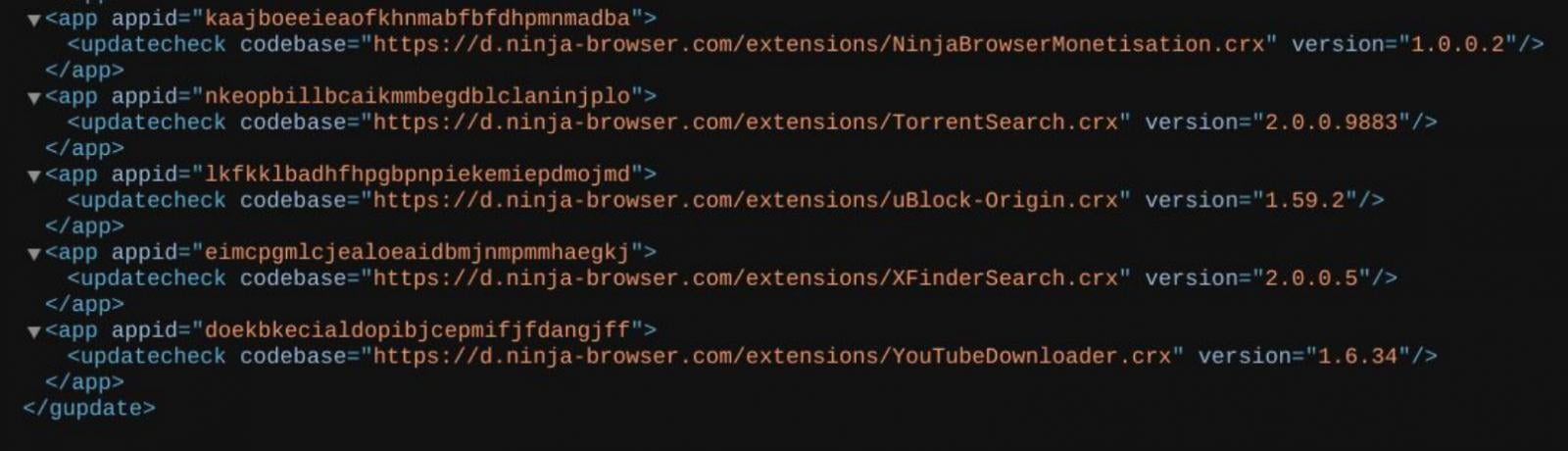
Source: CTM360
Covert Persistence Mechanism
CTM360 also detected scheduled tasks set to:
- Poll attacker-controlled servers daily.
- Quietly install updates without user interaction.
- Maintain long-term persistence.
Furthermore, researchers noted that the browser defaults to a Russian search engine called “X-Finder” and redirects to another suspicious AI-themed search page.
The associated domains include:
- ninja-browser[.]com
- nb-download[.]com
- nbdownload[.]space
Campaign Infrastructure & Indicators of Compromise
CTM360 connected the activity to infrastructure such as:
IPs:
- 152.42.139[.]18
- 89.111.170[.]100
C2 domain:
Multiple SHA-256 hashes and domains linked to credential harvesting and infostealer distribution were identified and are detailed in the report.
Organizational Risks
Risks from Lumma Stealer:
Risks from Ninja Browser:
- Surreptitious credential harvesting.
- Remote command execution.
- Backdoor-like persistence.
- Automatic malicious updates without user consent.
Since the campaign exploits Google services, it evades traditional trust-based filters and boosts user trust in malicious content.
Defensive Strategies
CTM360 recommends organizations to:
- Verify shortened URLs and Google Docs/Drive redirects.
- Block Indicators of Compromise (IoCs) at firewall and EDR levels.
- Caution users against downloading software from unverified sources.
- Monitor endpoint task creations.
- Review browser extension installations.
This campaign underscores a growing trend where attackers utilize trusted SaaS platforms for delivering malware to evade detection.
About the Investigation
The findings are detailed in CTM360’s February 2026 threat intelligence report titled “Ninja Browser & Lumma Infostealer Delivered via Weaponized Google Services.”
CTM360 is actively monitoring this campaign and associated infrastructure.
For the complete report, visit: CTM360 Report on Ninja Browser & Lumma Infostealer
Continuous Cyber Threat Monitoring with CTM360
Enhance your external digital landscape security by monitoring, analyzing, and mitigating risks with CTM360.
Join our Community Edition today.
This content is sponsored and authored by CTM360.
Transform the following sentence into a question:
“He is going to the store.”
Is he going to the store?
-

 Facebook4 months ago
Facebook4 months agoEU Takes Action Against Instagram and Facebook for Violating Illegal Content Rules
-

 Facebook4 months ago
Facebook4 months agoWarning: Facebook Creators Face Monetization Loss for Stealing and Reposting Videos
-

 Facebook4 months ago
Facebook4 months agoFacebook Compliance: ICE-tracking Page Removed After US Government Intervention
-

 Facebook4 months ago
Facebook4 months agoInstaDub: Meta’s AI Translation Tool for Instagram Videos
-

 Facebook2 months ago
Facebook2 months agoFacebook’s New Look: A Blend of Instagram’s Style
-

 Facebook2 months ago
Facebook2 months agoFacebook and Instagram to Reduce Personalized Ads for European Users
-

 Facebook2 months ago
Facebook2 months agoReclaim Your Account: Facebook and Instagram Launch New Hub for Account Recovery
-

 Apple4 months ago
Apple4 months agoMeta discontinues Messenger apps for Windows and macOS